Data is one of the most valuable resources in modern society. Social media and search companies make billions of dollars by gathering information about people and selling it to advertisers.
But it’s not just legitimate companies who see value in your data. Criminals do too. They steal login details so they can get into your accounts and steal information or to extort you. They might also take sensitive work documents and sell them to your rivals. Or, as is increasingly common, criminals often steal large amounts of data in bulk, which they then sell to other criminals on black market sites on the dark web.
Google ‘data breach news’, and you’ll find page after page of real-life cases where data has been taken by thieves. That data could easily include information about you. So how can you tell if your personal data has been leaked, and what should you do if it has? Read on to find out.
Before we start
Data breaches are both a security and a privacy problem, but MacKeeper can help with both. As well as real-time malware protection, it offers an ID Theft Guard feature and a full VPN client. This protects your privacy and encrypts your web traffic. You can try it now, with one free fix for each of its many tools.
How to identify if your personal information has been compromised
If a cybercriminal takes your data with the intention of extorting, then they’ll let you know about it. That could be via an email, a phone call or any other communication method. They might find embarrassing photos or messages and threaten to share them unless you pay a ransom.
In many cases, criminals will steal usernames and passwords, which they’ll either use themselves or sell to others. To them, it’s important that you don’t know your login has been leaked, because they don’t want you to change your password.
Although cybercriminals often try to stay hidden, there are still signs you can check for and ways to see if your details have been stolen:
- Look for unusual activity on your account, like changes in your settings or purchases you don’t remember making.
- In the case of stolen credit and debit cards, criminals might make large withdrawals, possibly clearing out your accounts. Or they might make lots of smaller purchases and withdrawals that you’re less likely to notice.
- If you get a password reset email that you didn’t request, someone could be trying to get into your account.
- You may find you can’t log into an account even though you’re using the right login. This is because hackers may have changed your password to lock you out.
- Enter your details into a data breach protection tool, like Have I Been Pwned. This free tool lets you know if your email address or phone number were involved in known data breaches.
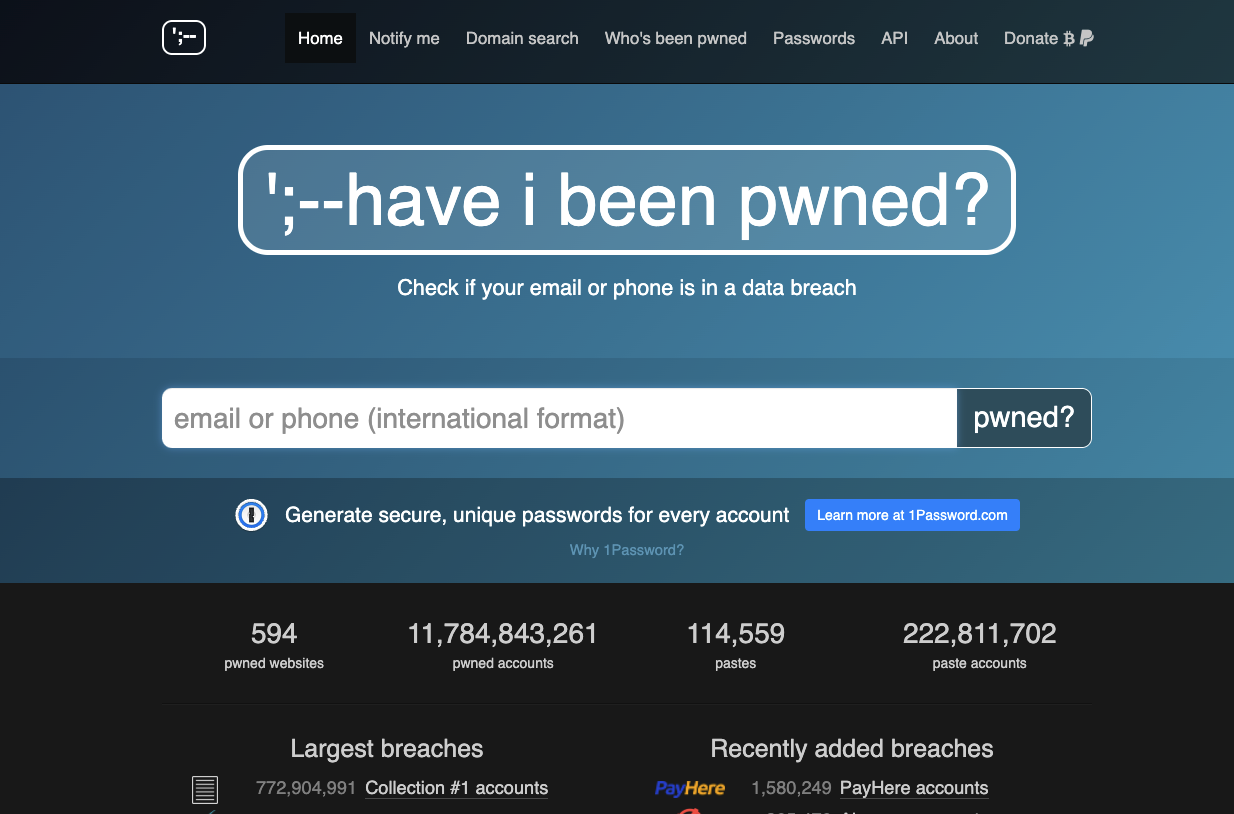
What to do if your data has been stolen
If you do find your data has been taken, it’s not necessarily the end of the world. There’s no way to ‘unleak’ it once it’s out there, but you can take steps to limit the damage and stop it happening again.
Change your passwords
This might seem obvious but it bears repeating. Should you find one of your passwords has been stolen, it’s vital to change it immediately.
There are a few key things to remember when changing your passwords after a data breach:
- Use a strong password, with a mix of number, lowercase and uppercase letters and symbols. You can make it easier for yourself by using a password manager to generate and save your logins
- Change your password anywhere else you’ve used it. Using the same password for more than one account is a terrible idea, because if hackers get your login details for one site, they’ll try them everywhere
- Make sure your computer is malware-free. If criminals have installed a keylogger on your system, they’ll be able to read what you type when you change your password
Let relevant people know about your data leak
It’s not only your data that can be affected if someone has your personal information. For example, if a cybercriminal gets access to your email account, they can access your contacts database. That could give them access to a huge amount of personal information, including email addresses, phone numbers, postal addresses, birthdays and more.
As well as targeting these people too, hackers could use what they find to impersonate you, to extract money or information from your contacts. It’s not usually necessary to tell other people about your data breach, but in some situations it can be a good idea.
Here are some of the people you might want to contact if your personal data is stolen:
- Your bank, so you can block cards and prevent unauthorized transactions
- Family and friends, whose data may also have been stolen. You can also warn them to look out for imposters
- Your boss and colleagues if workplace data has been taken
- Website owners whose sites have been compromised. They may not even know it’s happened
- The police, if you believe a data breach is particularly serious or if sensitive information has been stolen
Run a full virus scan
If a website suffers a data breach, that’s out of your control. But you might also be leaking data because they’re malware on your Mac. You should run a full virus scan to make sure there’s no malware leaking your information to hackers.
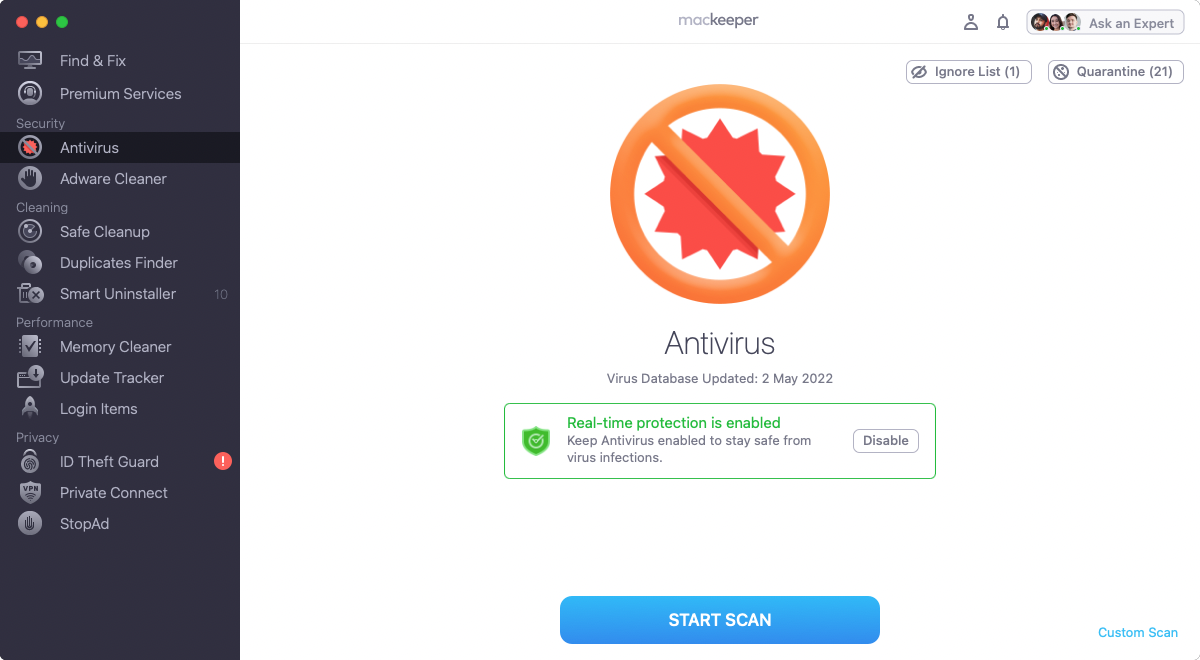
You can run a virus scan with MacKeeper Antivirus in a few easy steps:
1. In MacKeeper, select Antivirus, and click Start scan
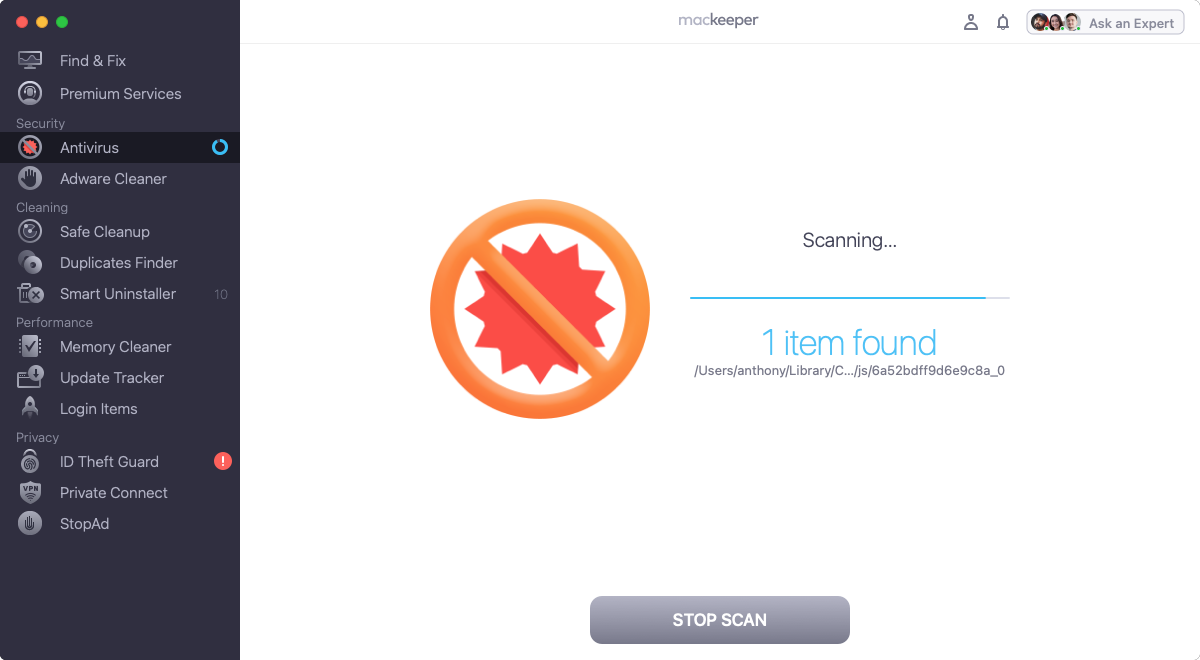
2. Wait while MacKeeper scans your computer
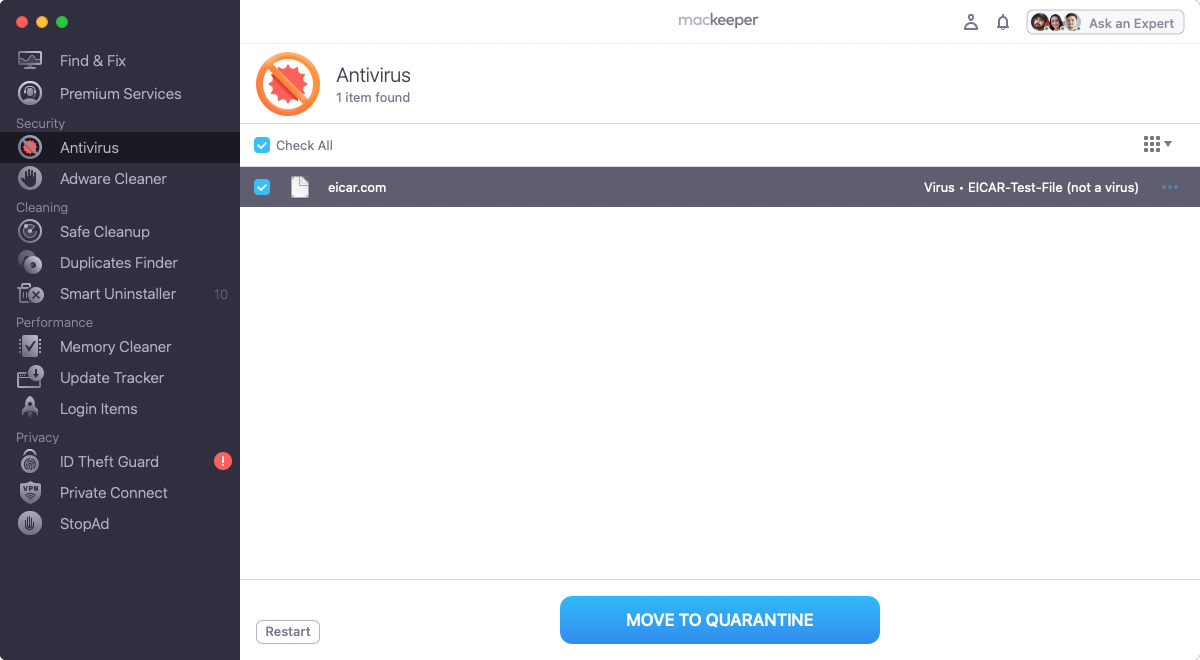
3. When the scan is finished, select any malware that’s found, and click Move to Quarantine
Set up multi-factor authentication
With multi-factor authentication, you log into your accounts with more than just your username and password. Instead there are other ‘factors’ that you need too. This will usually be something that you know or something that you possess.
Common ways to use multi-factor authentication include:
- A temporary, one-time password or PIN. This may be sent to you as a text message or an email, or through a dedicated app like Google Authenticator
- A pop-up on your phone, which requires you to confirm you’re trying to log into an account on another device
- Biometric authentication measures like fingerprint scans, face recognition and voice recognition
- A physical authentication device, such as a YubiKey, which your phone or computer reads via USB or near-field communication (NFC)
Set up data breach protection
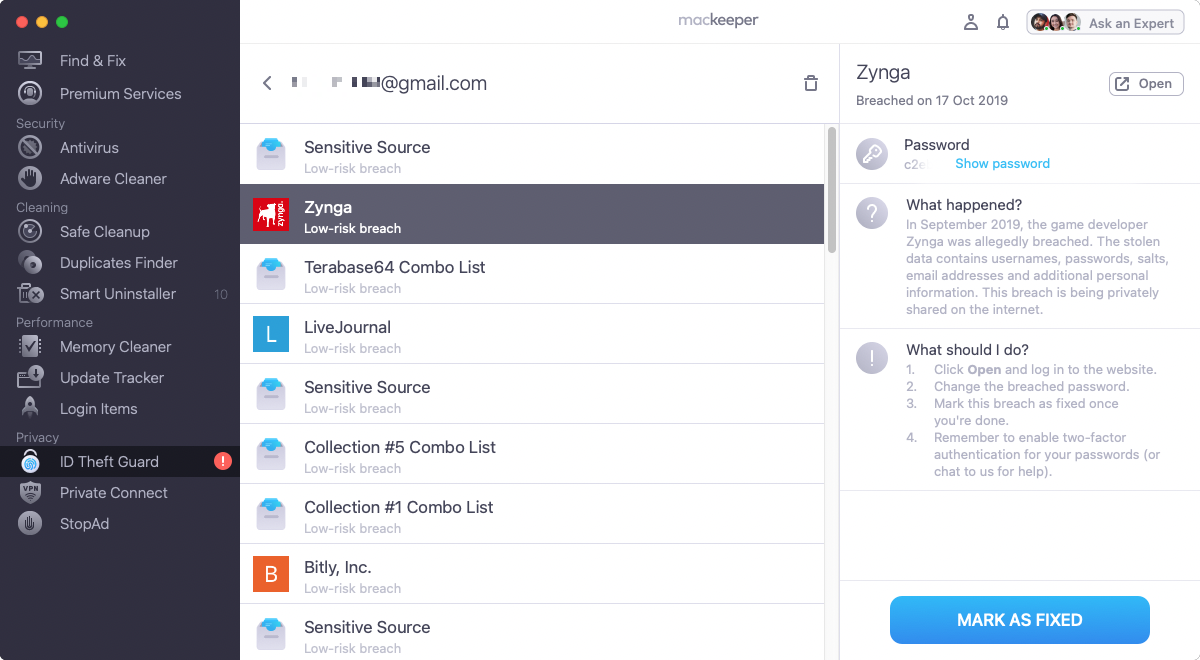
It’s impractical to keep checking if your personal data has been stolen. Luckily, you don’t have to. With MacKeeper, you can simply enter your email addresses, and it will let you know if they’re found in known data breaches.
Here’s how to set up MacKeeper’s ID Theft Guard feature:
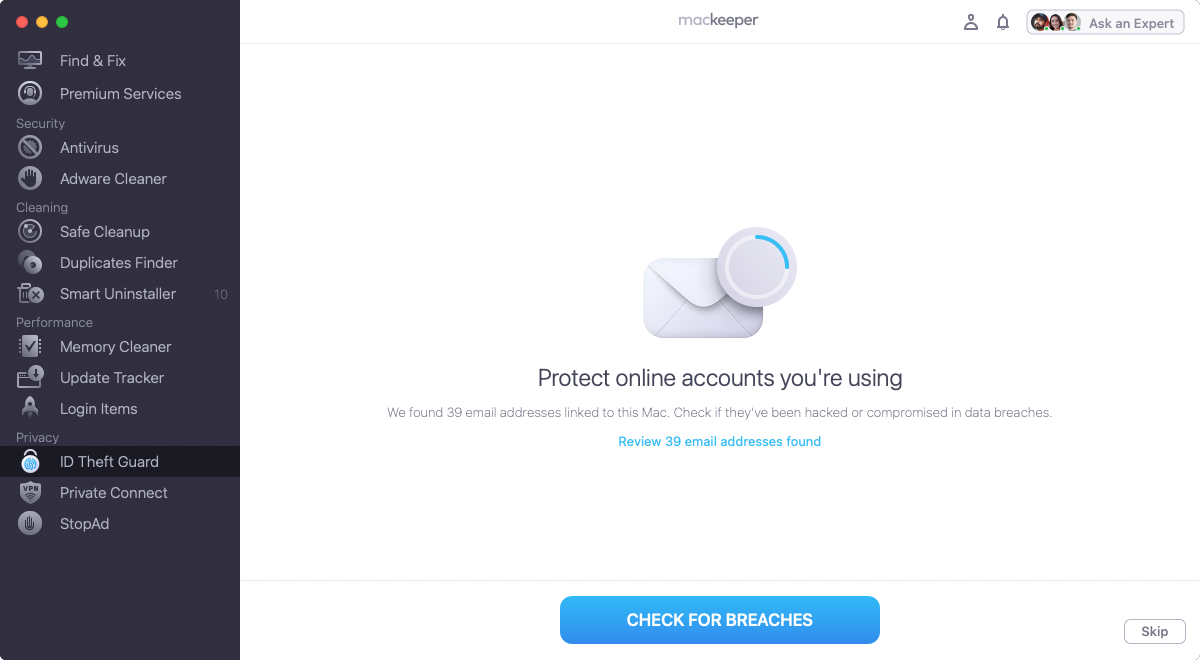
1. Open MacKeeper, and select ID Theft Guard from the sidebar
2. MacKeeper will automatically find email addresses linked to your Mac. Click Check for Breaches
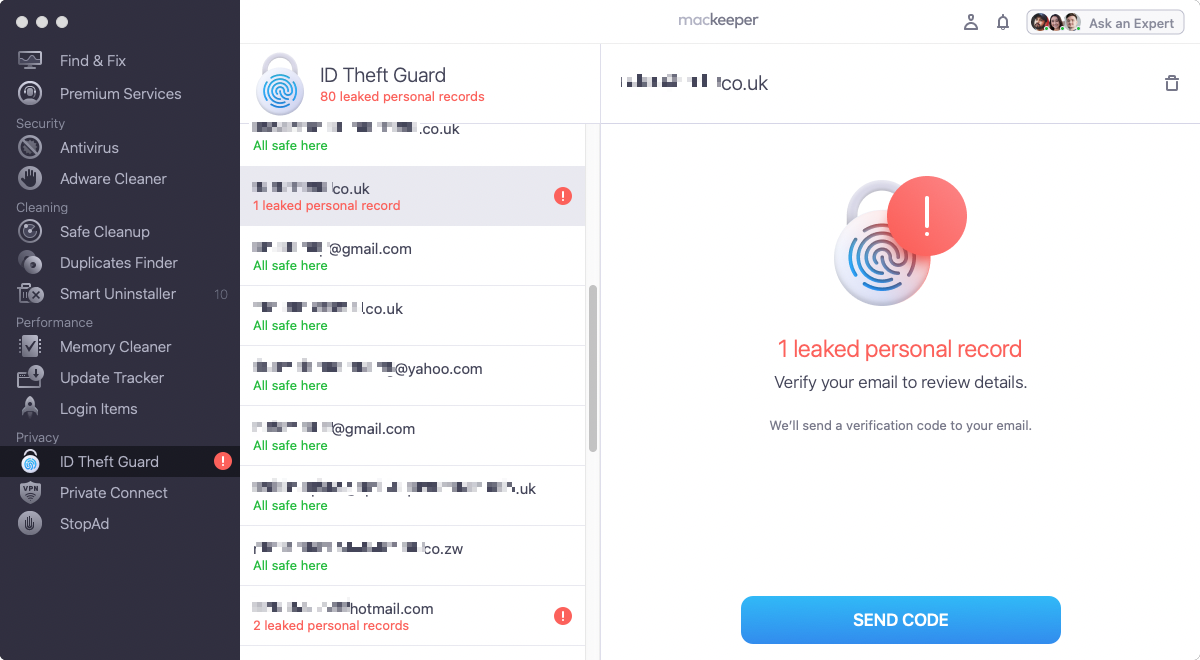
3. If you see an address that’s not yours, select it, and click the trash icon

4. You can also verify new addresses by clicking the Send code button
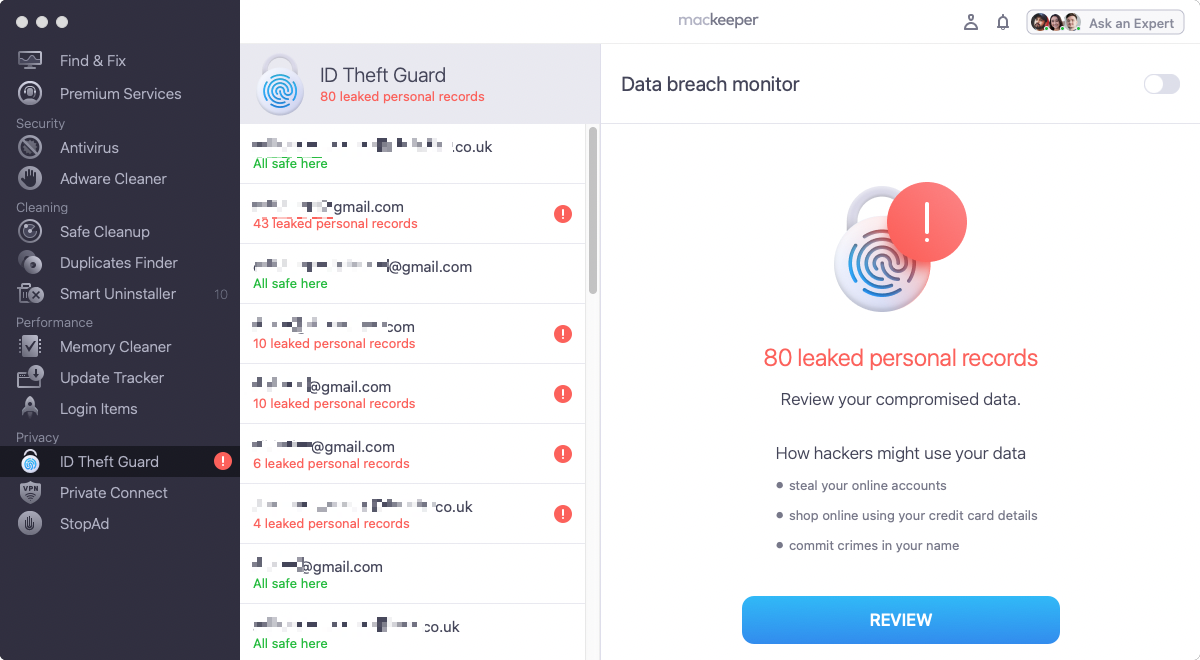
5. Once accounts are verified, you can see if an address has been compromised. Look through the results and take the recommended actions
6. Click Mark as fixed when done
Can you stop your data from being stolen?
In a word, no. If you want to buy things from the internet, use online banking or talk to people on social media, you’ll have to hand over personal details. As soon as you give your data to a third party, it’s their responsibility to take care of it and protect it. Unfortunately, there’s no way to guarantee that’s happening, and some website owners end up doing stupid things like storing passwords in unencrypted text documents.
While you can’t prevent these things happening, you can improve your chances of keeping your data safe. Follow best practices for protecting your online privacy and securing your Mac. Don’t download files from websites you don’t trust or email attachments from people you don’t know. These kinds of measures will reduce the chance that you’ll end up getting malware that steals your data.
With the right mix of precautions and awareness, you can stop data breaches turning into much bigger problems.
Read more: