Before we start
With online scammers getting more creative every day, you also need to be more attentive to your data privacy and security. VPNs, antiviruses, and other protective tools may become your greatest allies in these cases.
Get MacKeeper and let it take care of your Mac privacy and security. The ID Theft Guard, VPN, and StopAD app features help you keep your data private and provide a powerful antivirus and adware cleaner to secure your Mac from malware and viruses.
What are some of the myths about hackers?
- They always wear masks
- They work in complete darkness
- They type with enormous speed

You know the type, right? But doesn’t it seem unrealistic to you?
How about some true facts about hackers?
- Together, they earn around $1.5 trillion per year
- They’re armed with advanced technical tools that automate part of their work
- When they start an attack, they can reach their goals shockingly quickly
Data breaches occur literally every day, proving that cyberattackers are skilled at their craft. Being speedy and well-armed actually helps them wreck businesses and governments with alarming efficiency. In contrast, even prosperous and firmly established companies often react dreadfully slowly to cyberattacks.
But, how do hackers work and how can you protect yourself against cyberattacks?
How long does it take a hacker to perform a cyberattack?
IT security specialists have been long studying cyberattacks to understand how to employ protection at each stage of the intrusion. It appears that different types of cyberattacks, from DDoS attacks or malware injection to data theft have common phases. In 2011, Lockheed Martin summarized the stages of a cyberattack in a model called the Cyber Kill Chain. Later, other security organizations suggested their own models for the attack lifecycle.
We won’t try to describe all the various schemes used by professionals. Instead, here’s a cyberattack timeline explained in simple words.
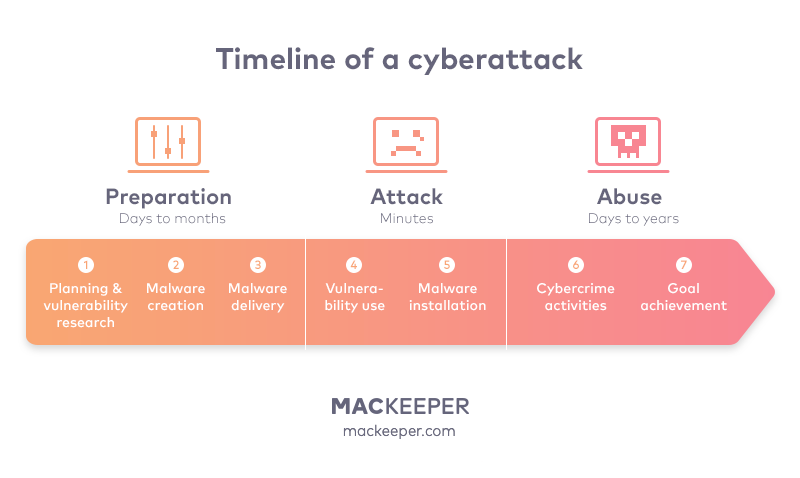
So, how long does it take to perform a cyberattack?
1. Hacker preparation for a cyberattack—days to months
This stage is rather time-consuming for the intruders. In order to reach their goal, they have to find a weak spot in their target, think out how they will act, and cover their attack.
For example, hackers may want to use a social engineering path and swindle a corporate login and a password from an employee. For this reason, they’ll research a company’s structure, email addresses, and operational facts. Based on this information, the attacker will be able to impersonate a corporate IT specialist and request employee credentials via a fake email.
Alternatively, cybercriminals may look for software or hardware vulnerabilities, like what happened in the WhatsApp hack story. Often, to find vulnerabilities in applications, web services, or operation systems, hackers use automated tools. For instance, they may use crawlers—programs that work with search engines to find unprotected data stored on the web. Automated vulnerability search tools accelerate attacks significantly.
Next, cybercriminals work on creating their own malicious program or choosing a readily available one to fit their goal best. Eventually, they find a way to deliver the malware to the target—through an email, a legitimate-looking program, a “forgotten” USB key, or in some other way.
2. The cyberattack itself—minutes
Attacking a vulnerability with a proper technical tool, such as malware, lets hackers gain access to the victim and take hold. This process is rapid. It takes mere minutes.
Let’s have a look at some practical figures. A recent study was focused on the speed of action in the main attack phase—a breakout—from the time of initial breach to time of exploring other computers and devices in the network. Russian hackers are the fastest, being able to break out in about 18 minutes on average.
All in all, if an attack is successful, it’s nearly impossible to repel it immediately or fix the harm completely. This is why prevention is key for both security specialists and individuals.
3. Abuse of the invaded resource—days to years
At this stage, the hackers may exploit the target stealthily for as long as needed or until the breach is revealed and fixed.
If the attackers hunt for data, they can use their crawler tool to check the accessed data, identify if it’s encrypted, and dump some of it to see whether it’s what they need. If the data is valuable, the hackers start downloading it.
Data downloading speed depends on the connection capacity of both the hacker and the target. Sometimes, cybercriminals deliberately slow down their activities to continue unnoticed. Experts say that the 143 million customer records stolen in an Equifax data breach were downloaded within a period from one to 38 days.
The picture may differ depending on the type of a cyberattack. For example, in a ransomware attack, cybercriminals make their invasion visible right away. They block access to a computer system and threaten to delete all the data stored inside unless a ransom is paid. In this case, the adversaries often set a short deadline to compel the victim to act.
How we set bait for hackers and tested their speed
One of the most common problems that companies experience happens when they place unprotected databases online. Usually, due to human error, large storages of sensitive data appear searchable and accessible to hackers. The result may be catastrophic as billions of records can be leaked in a data breach.
Interestingly, it’s quite easy to simulate an unprotected database and see how attackers would react. Professionals call these fake databases “honeypots” as they are irresistibly attractive to cybercrooks.
Curious about checking all security-related questions in practice, we couldn’t resist creating our own honeypot. We created a fake open database and placed it online. It was a MongoDB database, like those commonly used by different organizations. In just 10 days, our bait was found and attacked. The entire compromise took only 13 seconds to be completed.
Using automated tools, hackers found our database, connected to it, simulated data theft, and left a ransom note. They demanded 0.2 bitcoin for information recovery. In fact, we could see that our fabricated database was in fact deleted, not stolen, so the deal was even more sinister. We also checked whether these attackers received ransom payments from other victims but luckily they hadn’t.
What we learnt from this experiment is that unprotected databases are easily found by cybercriminals and are rapidly intercepted. For a business, this means that careless treatment of data will inevitably bring trouble.
How long does password cracking take?
Just like businesses, users have to take care of their data. Otherwise, they’ll likely be hacked quickly and irreversibly.
The easiest and most obvious way to protect yourself online is to use strong and unique passwords on your accounts. By the way, it’s now possible to automatically check how quickly a certain password can be hacked.
Let’s do another experiment right now.
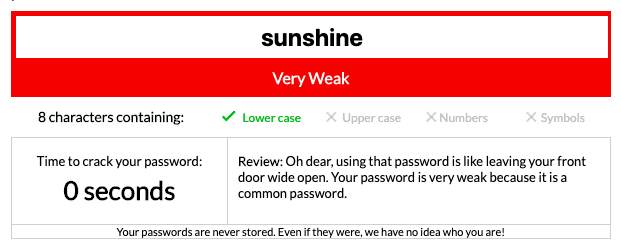
First, let’s test a tragically weak password. We’ll take “sunshine,” entry #8 in the 2018 list of most popular passwords.
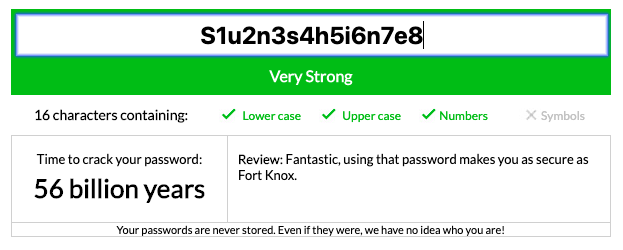
Now, what if we just add numbers after each letter? The word gets twice longer and no one would find it in a dictionary. It would take a password cracker 56 billion years to hack this password.
There are numerous other practices for staying well-protected with passwords such as:
- Use long passphrases with made-up or misspelled words in them
- Take unique passwords for each of your accounts
- Change your passwords regularly (at least quarterly)
Robust antivirus software and VPN services can also help to protect your privacy online.
***
Numerous examples prove how quickly cyberattacks can take place. In a world where it takes companies over 6 months just to detect a data breach, everyone should pay attention to and care for their security personally.
At MacKeeper, we want to make security control easy and seamless for you. ID Theft Guard, a new tool within MacKeeper regularly checks any accounts linked to an email you provide. If your data is ever compromised and made public online, you’ll get immediate alerts. This way, you will be able to act quickly and protect yourself from further troubles. Give it a try and see how convenient it is!