In this post, we’ve gathered 6 breaches that occurred in 2018. The research was conducted by Chris Vickery — a data breach hunter, who collaborated with MacKeeper to publish security and data breaches reports on the MacKeeper blog.
This is the third blog post in a series of data breach reports. Make sure to read the 2016 Data Breach Reports Archive and the 2017 Data Breach Reports Archive.
Click on a data leak name to read the report:
- FedEx customer records exposed
- Tens of thousands of vulnerable MongoDB servers
- Cryptocurrency leaks personal information on thousands of investors
- Honda Car India leaks customer data
- Docker Hub’s cryptojacking infection
- A money-laundering database breach
Essential reading and tools:
- Mac security guide will tell you all about macOS security settings
- Mac antivirus will run smoothly on your Mac guarding it in real-time
- VPN for Mac will connect you securely every time you use the internet
- Malware Removal Guide for Mac Owners will show you how to remove different kinds of malware
- How to Check Your Mac for Malware guide will show you how to detect and remove malware from your Mac
- Have I Been Pwnd service will check your emails for data breaches
FedEx customer records exposed
In February 2018, Chris Vickery stumbled upon a publically available Amazon S3 bucket, belonging to Bongo International LLC.
The exposed bucket contained more than 119 thousand scanned documents of US and foreign citizens, such as passports, driving licenses, and security IDs, among others. The IDs were accompanied by scanned "Applications for Delivery of Mail Through Agent" forms (PS Form 1583), which also contained names, home addresses, phone numbers, and ZIP codes.
In 2014, FedEx Corp. bought Bongo International and relaunched it as FedEx Cross-Border International. The service was shut down three years later. However, the data inherited from Bongo International LLC services from the 2009-2012 era remained publicly available.
On February 13th, after effortless attempts to get in touch with FedEx via FedEx Cross Border Merchant Customer Support line and emails, Vickery requested the assistance of ZDNet reporter, Zack Whittaker. Shortly after, the company confirmed its connection to the data and reassured Zack that none of it had been misappropriated. Read Zach’s take on the story at ZDnet.
A lesson to learn
The acquisition of Bongo International LLC and its subsequent data breach, highlight the importance of proper data management before, during, and after the sale.
When a company is being acquired, it is obliged to notify the customers about the acquisition and the transfer of their data to a new owner. The acquiring company should send the customers a data protection notice and allow them to opt-out of the data transfer. Furthermore, the acquiring company should use the opportunity to identify any security and data privacy risks during the integration or migration stage of the purchase.
If you worry about your data being exposed by this or any other cybersecurity incident, learn how to act after a data breach.
Tens of thousands of vulnerable MongoDB servers
In March 2018, MacKeeper’s experts tested the security of MongoDB, a popular NoSQL database commonly misconfigured for public access. A honeypot or fake database setup created by the researchers was attacked by an automated script from a Chinese IP address. The compromise was completed in just 13 seconds.
The MacKeeper’s experts took the following steps to create the honeypot database:
- Deployed Splunk on EC2 instance with 30 GB storage.
- Configured location dashboard with locations of hosts that attempted to connect to the Honeypot.
- Configured Top 25 IP dashboard with Top 25 IP addresses by the count of connections.
- Configured indexes for storing and accessing all collected data.
- Deployed MongoDB version 2.6.10 on EC2 instance with 30GB storage.
- Deployed MongoDB Monitoring Splunk App for log forwarding of MongoDB logs.
- Configured MongoDB for maximal verbosity of authentication logs and interactions logs.
- Deployed Splunk forwarder and Splunk Linux Auditd for auditd logs.
- Generated and uploaded a fake dataset into 2 databases on MongoDB: ***_prod, ***_dev.
- Backed up MongoDB Honeypot for recovery after a ransomware attack.
- Opened MongoDB for all TCP connections on 27017 port (typical misconfigured MongoDB)
After accessing the honeypot, the script deleted the Journals and created a database called Warning with Readme collection and the Solution record. Then, it left the following ransomware message for the database owners:
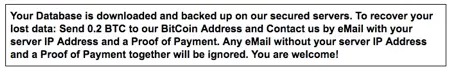
A lesson to learn
Although no data was lost in the breach of the test database, tens of thousands of real MongoDB databases are still vulnerable to cyberattacks. To address the issue the company has updated its software with secure defaults and released security guidelines. Nevertheless, there are approximately 54,000 databases that haven’t been secured yet.
To improve your cybersecurity, learn how to protect yourself against data breaches.
Cryptocurrency leaks personal information on thousands of investors
In March 2018, MacKeeper’s researchers discovered a publicly available database operated by a cryptocurrency company, Bezop. The database contained full names, addresses, email addresses, encrypted passwords, wallet information, along with links to scanned passports, driver's licenses, and other IDs of over 25,000 owners of the cryptocurrency.
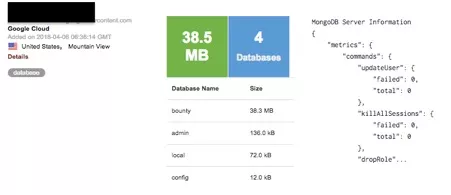
The transaction and cryptocurrency side of Bezop was built around Ethereum, an open blockchain technology allowing developers to easily design distributed systems for creating cryptocurrency and managing transactions. The front end store side of Bezop's system was reportedly based on HTML5, React JS, Node Js, and MongoDB.
Although the MongoDB vulnerabilities are well known, it’s difficult to grasp how the data exposure could happen by mistake. The database could have only been configured to public access deliberately, which is a giant cybersecurity risk.
A lesson to learn
Bezop survived the bumpy opening and it is still operational. We hope that the data breach has taught the company a valuable lesson on the security vulnerabilities of Mongo databases. Let’s also hope that the company has realized that no matter how hectic a development cycle is, convenience should never be prioritized over security.
Honda Car India leaks customer data
In 2018, MacKeeper’s experts discovered two unsecured Amazon AWS S3 buckets belonging to Honda Car India. The buckets stored databases with personal information of more than 50,000 users of the company’s Honda Connect App.
The exposed information included names, phone numbers and email addresses of both users and their trusted contacts, passwords, genders, and information about users’ vehicles.
Upon closer examination of the S3 buckets, MacKeeper’s researchers realized that it had been accessed at least once before by security researcher @Random_Robbie (twitter), who left the following note.
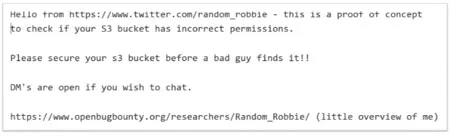
Astoundingly, the company didn't notice the note’s presence in its bucket, which indicated the lack of monitoring on its part.
The leaked information could have been used by the cybercriminals to launch targeted phishing attacks. It would not be too difficult to email or text a malicious link seemingly coming from a trusted source to access a victim’s device. To minimize your exposure to similar attacks, learn how to protect your privacy online.
A lesson to learn
With the sheer volume of coverage of leaky S3 buckets, it's astounding that they are still regularly discovered by MacKeeper’s experts. It shows that many companies of all sizes are still not paying enough attention to their cybersecurity. The case in point is Honda Car India that didn't notice the presence of the researcher’s note in its bucket, which indicated the lack of monitoring on its part.
The companies neglecting to improve their cybersecurity stance put at risk not only their reputation but also their customers’ privacy and even livelihood. Given the severe consequences of data breaches, there’s no place for loose cybersecurity in our increasingly interconnected world.
Docker Hub’s cryptojacking infection
In 2018, cybersecurity experts from MacKeeper discovered 17 malicious docker images stored on a repository service, Docker Hub, for a year.
The docker images were used by cybercriminals to infect the victim’s devices with cryptocurrency mining malware, which is a crime referred to as cryptojacking. It is estimated that the illegal practice allowed the cybercriminals to mine $90,000 worth of Monero cryptocurrency.
The cybercriminals presumably followed these steps to launch the cyberattack:
- Automized target collection using Shodan, Censys or Zoomeye.
- Infiltrated vulnerable or misconfigured Docker registries or Kubernetes instances.
- Exploited weak default settings and injected mining malware within containers.
- Automatically collected targets and exploiting them as C2 server hosts using AutoSploit or similar software.
Ericsson’s Head of Cloud Jason Hoffman attributes Docker’s rapid adoption to its package management. Although undeniably true, it’s worth noting that Docker images are generally dependent on the package manager provided by an underlying Linux distribution. Images such as CentOS 5.11 are deliberately held back for the sake of compatibility and their Shellshock vulnerability.
Additional insight into the issue is offered by engineer Ross Fairbanks who states that the Docker containers run as root by default. It means that a compromised container makes possible the root access to the host itself.
A lesson to learn
Pulling a Docker image from Docker Hub is akin to downloading an unknown binary file, executing it, and hoping for the best.
To minimize the risk of cryptojacking, it’s important to improve the traceability of the Docker images. At the same time, internal and external communication within Kubernetes cluster should also be secured. To this end, do the following:
- Don’t access Kubernetes clusters via the internet.kubelet
- Use SSH tunnels to send packets via the cluster's network without exposing the Kubelet's webserver to the Internet.
- Ensure that kubelet serves its https endpoint with a certificate that is signed by the cluster CA.
A money-laundering database breach
In June 2018, MacKeeper’s researchers stumbled across an unsecured database maintained by cybercriminals who used stolen credit cards and free-to-play apps for money laundering.
The cybercriminals processed almost 20,000 stolen credit cards in just 1.5 months. The following image offers a simplified view of the criminal scheme.
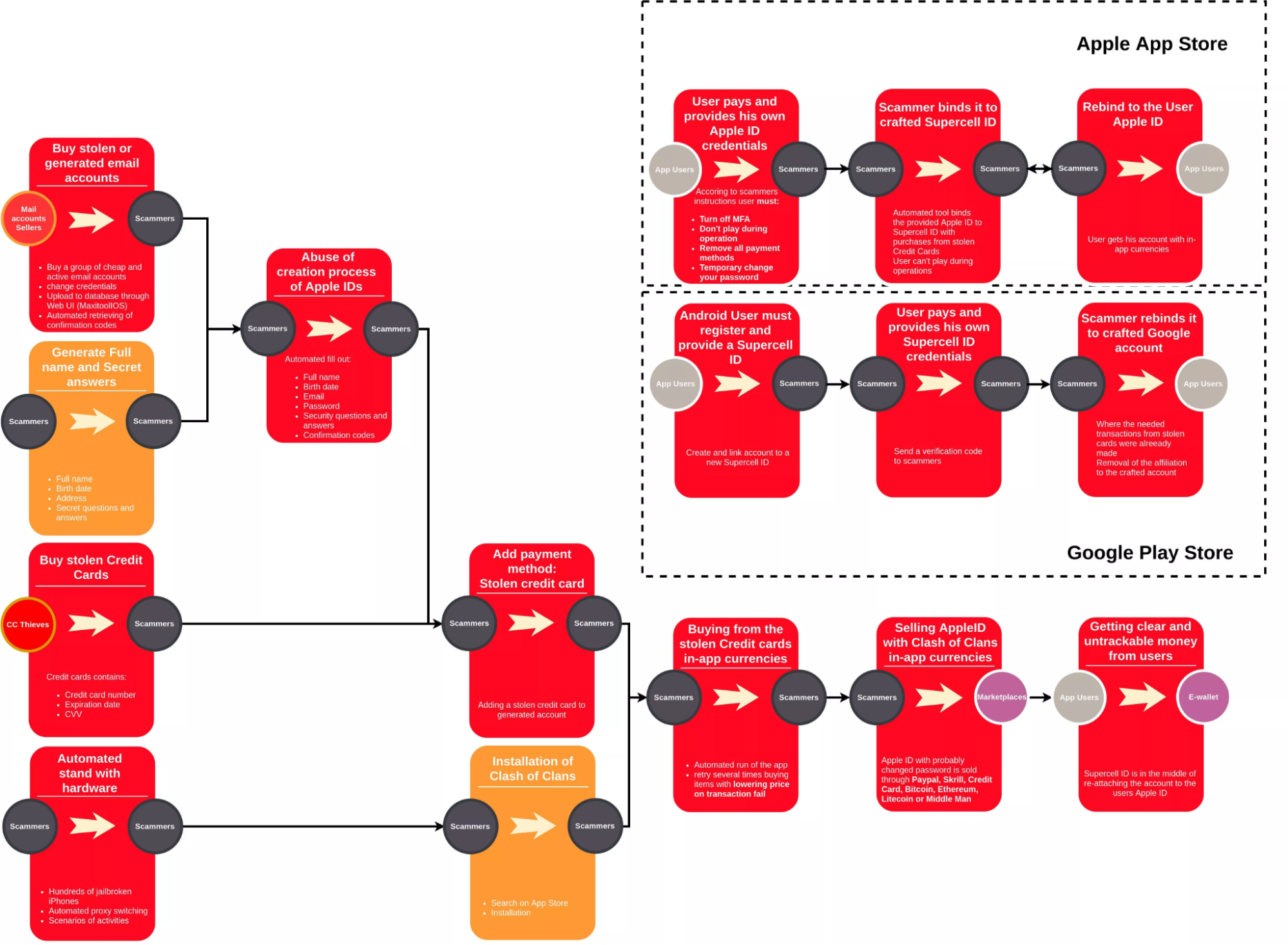
The criminal scheme revolved around the use of Apple IDs and just three games: Clash of Clans, Clash Royale, and Marvel Contest of Champions. Given that the aggregate annual revenue of the games exceeded $330 million, they were perfect targets for money laundering. To facilitate the process of in-game currency generation, the cybercriminals used automated bots created by the games’ fans.
A lesson to learn
It seems that the cybercriminals managed to pull off a daring crime because of Apple’s lax credit card verification process. In the same vein, email service providers also did not do enough to protect against this kind of abuse. Finally, the money-laundering scheme wouldn’t be possible if game developers did a better job of enforcing their in-game currency trading policies.
Read more: