How MacKeeper works

1. Run one-click scan
Get a bird’s eye view of your Mac’s storage, performance and security..

2. Fix items found
Review and fix items affecting your Mac experience in just a few clicks.

3. Enjoy a worry-free Mac
Let MacKeeper take care of your Mac—it’ll notify you if any action is needed.
Why MacKeeper is the ultimate choice
Cleaning
Get total Mac junk cleanup to free up gigabytes of storage. You can teach an old Mac new tricks.
-
Safe Cleanup
Get rid of junk files, unneeded mail attachments, and trash on your Mac.
-
Duplicates Finder
Find and delete duplicate files, which take up extra space.
-
Smart Uninstaller
Uninstall unneeded apps, widgets, plugins, and browser extensions.
Performance
Unleash the full power of your Mac. This is what real memory, startup, and performance optimization feels like.
-
Memory Cleaner
Manage your Mac’s memory for a smoother performance.
-
Update Tracker
Keep your apps up to date to ensure you have the latest security updates.
-
Login Items
Reduce your Mac startup time by reviewing and disabling apps that overload the system.
Privacy & Security
No matter the threat, we’ve got your back. MacKeeper protects your Mac from viruses and adware as well as guarding your data from online identity theft.
-
Antivirus
Protect your Mac from malware with real-time protection.
-
Adware Cleaner
Find and delete malicious apps that annoy you with ads, quickly and effortlessly.
-
ID Theft Guard
Check and monitor your personal data for data breaches with instant alerts.
-
VPN Private Connect
Browse securely with an anonymous internet connection.
-
StopAd
Enjoy ad-free web browsing and searching with a smart browser extension.
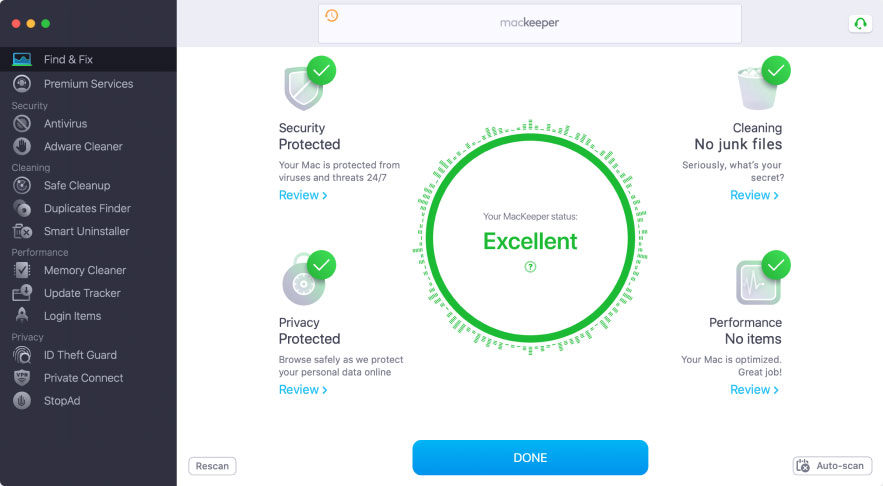
Check your Mac with one click
You can perform the diagnostics on your Mac with a single click. Voila—see what’s clogging up your device, what’s slowing down its performance, and all its security and privacy vulnerabilities. It couldn’t be easier!
Why customers love MacKeeper
Get premium help with any software-related issues
Sometimes it feels like devices get more sophisticated and more complex by the day. Setting them up and fixing them may seem daunting at times. Our tech crew can help with any software-related issues. By call or chat. 24/7.
add-on
