Worldwide studies from 2019 and 2020 have shown a massive increase in cybercrime. A report by Accenture states that security breaches increased by 67% from 2014-2019. It’s highly likely that educational institutions — relatively easy targets — have been attacked as well.
And they might not even know it. A 2020 report by IBM reported that it took about 280 days (on average) to identify a breach.
The situation is even more critical due to the COVID-19 pandemic, with educational institutions relying on remote learning more and more. The FBI reported a 300% increase in cybercrimes in the first half of 2020, from about 1,000 cases a day, to between 3,000 and 4,000.
A report carried out by Microsoft appears to indicate that educational institutions are the worst affected. The education sector reported over 6 million “malware encounters” in the first 30 days of 2021. Shocking, isn’t it?
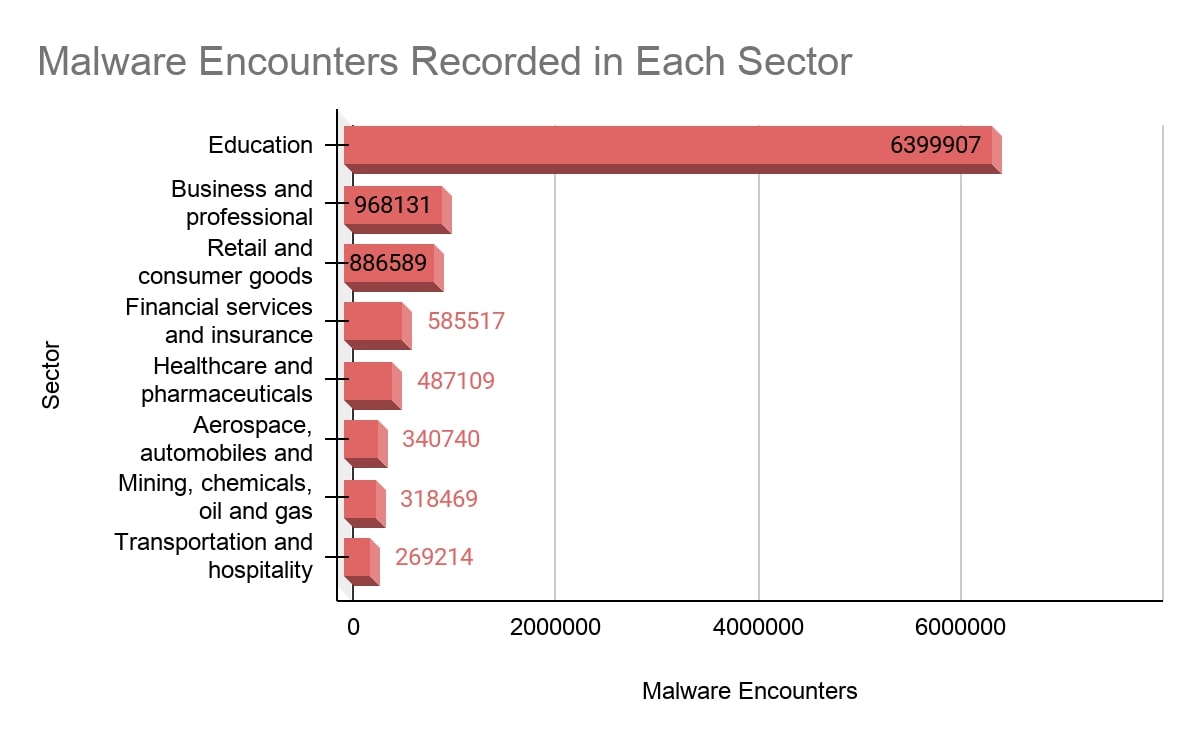
Most universities in the US are also considered ‘creditors’, according to the ‘Red Flags Rule’. So, any breach that results in identity theft can incur penalties of up to $3,993 per violation.
As you can imagine, educational institutions can have numerous cybersecurity issues, and we set out to research them. Being cybersecurity experts, we couldn’t help but wonder:
- How good are educational institutions at keeping hackers out and data safe?
- What attracts these attacks, and what are the most widespread vulnerabilities?
- What are the consequences of these attacks on university websites?
What we found through our study
Our team investigated 89 websites belonging to educational institutions (.edu) and found 293 vulnerabilities. We grouped them into five categories:
| Vulnerability |
Number
|
Vulnerable & outdated WordPress CMS
| 138 |
Content spoofing
| 67 |
URL redirection to untrusted websites
| 59 |
Unrestricted uploading of files with dangerous types
| 25 |
Insufficient security controls — sub-domains
| 4 |
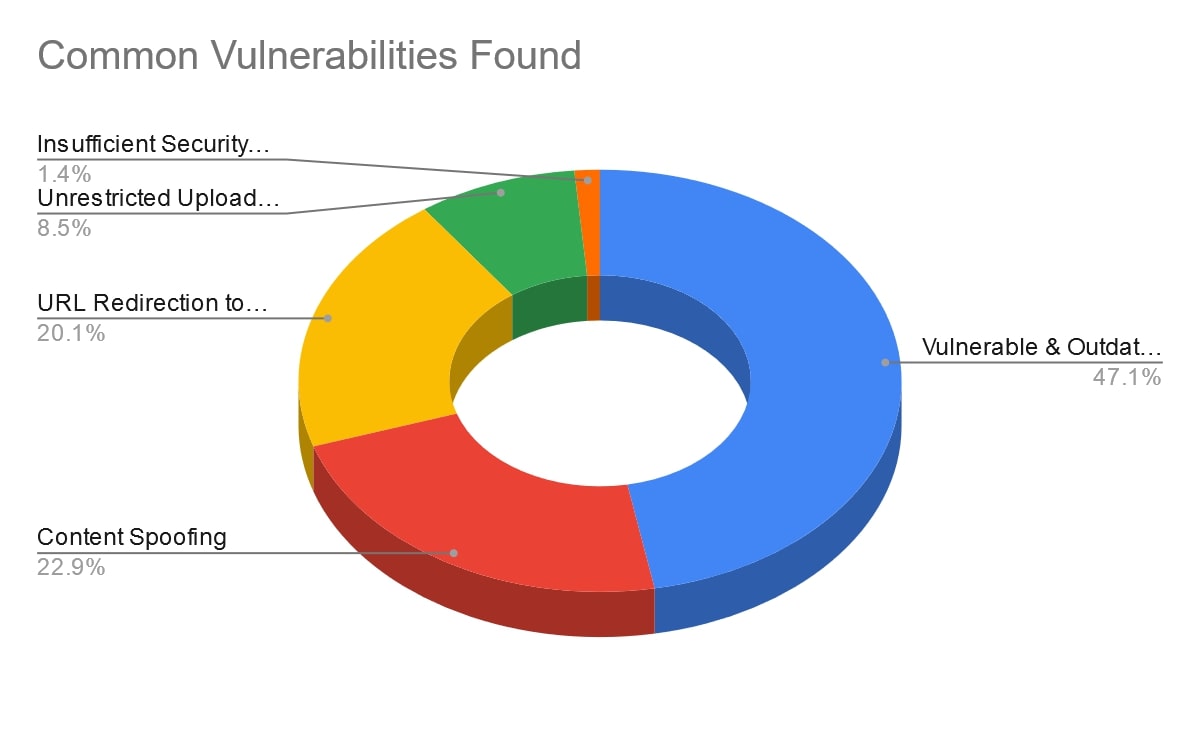
What do these vulnerabilities mean?
Let’s go through each vulnerability found and explain the impact of these security lapses, and how they can be prevented.
Vulnerable and outdated WordPress CMS
This is a common issue in the WordPress ecosystem. Outdated content management systems (CMS) could have vulnerabilities hackers know and are eager to exploit.
A 2019 report says that 47% of all hacked websites examined by the study had at least one backdoor that allowed hackers access to the site. CMS vulnerabilities were also common, with over 56% running outdated CMS applications at the time that they were hacked.
These are often ready-made exploits that are easy to reproduce. Here are some examples of vulnerable versions of WordPress detected by WPScan:
Component
| Version |
Version State
|
Vulnerabilities
|
Status
|
WordPress 4.9.8 (2018-08-02)
|
4.9.8
| Outdated | 25 | Alert |
WordPress 5.2.2 (2019-06-18)
|
5.2.2
| Outdated | 29 | Alert |
WordPress is the world’s most popular CMS and a common target with vulnerabilities that are easily exploited. If administrators don’t update these systems, the infrastructure becomes more and more susceptible to attacks every day it’s not done.
Effect:
It’s hard to predict the consequences of an attack on a vulnerable, unpatched component. It can be anything from a cosmetic change on the site to a completely compromised system.
Prevention:
Update the CMS as soon as new versions are available and check for components with known vulnerabilities.
Content spoofing attack
This attack allows hackers to change some of the content on a page. To do this, they simply inject code into a vulnerable application. You see, a website becomes vulnerable to this type of attack when form inputs (e.g. username, password, and so on) are not checked and can be used to send executable code to the server.
For example, submitting the following line in an input field could result in the image being referenced to display on a web page, even though the user doesn’t have the right to make such a change. In this case, it’s an HTML Injection.

The HTML tag ‘img src’, meaning ‘image source’, tells the browser to source a photo found at a specific web address.

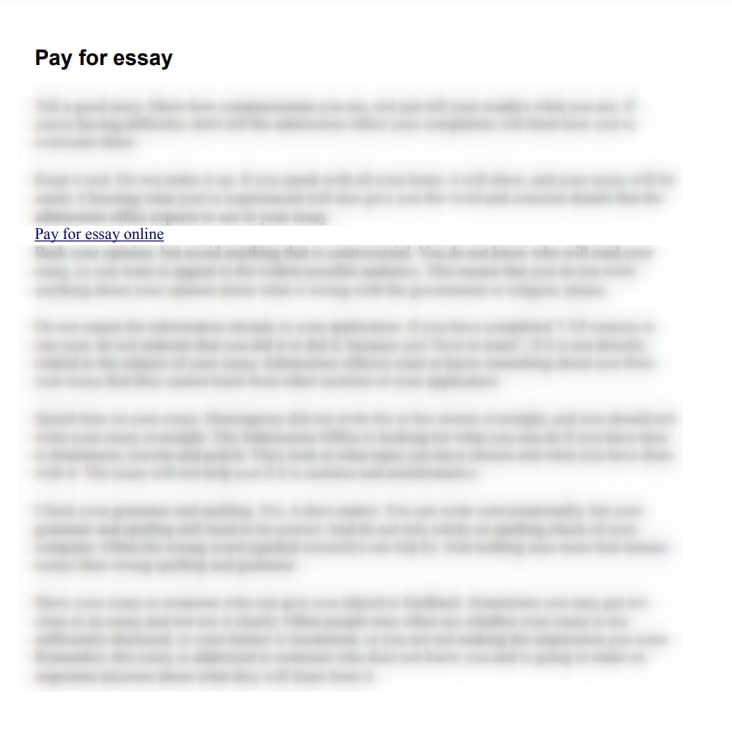
Through injection, intruders were able to add content to the website of an educational institution. It was an ad for a website that writes theses and essays for money.
Hackers add such content to websites to take advantage of their authority on search engines like Google. We ran a search for advertising content on the website and found that Google was indexing the page and returning the ad content as a search result. That’s insane!
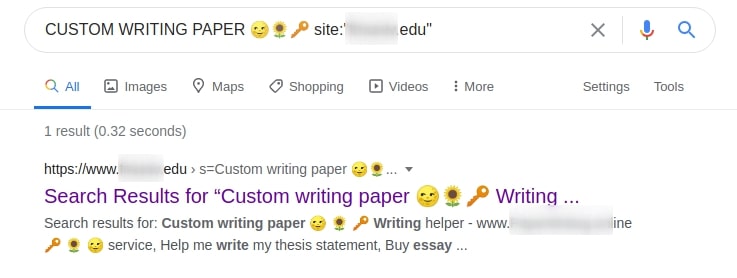
It’s even worse when attackers use code injection to generate and display a form identical to the legitimate one. In that case, when a user types their credentials (username, password etc.) into this form, the information is redirected and sent to the attacker. The cybercriminal can then steal the information using these credentials.
Fortunately, injection is a well-known type of attack, and there are ways to prevent it.
Effect:
- Interaction with fraudulent elements (like links and forms) on a legitimate page
- Unwanted content and ads on the website
- The structure of the website or web pages is messed up
Prevention:
- Validate user input for type, length, data-range, and format
- Encode any user input that will be output by the web application
- Use the POST parameter if possible
- Test with web vulnerability scanners before deploying a web application
URL redirection to an untrusted website
A redirect makes a web page available under more than one URL address. This means that when a browser attempts to open a URL that has been redirected, a different page is opened instead.
There are legitimate reasons to do this. For example, if a web page is being moved to a different address, anyone trying to access the old page needs to be redirected to the new URL.
However, it can also become a vulnerability, referred to as ‘Open Redirect’. A website is vulnerable when parameter values — the part of the URL that comes after the ‘?’ character — allow for information that will redirect a user to a new URL without prior validation. This could happen after an action (like login) or as soon as a page is loaded.
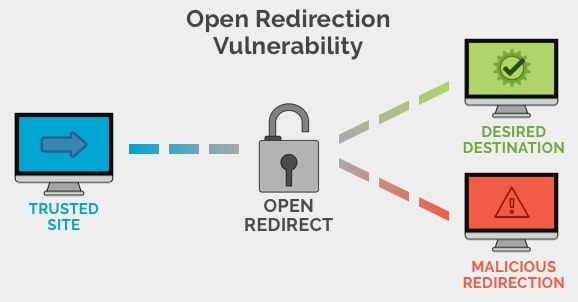
Most victims of URL redirection click on a link someone sent to them without looking at the address. Of course, hackers can make the URL look familiar or obscure it (using a random series of numbers and alphabets), making it practically impossible to see it’s fraudulent.

The above is an example of an .edu site we found to be vulnerable to redirects. To examine it, we added the link to the OWASP official page and found that it successfully redirected to this link. A hacker can choose any website to be redirected to, like an online casino.
Effect:
- Hackers can use vulnerable .edu website URLs to redirect users to phishing sites
- They can show users ads and banners
- Users can be redirected to websites that will then steal their data
Prevention:
- Try to avoid redirects
- Implement “whitelisting” — allowing a specific list of things — of user input
- Use a local URL
Unrestricted uploading of files
The internet is teeming with ready-made ways to exploit mistakes in the configuration of web applications and services. Vulnerabilities can often be exploited by sending unauthorized scripts or codes to the web server for processing. That's how we approached this vulnerability.

The ability to upload executable files without sanitization and validation checks is an open channel for attackers to deliver malicious code into a website or a web application.
Effect:
The impact will depend on just how much access an attacker gets. A hacker who gains initial access into the website’s infrastructure can then try and move laterally to a neighbor’s IT systems (through shared infrastructure like the server).
Apart from technical risks, uploaded files may also contain unauthorized content or links to websites advertising illegal or questionable services. For example, a document with just such unauthorized content — essays for sale — was found on one of the websites, and it wasn’t the only one we discovered.
Prevention:
- Generate a unique file name for an uploaded file instead of using the user-supplied filename
- Assume that all input is “malicious” and use a list of acceptable inputs that meet specifications while rejecting those that do not meet specifications
- Store all uploaded files outside of the document root and instead upload them to a specific directory from where they can be delivered dynamically
Insufficient security controls — subdomains
Generally, universities offer external services located on dedicated subdomains. For example, a university with a domain address www.some-university.edu might set up a blogging platform that is accessible from www.blogging.some-university.edu.
But, more often than not, the IT administration doesn’t pay enough attention to the identity and access management (IAM) of such services and any registered accounts on these services. This could lead to misuse.
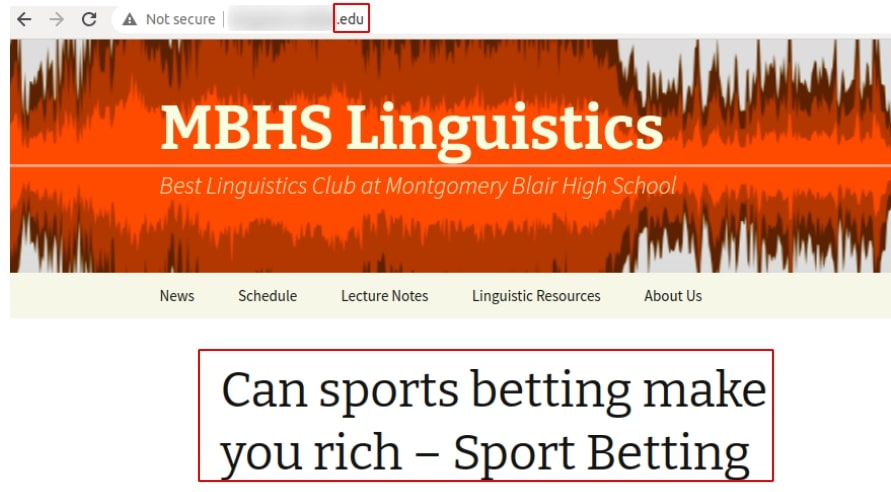
Credentials can be stolen — via social engineering or other ways — and used by attackers to gain a foothold in the IT system as the first step before attempting more sophisticated attacks. For example, we found a page advertising sports betting on the subdomain of a school website.
Effect:
Without the control of content hosted on subdomains, a regular inventory of all subdomains, and correct IAM, security controls will lose efficiency.
Prevention:
The general advice is to regularly validate DNS records and check which domains and subdomains are supported. Also, to validate identities and access provisioning procedures from time to time to revoke unused and outdated accounts.
***
The results of our cybersecurity study are pretty disturbing. Sadly, the cause of many vulnerabilities usually lies in the indifference shown to the common security requirements of a modern website. Fortunately, though, they can all be prevented.
The people responsible for university websites should take online security more seriously and ensure measures that take it to the required level' or something similar. Educational institutions should also consider investing more in their cybersecurity efforts. Without the right tools, even experts will struggle to keep up with attack vectors and breaches. Better safe than sorry, right?
Methodology
Here are the steps we took:
- Searched for vulnerable .edu domains using Google
- Analyzed websites for vulnerabilities using the free, open-source tools WPScan and webanalyze
- Reviewed websites to detect vulnerabilities and check the legitimacy of content
- Selected the most popular and likely attack vectors
- Analyzed vulnerabilities against the MITRE Common Weakness Enumeration database
- Recorded the results using statistics and descriptive methods