In this article you will find the following:
MacKeeper collaborated with an independent cybersecurity researcher Bob Diachenko to unveil and responsibly report the incident described in this data breach report.
“We're here to put a smile on your face” is one of the aims for leading website Raffle House.
But the company did anything but after MacKeeper’s Research Center recently discovered a data breach exposing user details on the site.
Raffle House hosts weekly lotteries with big prizes up for grabs including dream homes, clothing and other aspirational lifestyle accessories.
However, while the company offers life-changing prizes for its visitors, it inadvertently exposed its S3 bucket meaning it could have impacted many user lives for the worse. This was misconfigured for public access and allowed users to see the details of each other.
In total, 615 large files were exposed, featuring reports for hundreds of thousands users details, including personal information surrounding the winners and their prizes.
Data Breach Summary
| Affected company | Raffle House |
| Exposed environment | Amazon S3 bucket |
| Type of data exposed | Users personal information (name, email, phone, lottery stats, prizes, etc.) |
| Estimated number of records | 615 CSV files with raffle users and order details |
| Publicly indexed by | Grayhat Warfare search engine |
| Discovered on | June 7th, 2021 |
| Reported on | June 7th, 2021 |
| Issue addressed | yes |
Company profile
UK-based Raffle House draws weekly lotteries with a chance to win brilliant prizes.
Founded in 2017, the company offers customers the chance of entering a raffle to win a house without paying a mortgage or any stamp duty via £2 raffle tickets. Other huge, life-changing prizes are also available. These range from hotel holiday trips to sky-diving experiences and luxury items such as watches or jewelry.
Timeline
The timeline surrounding data breaches can vary. Sometimes a breach can be detected and several days can pass before any action is taken.
However, in this case, the breach was discovered and reported on the same day.
Database overview
In its FAQs around security, Raffle House claims “your data is saved on our secure and encrypted back-end so don't worry, it and you are in safe hands”.
And
“We need your email and telephone number because we need to contact you if you WIN! 😊Having two ways to contact you just means we have more chances to tell you the GOOD NEWS!”
However, in this instance, it was this important information that was exposed.
The exposed environment was an Amazon S3 Bucket. This is a public cloud storage infrastructure offered by Amazon Web Services (AWS) to provide object storage through a web service interface.
The exposed data was from Raffle House users who had entered different competitions to win prizes such as a helicopter sightseeing experience over London, a fitness machine, and an iPad Mini.
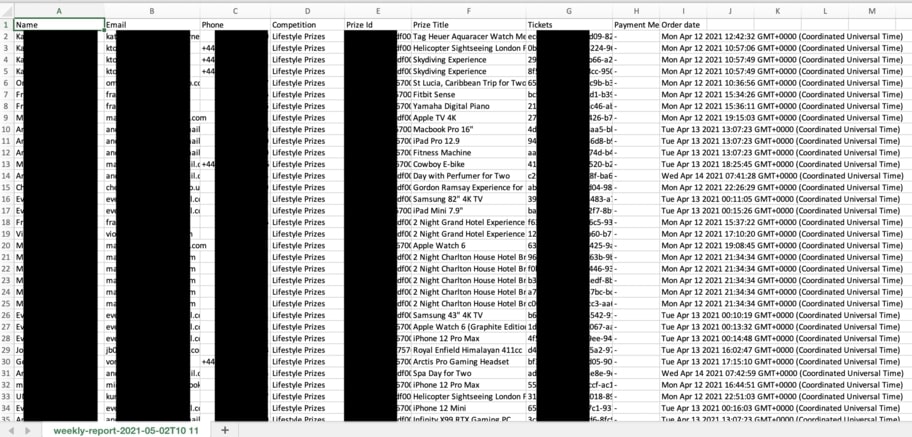
Some of the records exposed contained different forms of Personally Identifiable Information (PII) data for every user who entered a competition. This included:
- Full names
- Email addresses
- Phone number
- Prize id
- Referred email
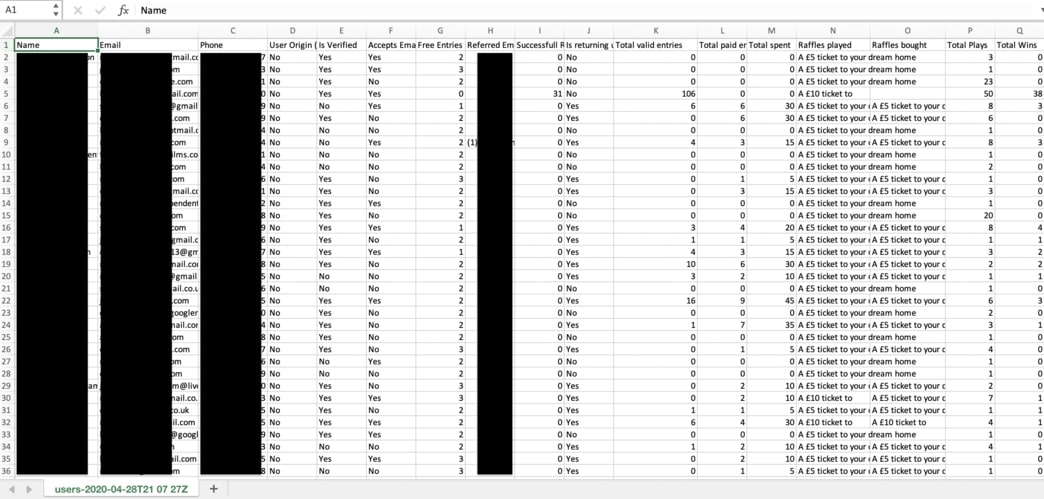
Other exposed data included information submitted raffles to win dream homes. Again, the leaked details included PII such as name, email, phone, and total numbers of plays and wins.
Data breach impact
While many Raffle House website users are hoping to win big prizes, for some unlucky winners it was the exposure of their details that was an unexpected result of using the website.
User impact
Phishing
Contact data is invaluable for cybercriminals looking to conduct phishing scams. If they have mobile numbers or email addresses, then this information can be used by scammers to target victims and trick them into divulging any sensitive information. The more details they have, the more personalised and convincing their tricks can be.
Identity theft or fraud
Armed with personal details such as email or a contact telephone number, then scammers can use this information to conduct identity fraud. Examples of ID fraud include ordering goods on behalf of a victim or opening a bank account in their name.
Blackmail
Again, with all of these personal details now available online, scammers will have plenty of ways to blackmail Raffle House users and try and extort money from them.
Impact on Raffle House
Alongside the Raffle House customers who have seen their details exposed online, there are also possible ramifications for the company too.
Loss of reputation
Loss of reputation is a key concern for Raffle House in this instance, particularly as their website outlines their commitments to keeping payment details and financial information secure.
If this becomes a news story, then it can also give any competitors a potential advantage, particularly those looking to use any bad publicity to attract new customers. For Raffle House, this has the potential to be damaging alongside some of the other negative press the company and its competitions have previously attracted.
Lost competitive advantage
If any competitors had seen the exposed information, then this could have given them valuable insight into how Raffle House operates their competitions and company.
At risk of hackers
With this information exposed, any hackers could also use this data to target Raffle House and exploit vulnerabilities in their IT infrastructure for their own ends.
Expert advice for Raffle House
Raffle House could have potentially avoided this data breach by adhering to some security measures surrounding the S3 Bucket.
Secure your servers
You can restrict access to the S3 Bucket by writing policies specifying user access.
Limiting access via proper user rules is good practice for companies and firms utilizing this kind of cloud storage.
Encrypt data
There are different ways to encrypt your data either server or client-side. Adopting best practices around data encryption would have been useful in this instance.
How to protect yourself from data breaches
1. Use an extra security layer of multi-factor authentication
As everyone has their phone at their hand at all times — using the Google Authenticator App has become accessible. 2-step verification will make sure it’s really you when trying to sign in.
2. Use long passphrases
At least 12-14 characters. And make those not be based on personal data.
3. Change your passwords regularly
Your passwords should be changed at least every 180 days. Besides, don't reuse at least 10 last passwords.
4. Don't store your passwords locally
Saving them on Google Chrome or other browsers, notepads, cloud storage like Dropbox or Google Drive, or even a piece of paper that you keep on your office desk is not a good idea.
5. Scan your email for breaches
Oftentimes it takes a lot of time to learn that your records were exposed in a data breach. However, you can learn about any breaches much quicker if you use the ID Theft Guard tool in MacKeeper. Set up your account and add any of your emails. ID Theft Guard will regularly check all your accounts and instantly alert you if something goes wrong.
***
Discovering data leaks is part of MacKeeper Research Centre's ongoing work into protecting online users and keeping their details safe.