In this article you will find the following:
Could you tell if your Mac has been remotely accessed? macOS security features make MacBooks and other Apple devices very secure. However, it’s still possible for your Mac’s security to be compromised.
Cybercriminals may want to access your Mac remotely for many reasons. However, there are ways to secure your system and ensure your Mac is as safe as possible.
In this article, we’ll explain how to know if someone has remote access to your Mac and how to stop someone from accessing your computer remotely.
Remote hacking isn’t the only privacy risk online—fortunately, we’ve gathered more information about online privacy protection. Has someone blackmailed you online or asked you for a ransom to access your data? Check out our article on how to remove ransomware.
Before we start:
If you want to stop someone from accessing your Mac computer remotely, using a VPN (virtual private network) can help. VPNs hide your real IP address, making it harder for cybercriminals to gain access to your Mac. MacKeeper’s Private Connect is an easy-to-use VPN—you can be ready to go in minutes!
Get started with MacKeeper’s Private Connect:
- Download MacKeeper.
- Choose Private Connect from the sidebar.
- Select Turn On.
What is remote access
Remote access is when someone gains access to your Mac without being in physical contact. They could be in the same building as you or on the other side. They could be doing it for a good reason, such as providing tech support or more nefarious purposes.
Cybercriminals can use remote access as part of remote hacking scams. When someone accesses your Mac remotely for malicious reasons, they may have a few different aims:
- They may want to find out confidential information—about your finances, online login or banking details, for example.
- They could be spying on you or your company. This is particularly likely if you are a high-profile individual or have a very senior role in an organization.
- They may want to delete data from your Mac.
- They may want to access your webcam or gain access to images or videos stored on your computer.
- They may want to install tracking software on your computer, such as keyloggers or other monitoring applications.
Сan someone remotely access your Mac
People can remotely access Macs. In fact, there are plenty of legitimate reasons that someone would need remote access to your Mac. For example, Mac remote access can be used for:
- IT support and troubleshooting: Rather than a technician needing to travel to you, they can remotely access your Mac and sort out issues from a distance.
- Remote work with colleagues: If you and your coworkers aren’t based in the same location, you might use remote access for training, joint projects, or other collaborative work.
- Screen sharing: Whether you’re presenting at a video conference or just need to quickly share information, screen sharing is a useful way to show someone exactly what you can see on your Mac.
You may have used applications like TeamViewer, Microsoft Remote Desktop, or AnyDesk to remotely access other people’s computers or virtual machines. Alternatively, you may have invited people to use Remote Login or Screen Sharing so that they can access your Mac.
However, some people may want to access your Mac for malicious purposes remotely, and that’s what we want to prevent. So that’s why we need to be able to tell if your Mac has been remotely accessed.
How to check if someone is remotely accessing your Mac
It’s important to know if someone has remote access to your Mac so that you can solve the problem and avoid becoming a victim of blackmail, fraud, or identity theft.
Here are some steps that you can take to check if someone is remotely accessing your Mac computer:
- Check for remote login
- Check your user accounts
- See all the latest activity on your device
- Inspect for suspicious activity
- Check installed programs on your Mac
- Check your firewall settings
- Run an antivirus scan
1. Check for remote login
Remote Login allows people to access your Mac remotely. It’s a really useful tool, and you may have used it for legitimate reasons. However, it can also be exploited.
To check whether Remote Login is turned on:
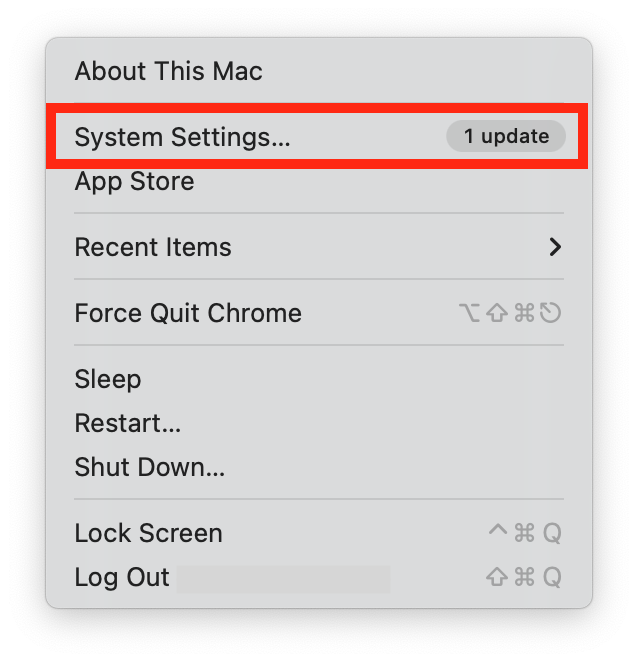
- Go to the Apple menu > System Settings (System Preferences).
- If you’re running macOS 12 or below, choose Sharing. If you’re running a newer macOS version, select General, then scroll down to choose Sharing.
- Select Remote Login.
- Look at the settings—is Remote Login turned on? Are any boxes checked, or do any unknown users have permissions?

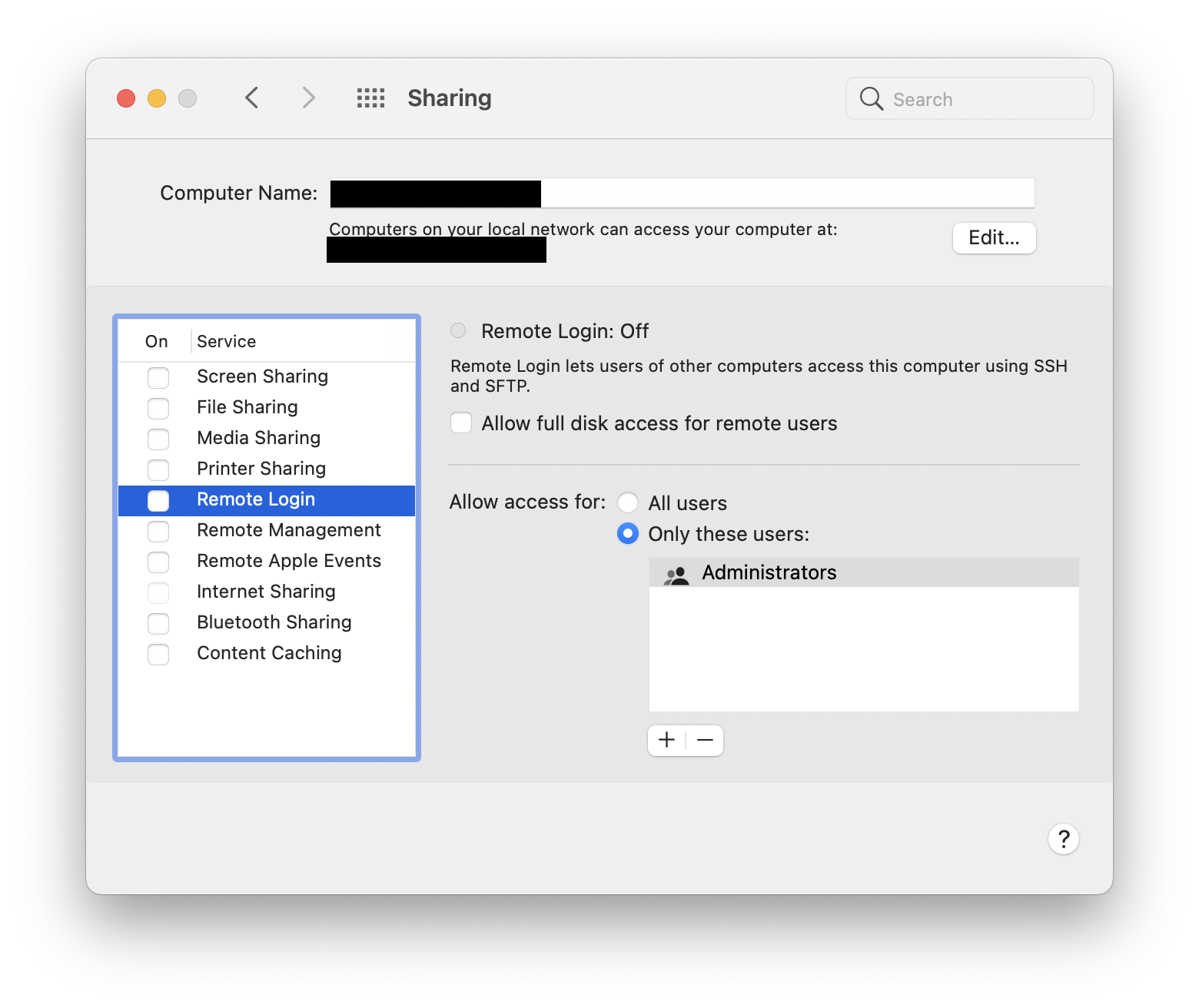
Note from our team: If you’ve never used Remote Login, it should be turned off by default.
2. Check your user accounts
Apple computers let you set up multiple user accounts. This is a useful feature—for example, if multiple people use the same computer, user accounts let you personalize your experience.
However, you shouldn't see multiple user accounts if you don’t have multiple users on your Mac.
How to check for user accounts:
- Open Terminal. You can do this by going to the Launchpad, typing Terminal into the search bar, and selecting the icon.
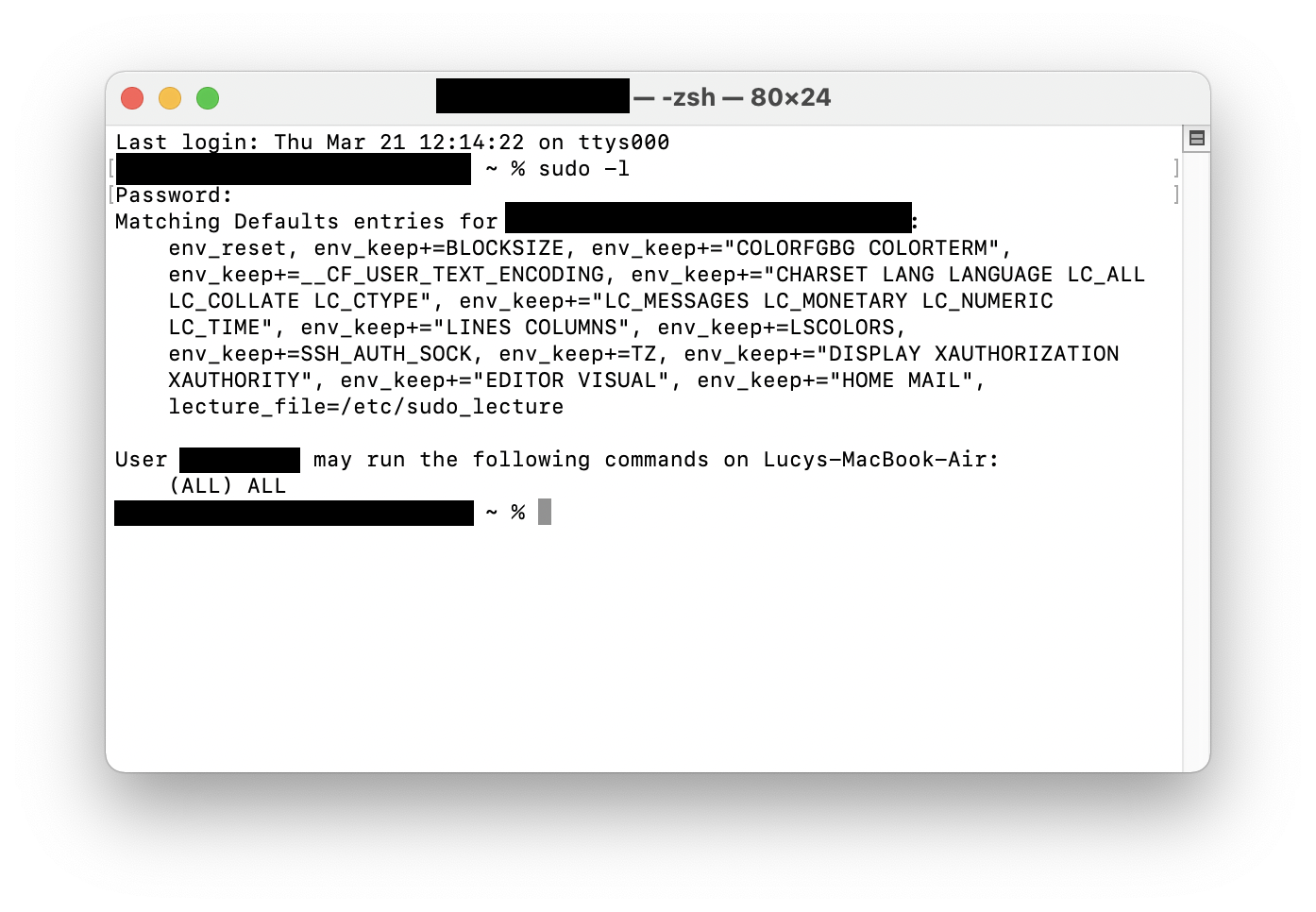
- Type in the command sudo -l and press Enter.
- Type your password, and press Enter.
- Type users and press Enter. This will give you a list of users who are currently logged in. If you see unexpected usernames here, this may be a sign that there is an issue.
- Type dscl -list /users and press Enter. This will provide a much longer list of information and many more users. Most of them will be legitimate Apple system accounts, but you may notice suspicious usernames.
3. See all the latest activity on your device
Someone with remote access to your Mac may be opening, editing, or deleting files. We can check recently-accessed files in Finder.
How to see recently-accessed files on your Mac:
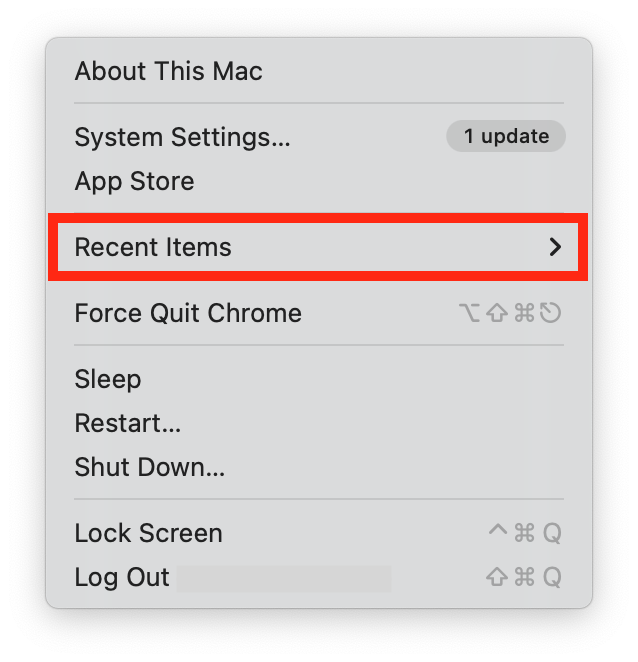
- Go to Apple menu > Recent Items.
- This will bring up a list of the last applications, documents, and servers accessed on your Mac. Are these all the ones you would expect?
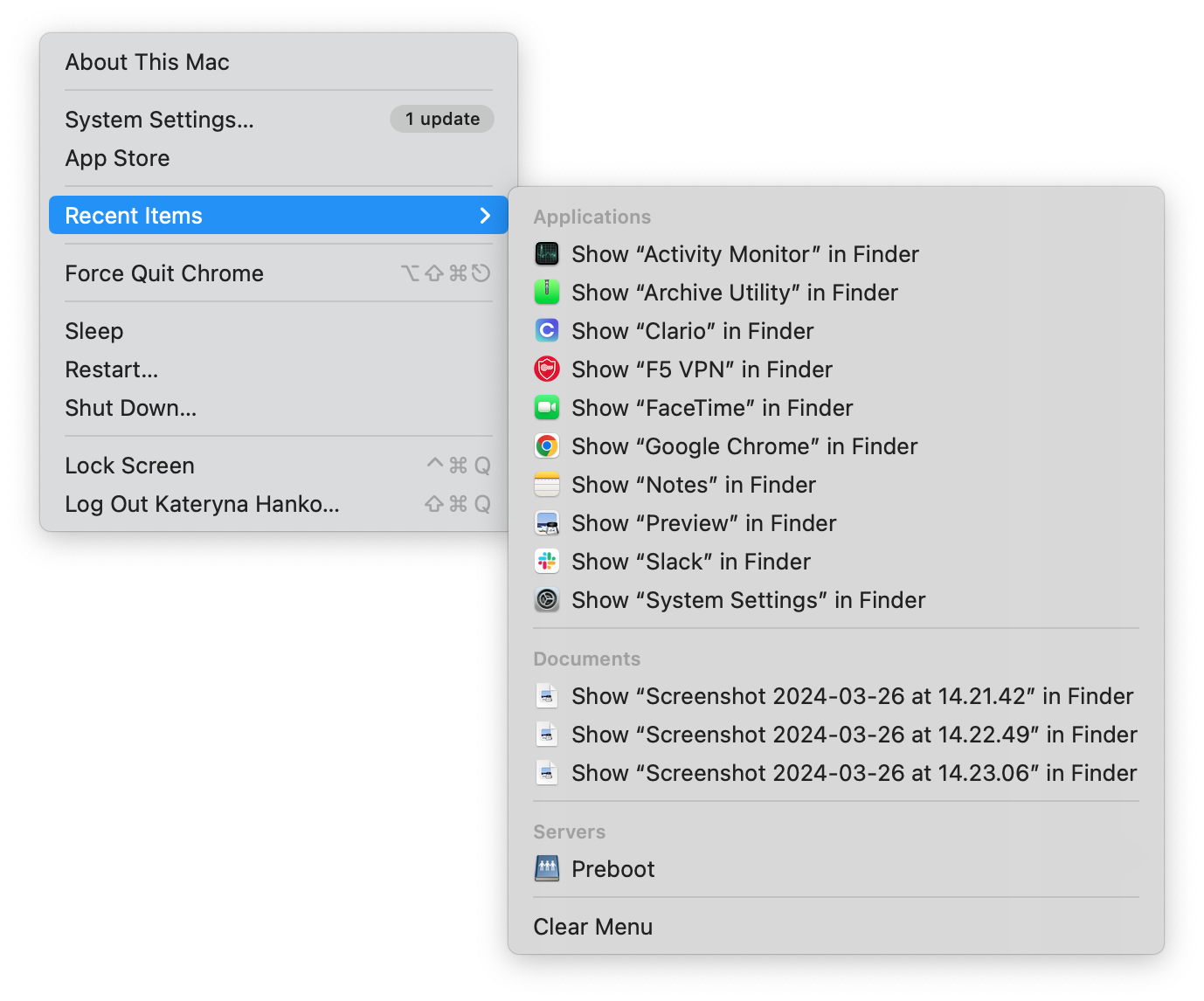
You can also see which users last logged in to your Mac.
How to find the last logins on your Mac:
- Open Terminal. Do this by going to the Launchpad and typing Terminal into the search bar.
- Type last and press Enter. This will give you a list of the last logins on your Mac. Can you identify them all?
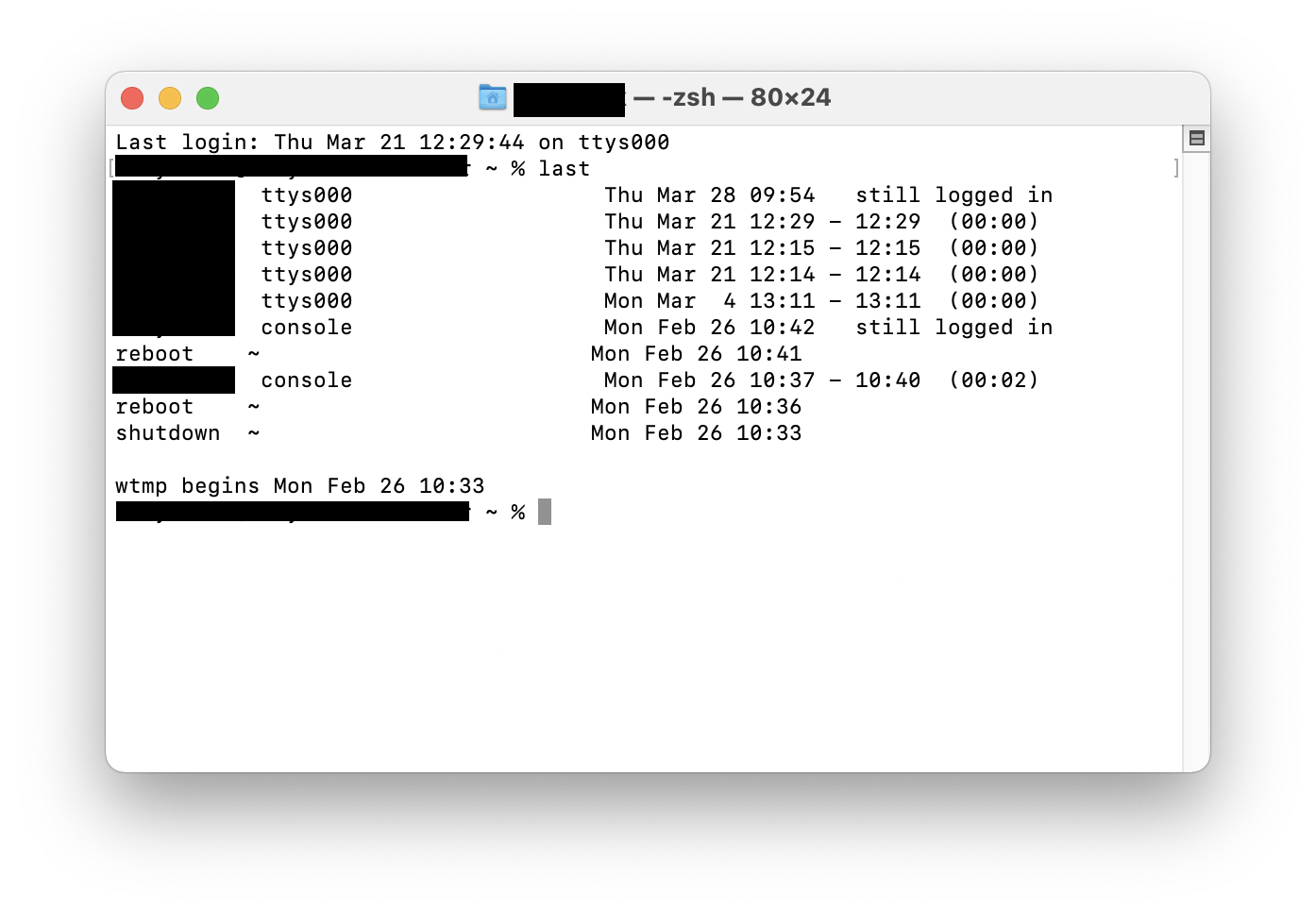
This information might help you tell if your Mac has been remotely accessed.
4. Inspect for suspicious activity
Have you noticed anything unexpected or suspicious happening on your Mac?
- Has your webcam’s light turned on when you haven’t been using it?
- Have you seen unexpected pop-ups?
- Are any of your files or apps missing or in different locations?
If you identify any of these, it could be a sign that someone has remote access to your Mac.
Hint from our team: There could be other reasons for these symptoms, such as malware on your Mac. We recommend running regular malware scans and using real-time antivirus protection to ensure your computer stays safe.
5. Check installed programs on your Mac
Some hackers might install malware and destroy data on your computer. Others might install a keylogger or other tracking software to monitor your activity.
How to check what applications are installed on your Mac:
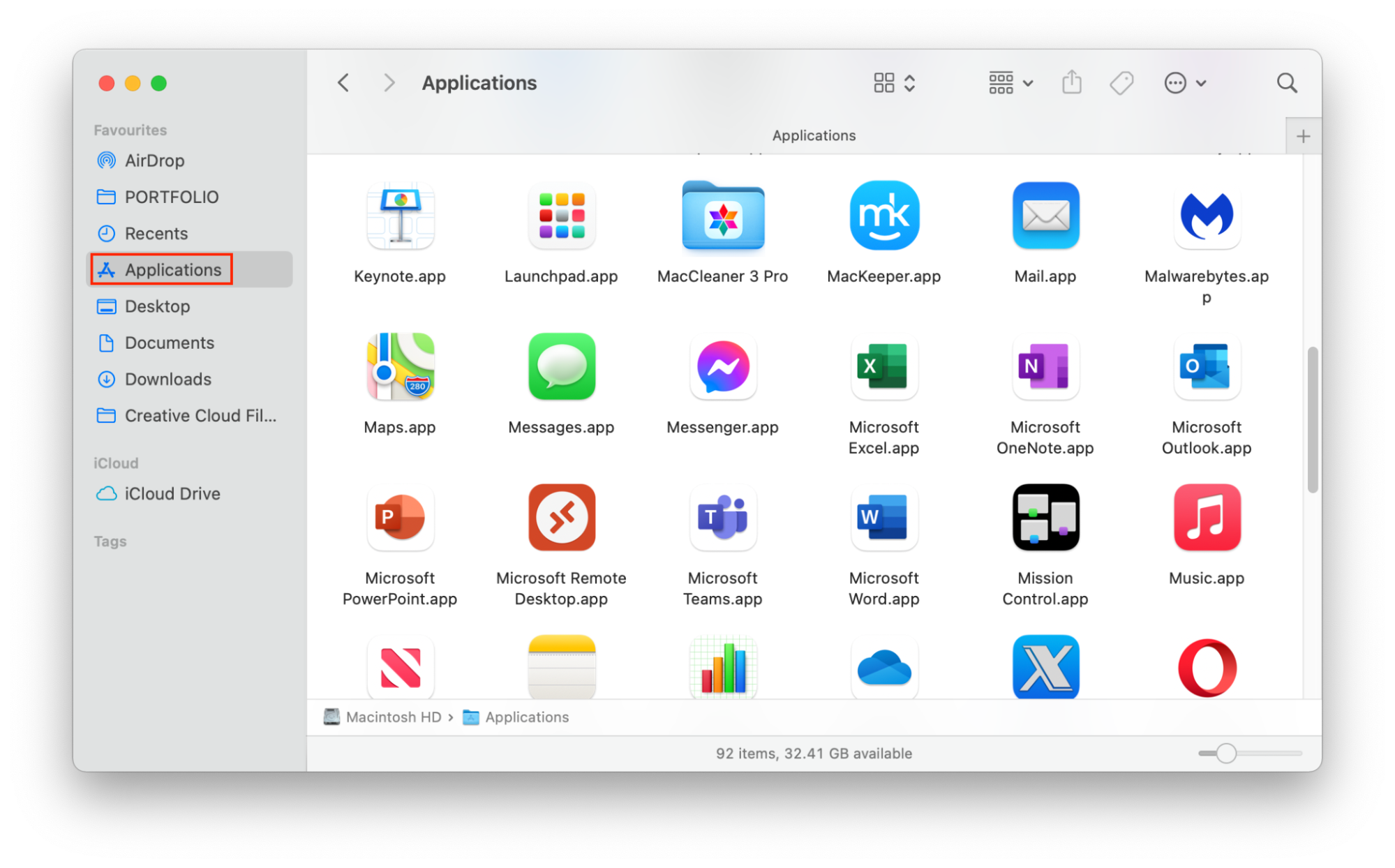
- Open Finder, and go to the Applications folder.
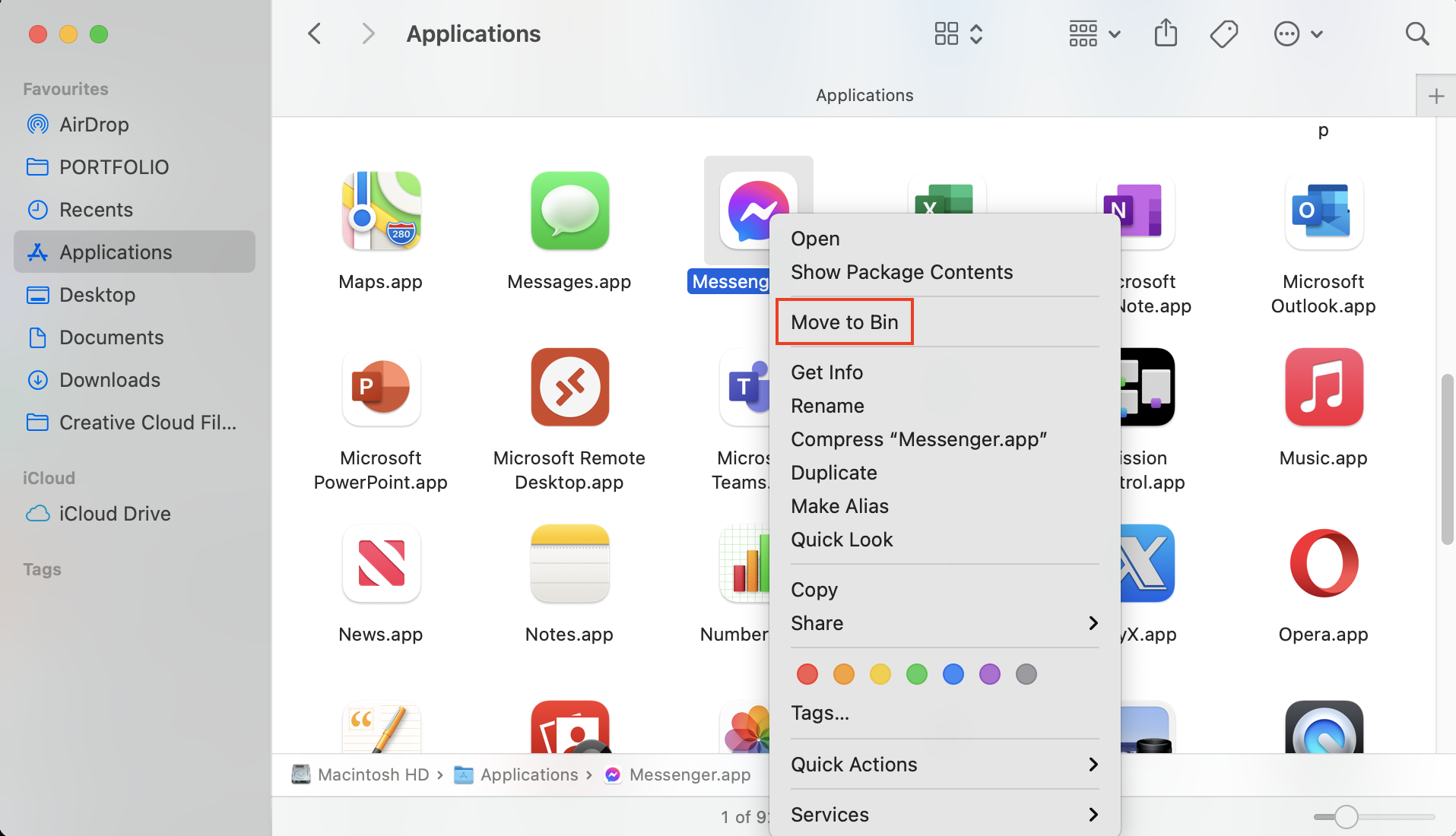
- Look through the list of applications. Do you recognize them all? If any look suspicious, delete them by right-clicking and choosing Move to Bin, or by dragging them to the Bin.
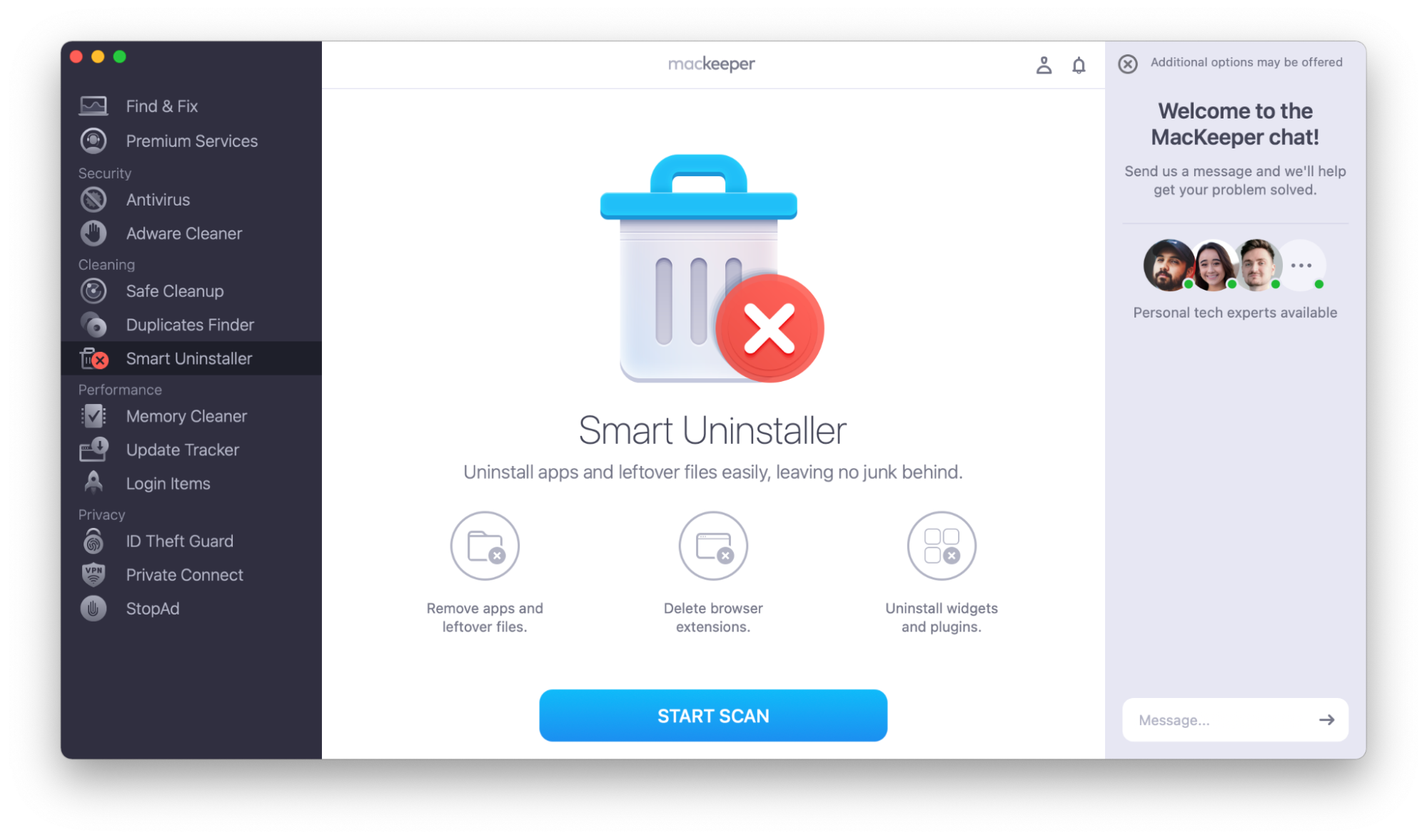
Some applications can leave data behind when you uninstall them. Delete malicious programs fully so they don’t leave anything behind on your system. MacKeeper’s Smart Uninstaller can help.
To uninstall applications completely:
- Download MacKeeper and open the app.
- Choose Smart Uninstaller from the sidebar, and select Start Scan.
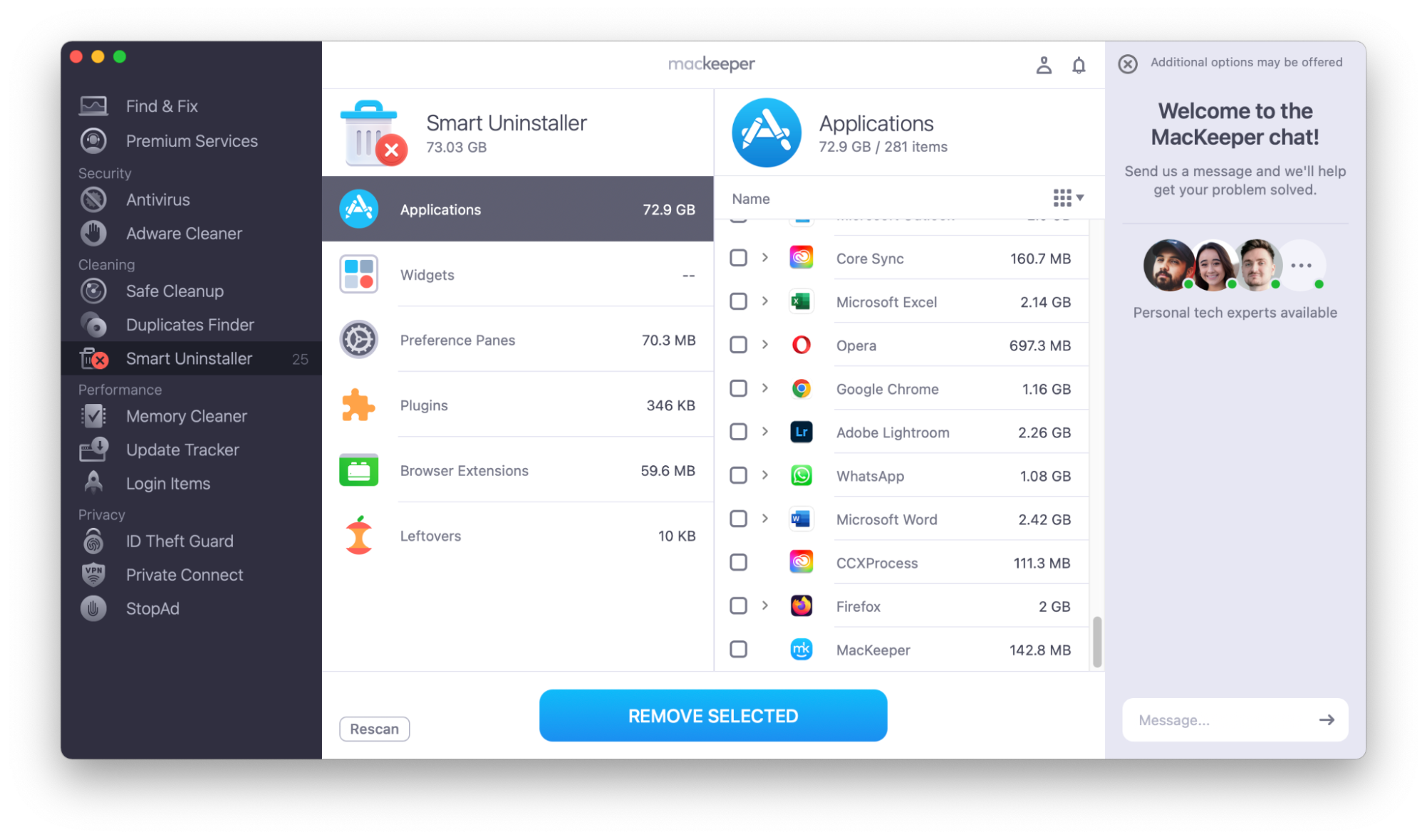
- When the scan is finished, click Applications. Look through the list and select any that you want to remove.
- Choose Remove Selected.
6. Check your firewall settings
A firewall is an important part of network security. It prevents someone from having unauthorized access to your device. If you don’t have a firewall turned on, your Mac may be at risk.
Check your Mac firewall settings:
- Go to Apple menu > System Preferences.
- Choose Security & Privacy.
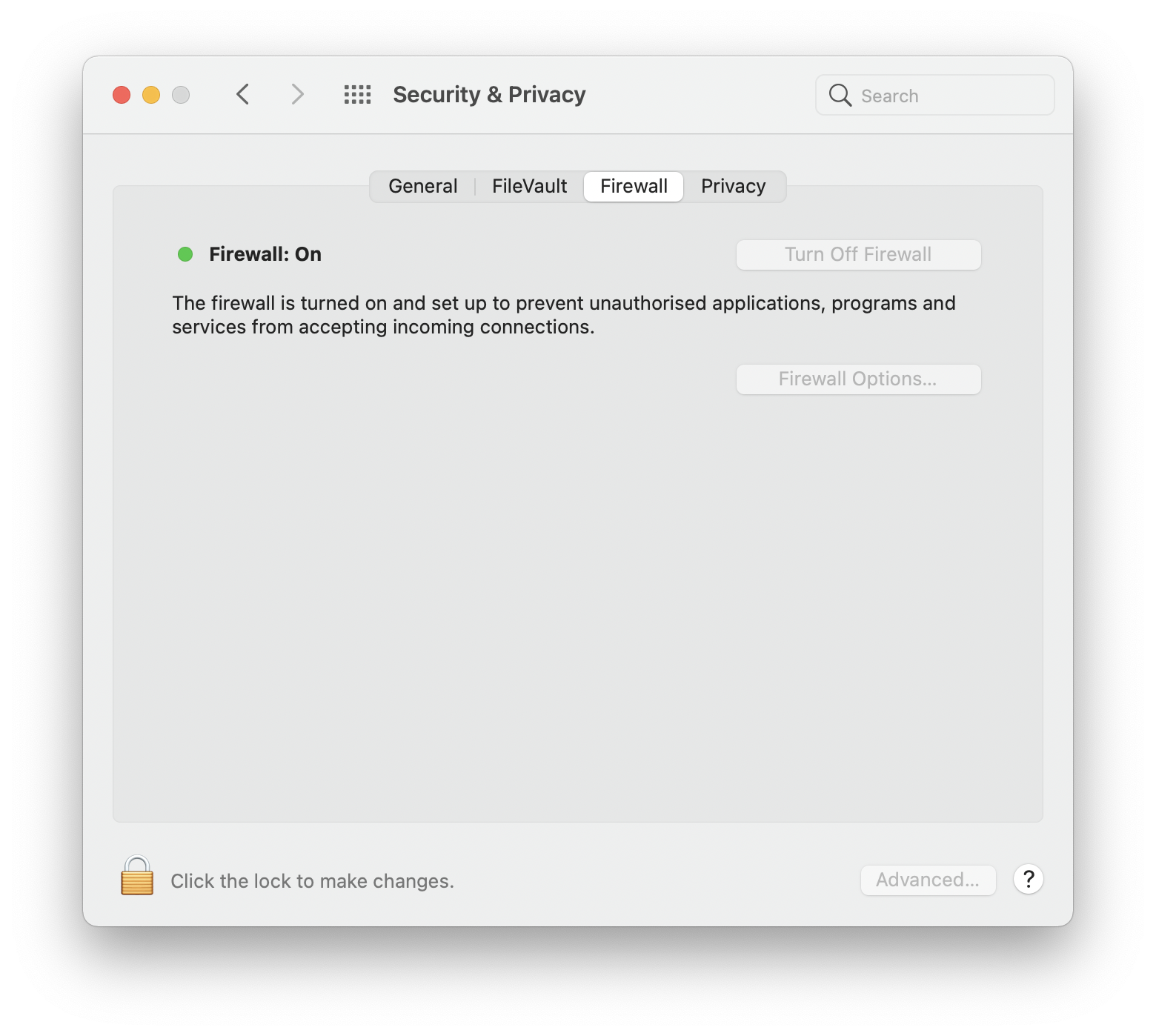
- Select the Firewall tab. Is it turned on?
7. Run an antivirus scan
It’s a good idea to scan your Mac for malware on a regular basis. A hacker may have installed malware on your system, or you may have security vulnerabilities that put your Mac at risk from other sources. MacKeeper’s Antivirus can help with a quick and easy virus scan.
Here’s how to run an antivirus scan with MacKeeper:
- Open MacKeeper.
- Select Antivirus from the sidebar.
- Choose Start Scan.
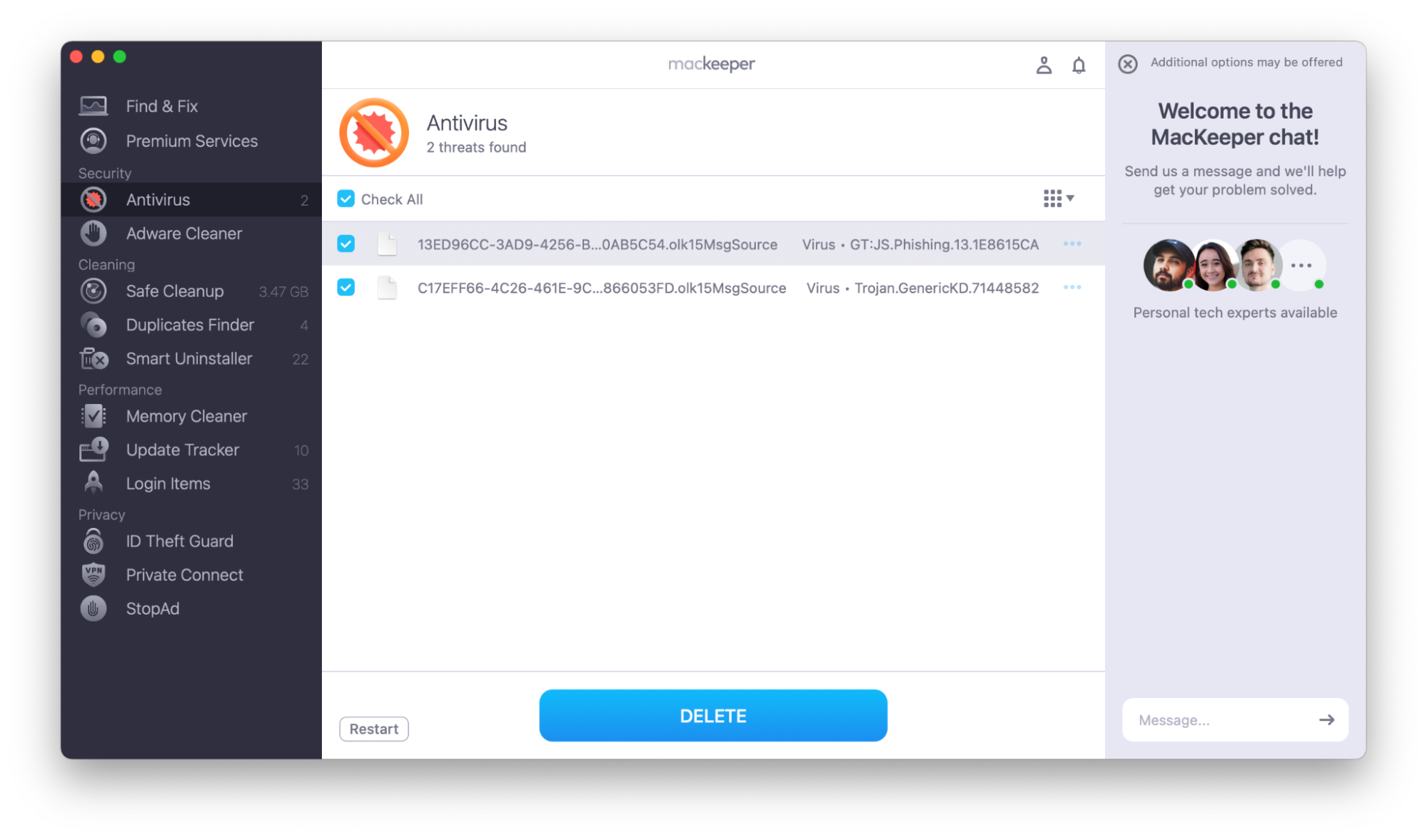
- If any threats are found, select them and choose Delete.
How to stop someone from accessing your Mac remotely
You might need to stop someone from accessing your Mac computer remotely. If you’re concerned that someone is currently accessing your system and want to stop them immediately, disconnecting from the internet is the quickest way to do so.
There are a few ways to disconnect from the internet on a Mac:
- If your Mac uses an Ethernet cable to connect to the internet, unplug it.
- If your Mac uses Wi-Fi and you want to disconnect all Wi-Fi devices, turn off or unplug your router.
- If you want to turn Wi-Fi off on your Mac only, click the Wi-Fi symbol on the menu bar. Toggle the Wi-Fi switch.
When you log back on, stop someone from accessing your computer remotely using a Mac VPN. A VPN (virtual private network) gives your device a new IP address, making it harder for hackers to gain access.
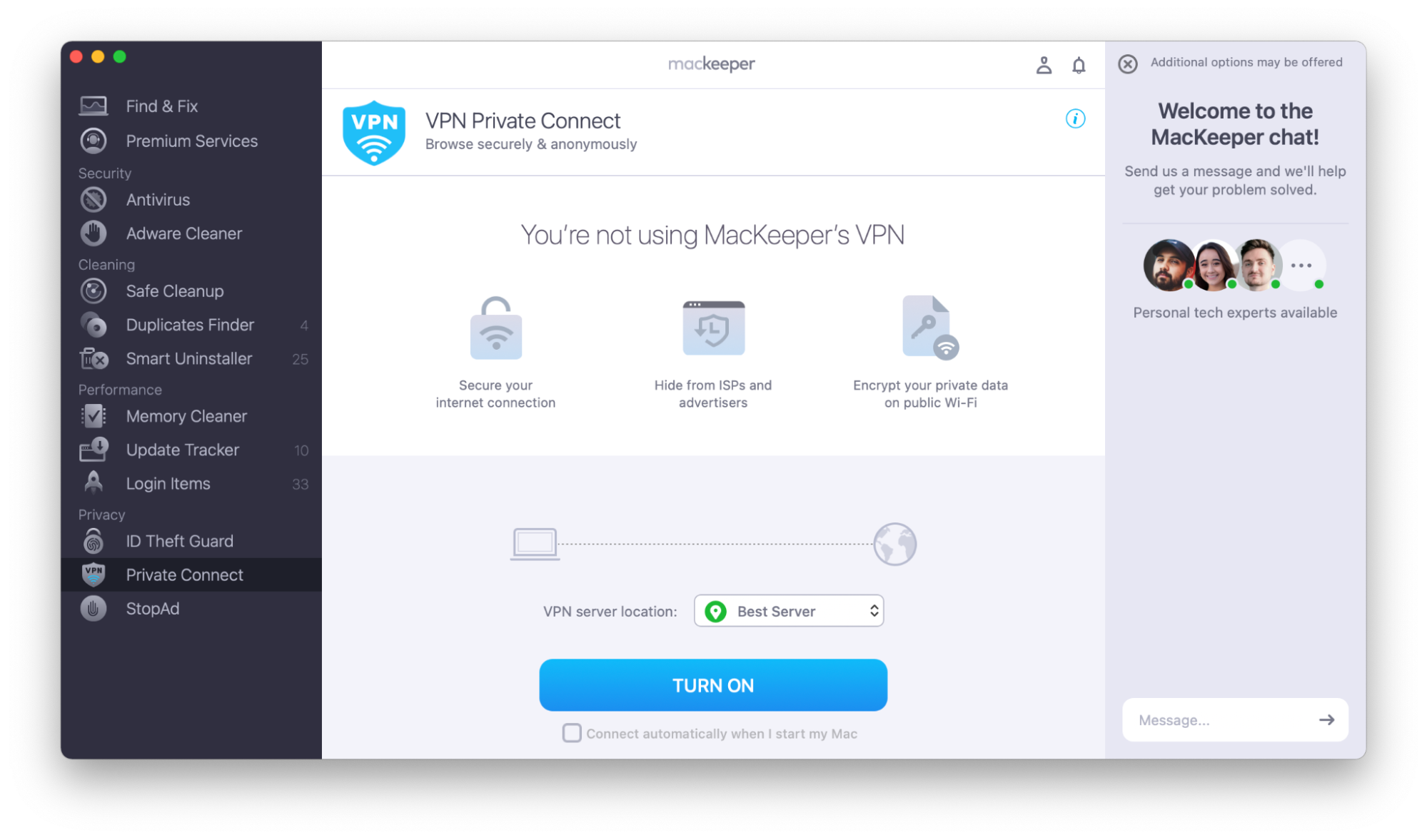
MacKeeper’s VPN Private Connect provides an easy-to-use VPN you can activate in several clicks. What’s more, you can choose to connect to the VPN automatically whenever your Mac starts up, meaning that your web browsing will always be secure.
To use MacKeeper’s VPN Private Connect:
- Open MacKeeper.
- In the sidebar, choose VPN Private Connect.
- Click Turn On, and check the box next to Connect automatically when I start my Mac, if necessary.
How to prevent someone from remotely accessing your Mac
While it’s good to be able to stop a hacker while they’re remotely connected to your Mac, it’s obviously much better to prevent them from accessing it in the first place.
To prevent someone from remotely accessing your Mac:
- Turn off remote login
- Disable remote control
- Disconnect from the Internet
- Update your passwords
- Turn on a firewall
- Use antivirus software
- Protect your Wi-Fi router
- Back up and wipe your device
These steps for Mac should stop someone from accessing your computer remotely.
Note from our experts: If you’re concerned about a computer that’s part of a network (for example, at work or school), talk to your system administrator before attempting to make any changes.
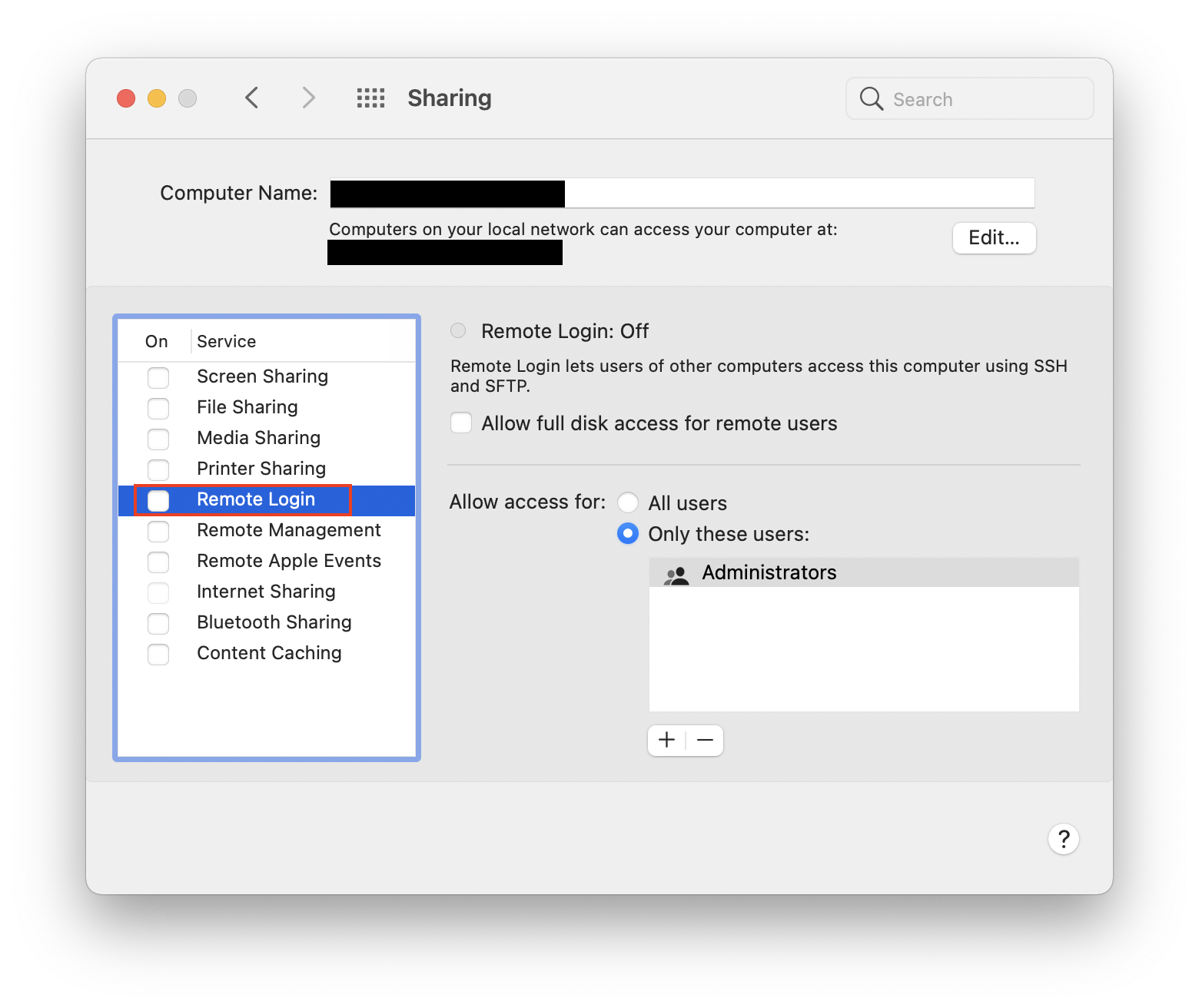
1. Turn off remote login
We’ve already talked about Remote Login, Apple’s built-in remote access facility. There are lots of reasons that you might use Remote Login. However, if you aren’t using this feature, you should keep it turned off for optimal security. If you don’t remember turning Remote Login on, this could be a way to know if someone has remote access to your Mac.
To turn off Remote Login on your Mac:
- Go to the Apple menu > System Preferences.
- If your Mac runs macOS 12 or below, choose Sharing. If you have a newer version of macOS, choose General and scroll down to Sharing.
- Select Remote Login.
- Uncheck the box next to Remote Login.
Remote Login should now be disabled.

2. Disable remote control
Remote Management, also sometimes known as remote control, is another of Apple’s built-in remote access features. It’s particularly useful for network administrators, who might need to manage your Mac remotely—for example, to change permissions, settings, or access privileges.
How to turn off Remote Management on your Mac:
- Go to the Apple menu > System Settings.
- If your computer runs macOS 12 or below, choose Sharing. If you have a newer version of macOS, choose General and scroll down to Sharing.
- Uncheck the box next to Remote Management.

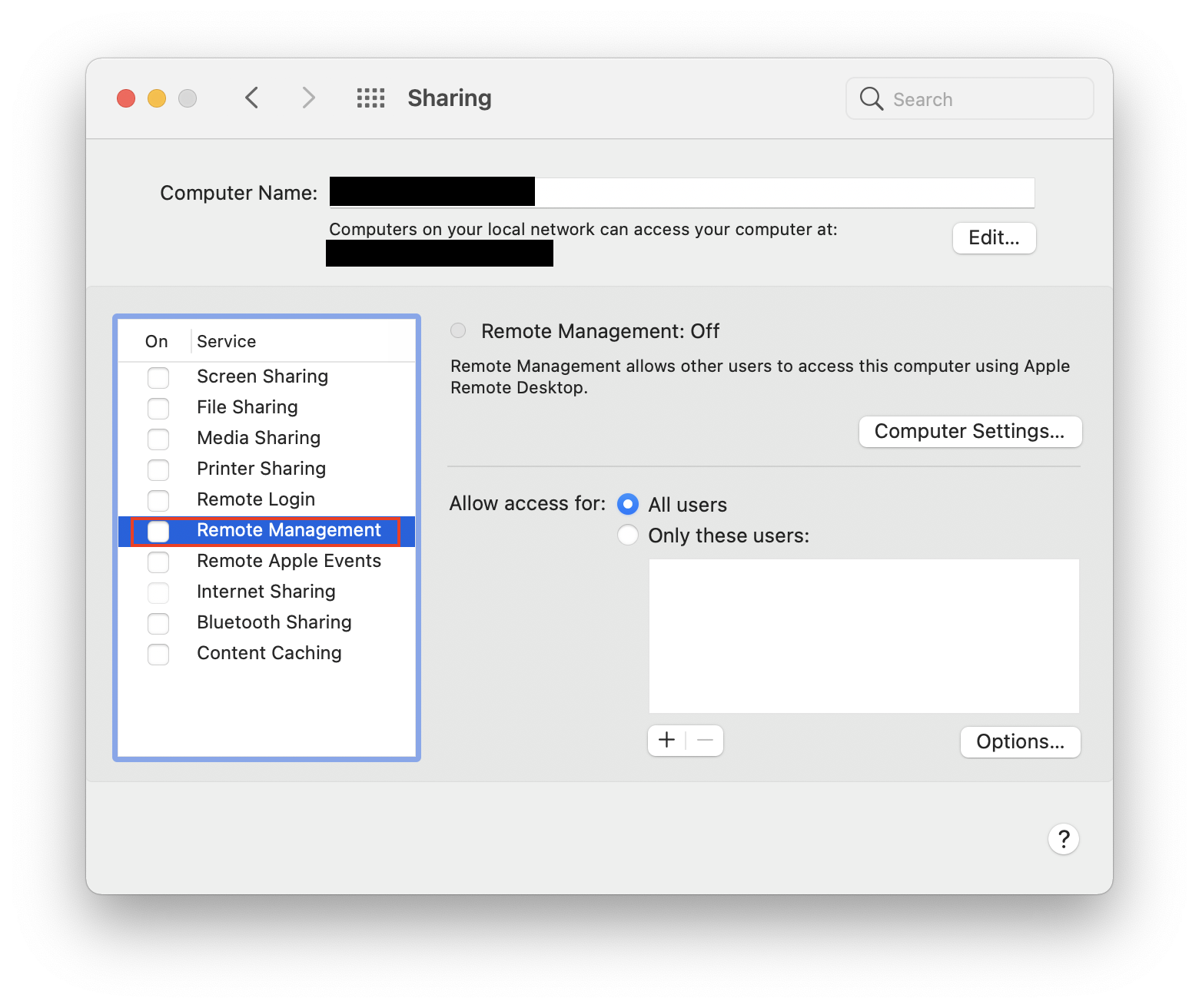
Important: Remote Management doesn’t let external users access your Mac, but it does allow them to say who can access it.
3. Disconnect from the Internet
If your Mac is being remotely accessed, hackers are using the internet to do it. These days, all our devices are connected to the internet, and we rarely think of disconnecting from it. On average, internet-using households in the US have 16 devices connected at any one time!
If someone has remote access to your Mac, disconnect from the internet before changing other security settings.
You can do this by removing your Ethernet cable, disconnecting or turning off your router, or turning your Wi-Fi off on your Mac.
Now that your Mac is disconnected from the internet, you can work on permanently stopping someone from accessing your computer remotely.
4. Update all your passwords with a secure device
Once you know if someone has remote access to your Mac, you should change your passwords for online accounts—especially ones that are confidential or involve finances. However, the hackers may have installed a keylogger or other tracking software that would allow them to see your new passwords too.
Because of this, we’d recommend changing your passwords on another device. Use your smartphone, tablet, or another uncompromised computer.
You might want to change your password on accounts such as:
- Online banking
- Emails
- Social media
- Online shopping sites
- Online gaming sites
Our expert’s recommendation: Remember to use a different password for multiple accounts, and make sure you choose something difficult to guess.
5. Turn on the firewall
Firewalls prevent people from having unauthorized access to your device. Fortunately, Apple computers come with a built-in firewall feature.
How to turn on the firewall on your Mac:
- Go to Apple menu > System Settings.
- Choose Security & Privacy.
- Go to the Firewall tab.
- If the firewall isn’t turned on, click the Turn On Firewall button.
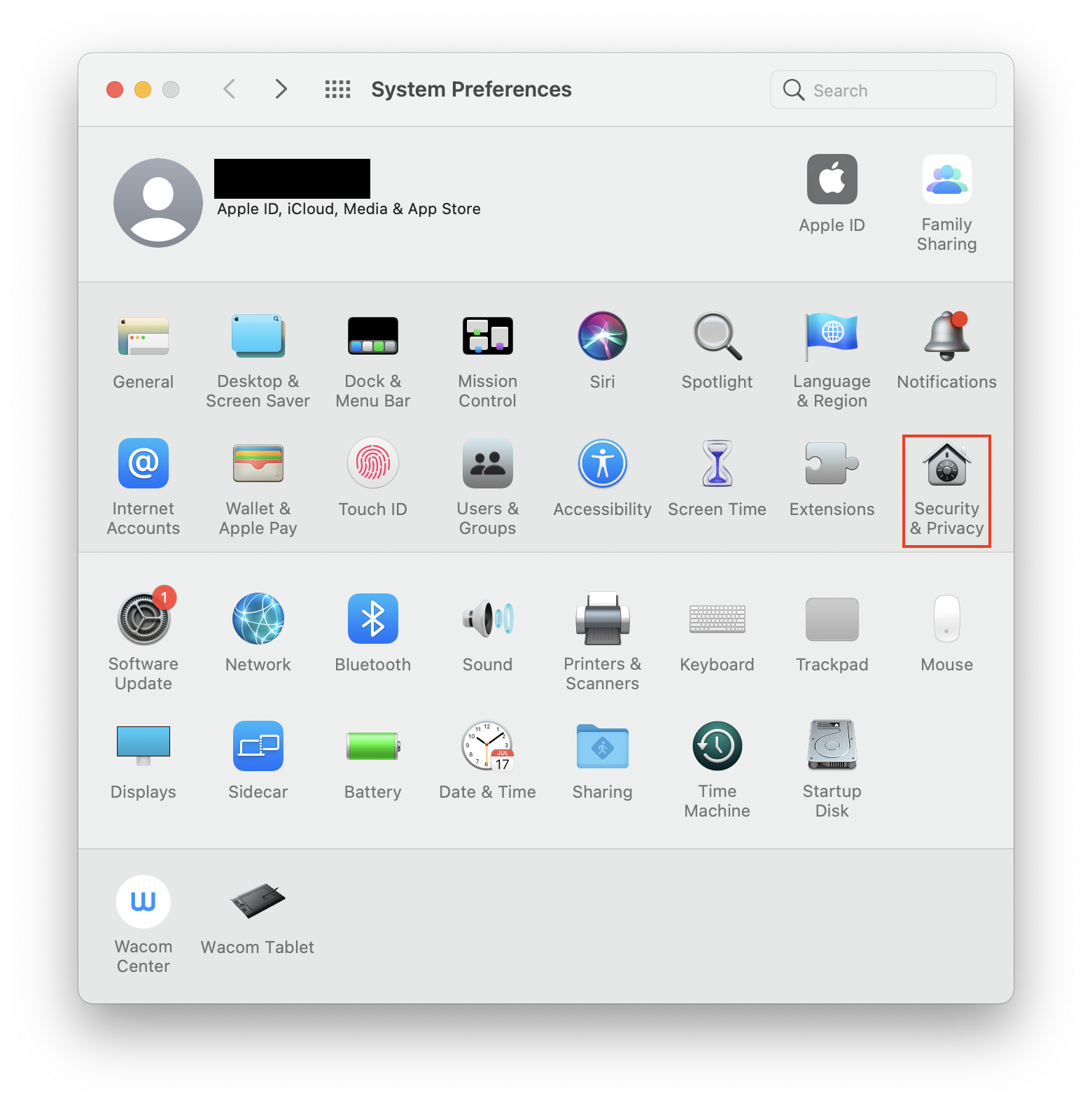
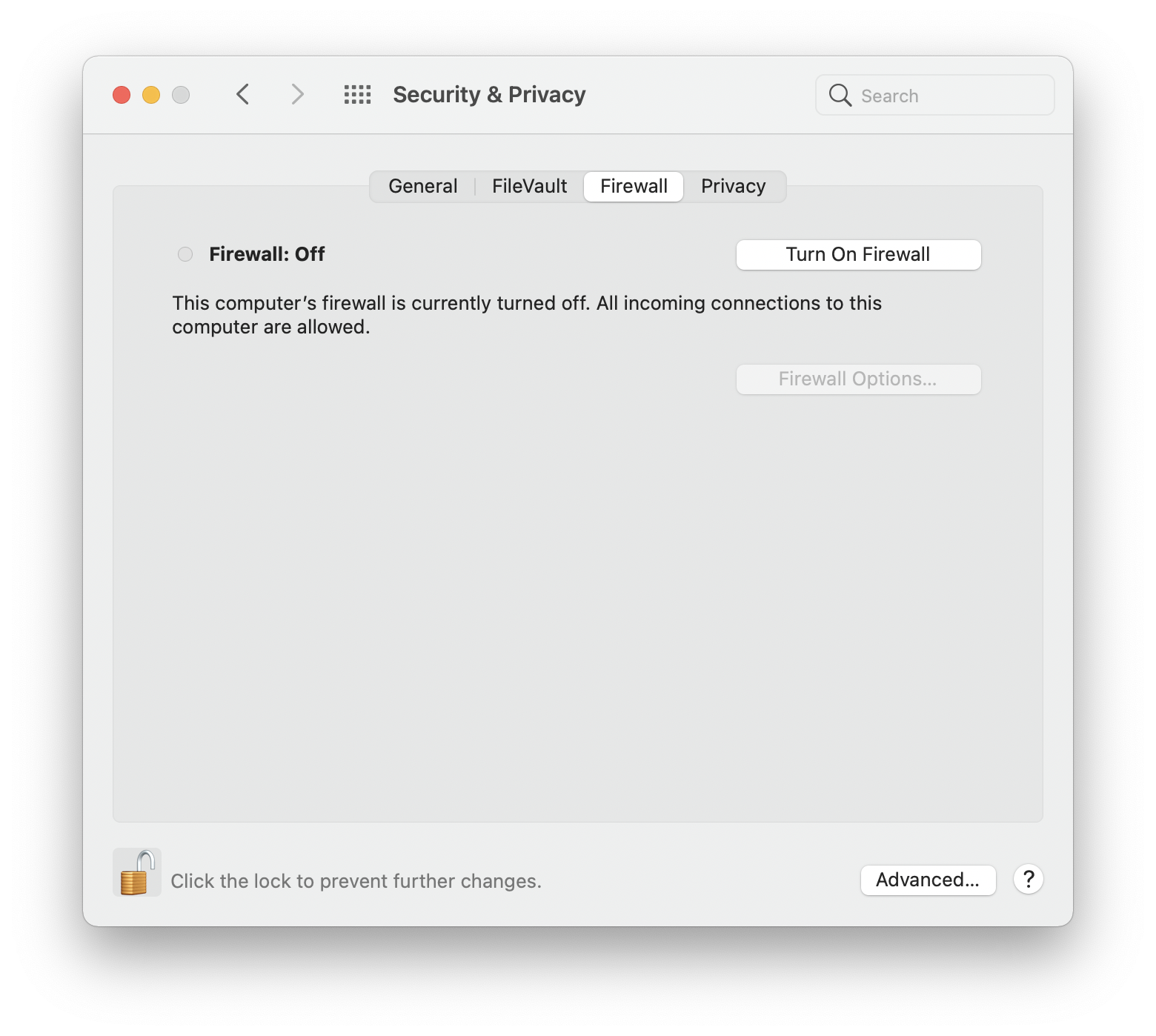
Our helpful advice: You may need to click the Lock symbol at the bottom left of the Security & Privacy window and enter your password, or you may use Touch ID to change your security settings. This stops unauthorized users from making changes to your security settings.
6. Use antivirus software
While antivirus software can’t always prevent phishing and remote access scams, it can help you deal with any malware that hackers have installed on your Mac. We recommend looking for antivirus software that offers real-time protection—this means that your Mac will be protected even if you’re not currently running a scan.
MacKeeper’s Antivirus automatically blocks malware and adware when it’s active. To turn on real-time antivirus protection, follow these steps:
- Open MacKeeper.
- Choose Antivirus from the left sidebar.
- Choose Enable to turn on real-time protection.
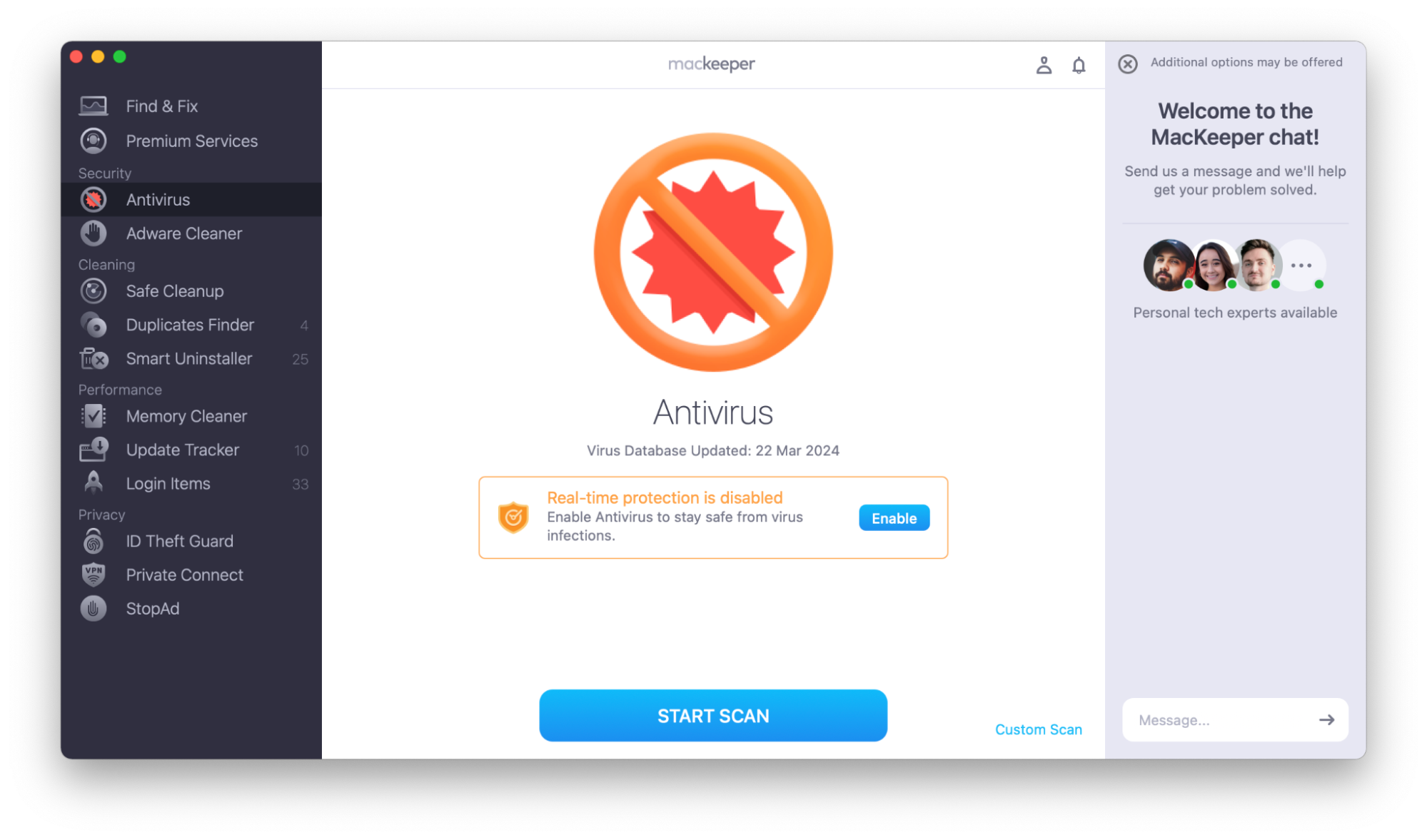
Even when you have real-time antivirus protection enabled, we still recommend running regular virus scans and dealing promptly with any threats.
7. Protect your Wi-Fi router
Some hackers target your computer and attack your Wi-Fi router to create maximum disruption in your home or workplace.
Fortunately, you can take several steps to protect your router, including:
- Change your router’s password. Many people leave their router with the default password, which may be easy for hackers to guess. Even if it’s a difficult password to guess, if a cybercriminal has access, change your password for increased security.
- Upgrade your router’s firmware. There may be security upgrades available.
- Check and disable any remote administration settings. This will stop people from getting unauthorized access to your router.
- Enable WPA3 encryption. This security standard securely encrypts passwords and protects your router and devices against brute-force attacks.
You’ll need to use a computer or other device to access your router and make these changes. If you think your current Mac has been compromised, ensure you’re using a secure device.
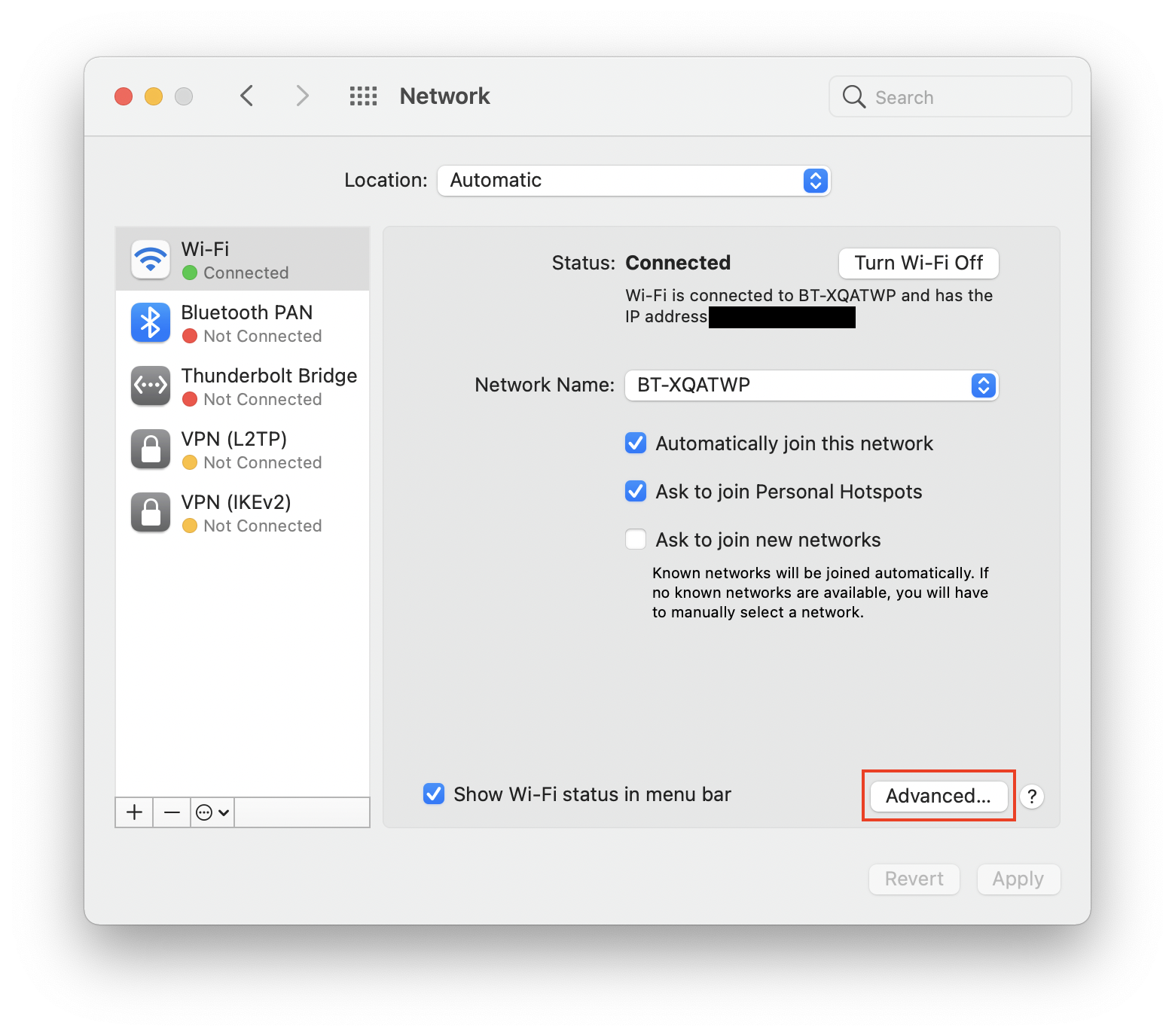
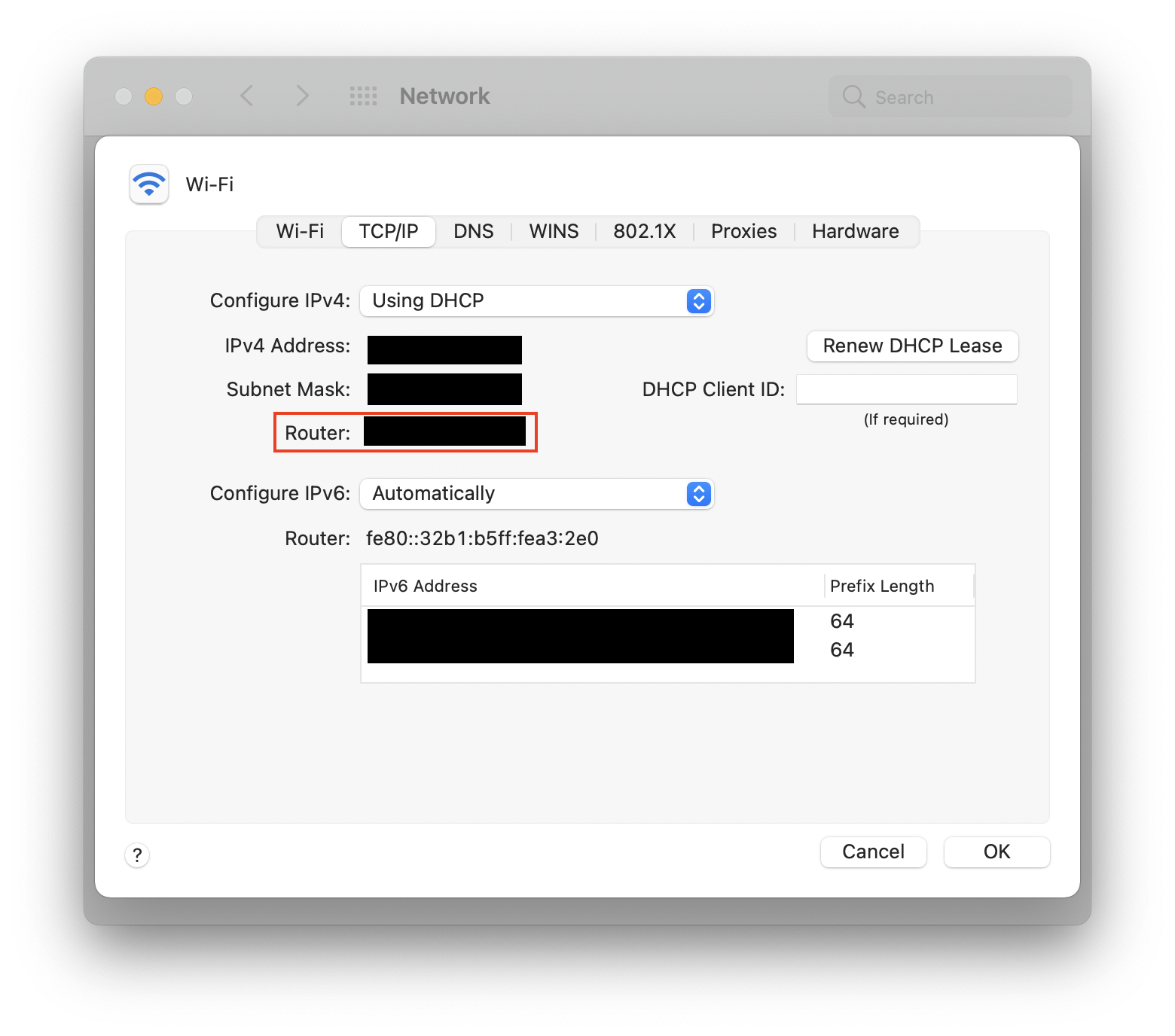
How to make changes to your router’s security on a Mac:
- You’ll need to know your router’s IP address before you start. If you already know it, go straight to step 4. To find out the IP address, go to Apple menu > System Settings, and choose Network.
- Choose Advanced.
- Choose the TCP/IP tab, and find your router's IP address.
- Copy and paste the IP address into a web browser.
- This will open your router’s software interface. You may need to log in using your router’s password. From there, you should be able to make any necessary changes.

8. Back up and wipe your device
Completely wiping your Mac is the ultimate way to remove any malware.
However, before you wipe your computer, you need to ensure that any necessary data is saved somewhere secure. Depending on how much data you have, you may choose to back it up in the following places:
- On a memory stick—if you have less than around 256GB of storage, this could be the easiest and most secure option.
- In a cloud-based storage service—however, if you do this, make sure that your passwords haven’t been compromised.
- On an external hard drive—if you have hundreds of gigabytes (or more!) of data, this could be the best choice for you.
If you’re using an external device, you can back up your data using Time Machine. To back up your device using Time Machine:
- Ensure that your memory stick or external hard drive has at least twice the capacity of your Mac. If there are existing files on the external storage, you’ll need to remove them—you’ll be prompted to do this during the backup process.
- Go to Apple menu > System Settings.
- Choose Time Machine. (Depending on the macOS version you’re running, you may need to click General and then choose Time Machine.)
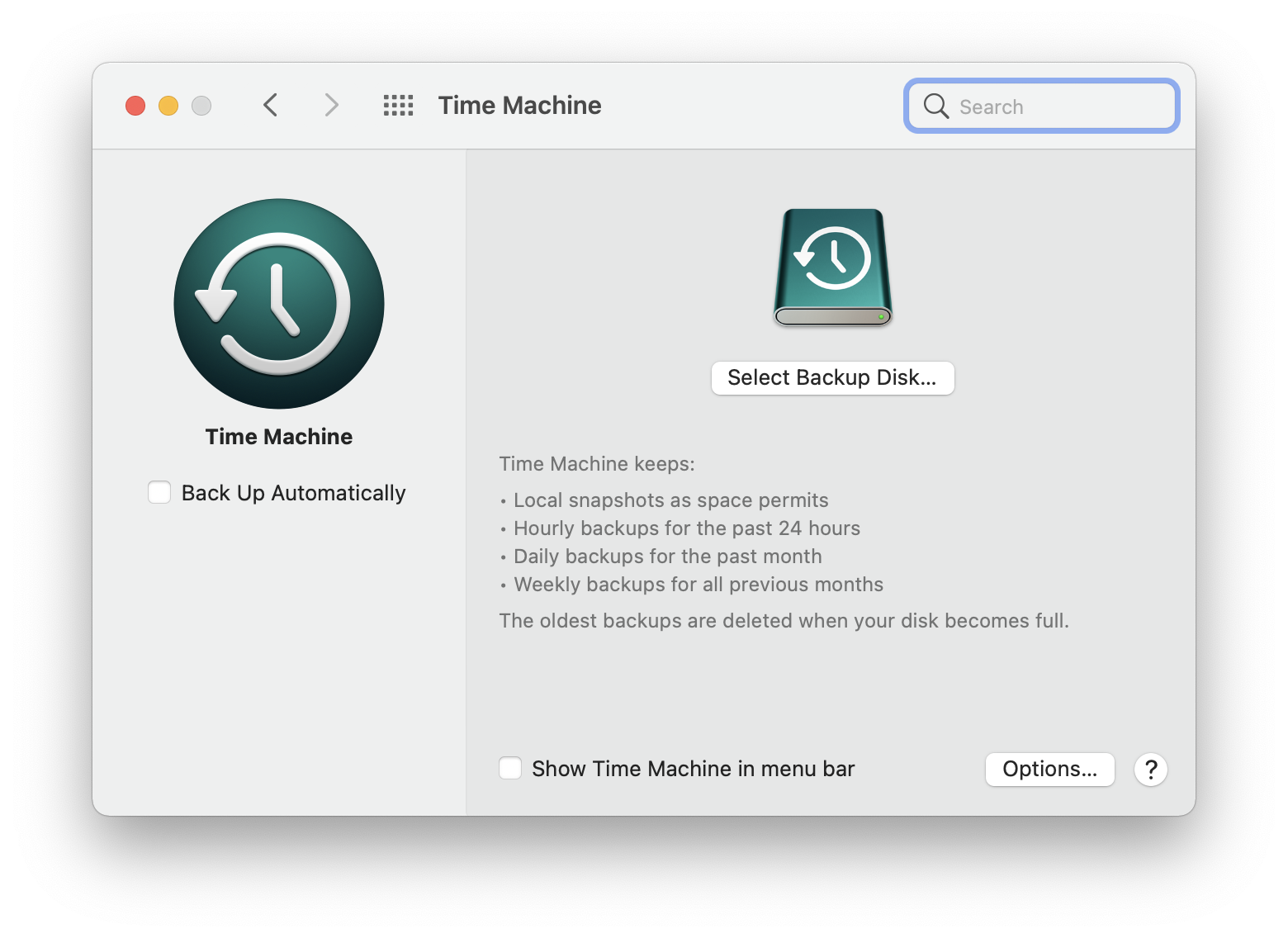
- Attach your external device, and click Select Backup Disk.
- Choose your disk, and follow the instructions on the screen to complete the process.
Once you’ve backed up your files, Mac makes it simple to wipe your device.
Here’s how to wipe your Mac if you use macOS 13 or higher:
- Go to Apple menu > System Settings.
- Choose General in the sidebar, and then click Transfer or Reset.
- Choose Erase All Content and Settings to completely wipe your device.
To wipe your Mac if you use macOS 12:
- Go to Apple menu > System Preferences.
- Choose Erase All Content and Settings to wipe your device.
Note: This feature only works on Macs running macOS 12 and higher with Apple’s silicon chip.
Conclusion
This article will help you determine if someone has remote access to your Mac. People remotely accessing your computer can be scary. The person targeting you could be a stranger on the other side of the world or a coworker, acquaintance, or partner trying to get information about your activity.
Fortunately, you can protect yourself from remote access hackers and secure your Mac so they can’t easily attack your system again.
Whether you use a MacBook, iMac, or any other Apple computer, our app can help keep your system safe. With real-time antivirus protection, a secure VPN, and the ability to quickly and easily uninstall apps, MacKeeper can help prevent someone from accessing your Mac remotely.
By following the steps in this article, we hope that you can stop someone from accessing your Mac computer remotely.