In this article you will find the following:
To define phishing, it’s one of the many ways hackers can steal private information from people and organizations. What appears to be a real email, message, or website can be a trap that steals your login credentials, credit card, and social security numbers, and much more.
In this comprehensive guide, I’ll show how phishing works, the different phishing methods, and how to recognize and protect yourself against phishing attacks.
Before we start
Checking every file you download from your emails is essential. And when it comes to Macs, it’s easy with MacKeeper’s Antivirus. Check your entire system for malicious code or files, and protect your privacy through timely notifications when the hazard of files being compromised is detected.
Here’s how to do it:
- Download MacKeeper and use the free trial to set up an account.
- Select Antivirus from the left-side menu.
- Click Start scan and wait for the virus scan to complete.
- If MacKeeper finds any malicious files, click Delete > Delete.
How does phishing work?
Phishing is a trick. It works by sending you a fake message, email, or other interaction that looks like it came from a real person, company, bank, or group. The problem is that the phishing message format and design will look legit, so you need to know how to identify the hazard.
To help you, below, we’ve explained the key schema behind phishing:
1. Creating the bait to look real
A good way to catch fish is by having the best bait. Yes, the bait can look real. However, there’s often a trick. Bait can be a malicious website urging you to provide personal information, an email asking to confirm you sign in to your online banking app, etc.
2. Sending out the bait
The next step attackers take is sending their bait to targets. Phishing is done through email, social media, phone calls, and instant messages. Remember, attackers always want to look as real as possible. They’ll impersonate your friends, family, bank, doctor, etc.
3. Harvesting your information
Once you interact with the phishing bait, the attacker collects your information to sell it, commit ID theft, or, worse, financial fraud. This information can be anything from your usernames, passwords, credit card information, social security number, banking info, and more.
4. Exploitation
After a hacker gets your information, they use it in various ways. Sometimes, they’ll sell this data on the dark web, gain unauthorized access to your bank to transfer funds, take out a loan, or steal your identity.
How to recognize phishing
How do you tell if someone's phishing you? We’ll review four safety steps to help you identify phishing bait:
- Always check the email address. Is it from a legitimate source?
- What are the To: addresses? Is there a ton of recipients?
- Check the message. Does it read unprofessionally and have errors?
- Check the hyperlinks. Is this the same organization’s website?
Look! The screenshot below is of an email from the Bank of America. Is it real?
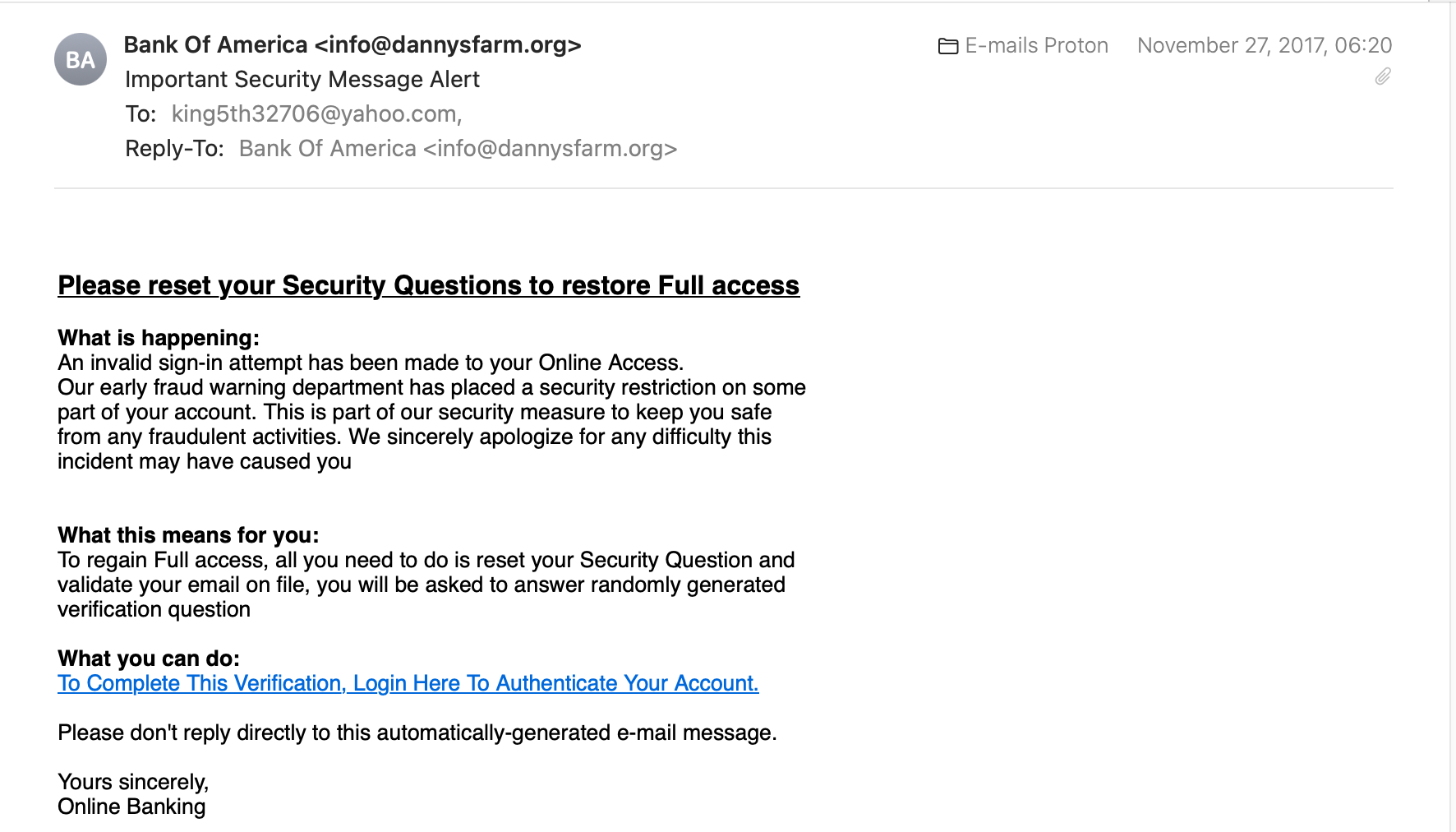
Always check the email address. Is it from a legitimate source?
We got this email from info@dannysfarm.org. What is dannysfarm.org? One thing we know for sure, it’s not Bank of America. If we do a Google search, we can see that Bank of America’s email addresses always have a domain name @bankofamerica.com at the end of their email address—for example, support@bankofamerica.com.
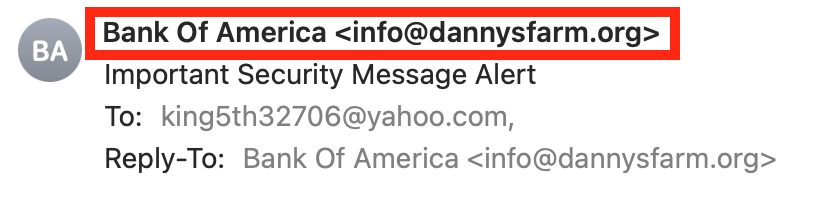
What are the To: addresses? Is there a ton of recipients?
Often, hackers want to send their phishing emails to as many people as possible to cast a wide net. Check if there are other recipients in the To: address section.
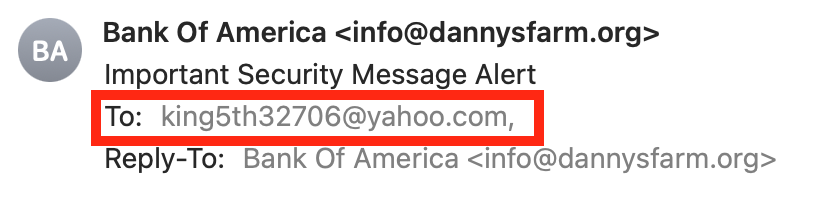
Check the message. Does it read unprofessionally and have errors?
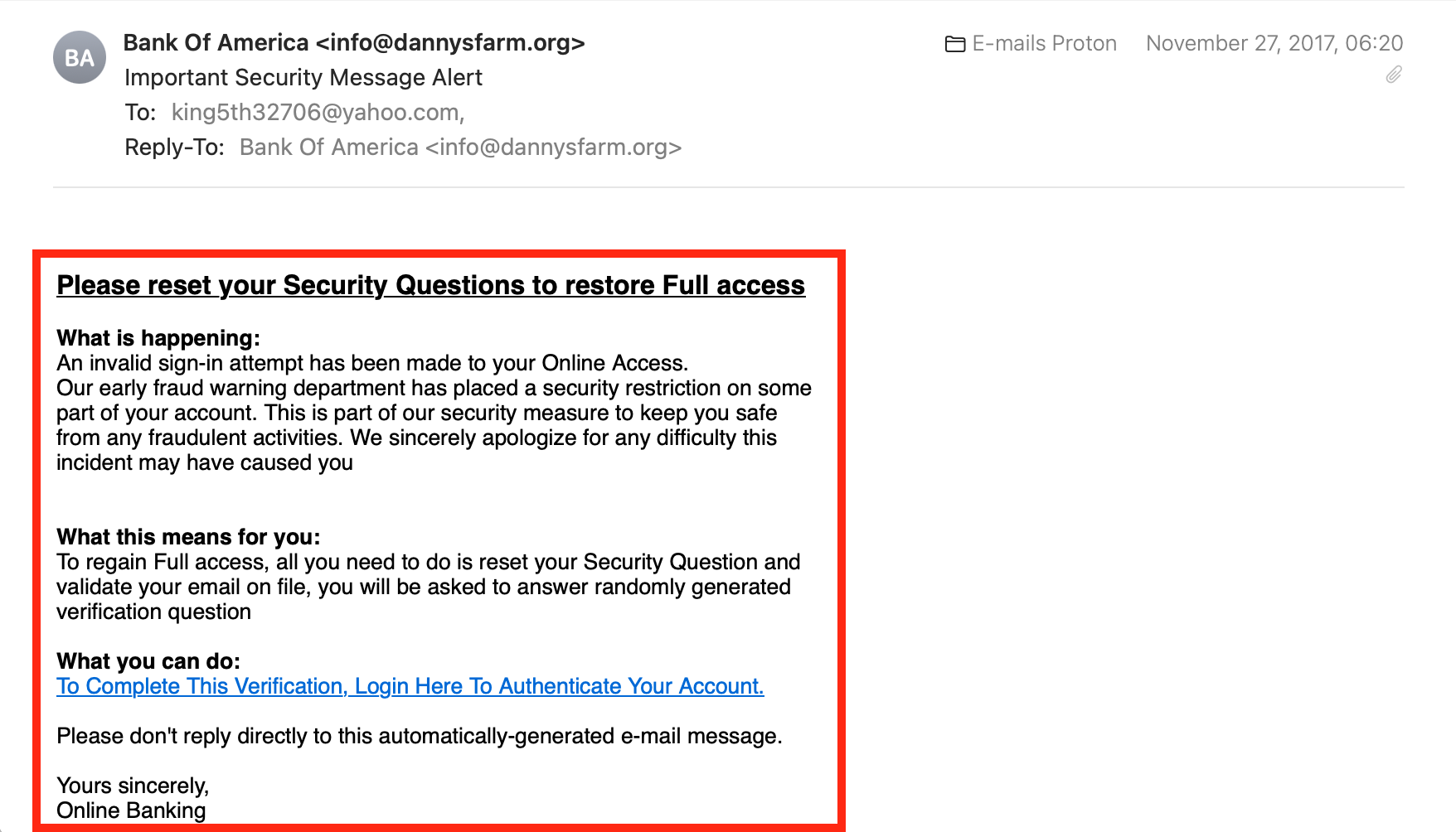
The message appears to be written poorly and unprofessionally. There’s no address to my name, unnecessary capitalization for random words, lack of punctuation, no brand design, and no signature from Bank of America. It doesn’t look official, does it?
Check the hyperlinks. Is this the same organization’s website?
We recommend you don’t click any hyperlinks. Instead, hover your mouse over the link until a popup helper window shows the URL address.
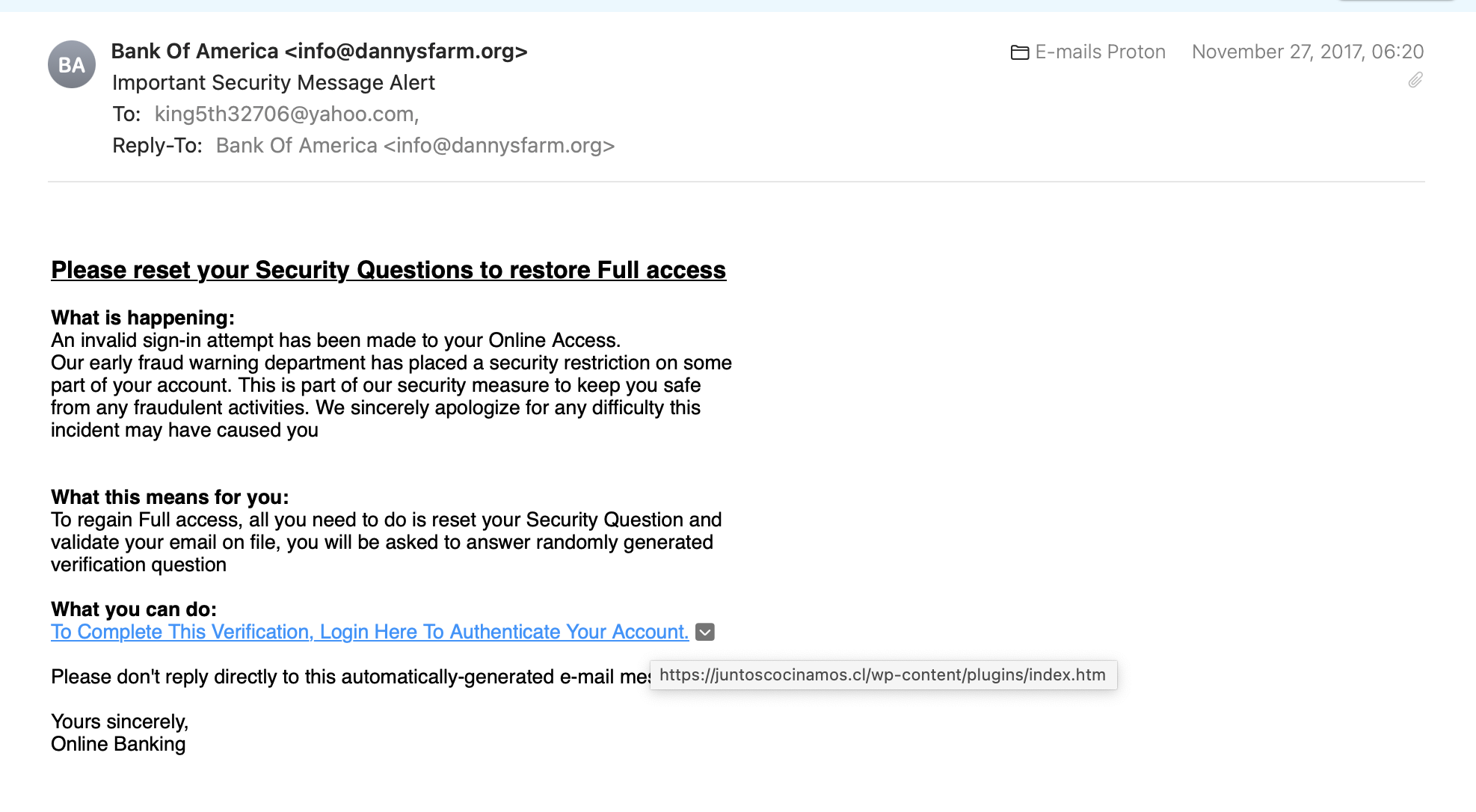
The helper popup text indicates that the website isn’t www.bankofamerica.com. Instead, we have an odd webpage URL.
Phishing gets more sophisticated than this. Below is another example of a fake but more believable phishing email. The bait is much more robust, so it’s harder to tell if it’s fake.
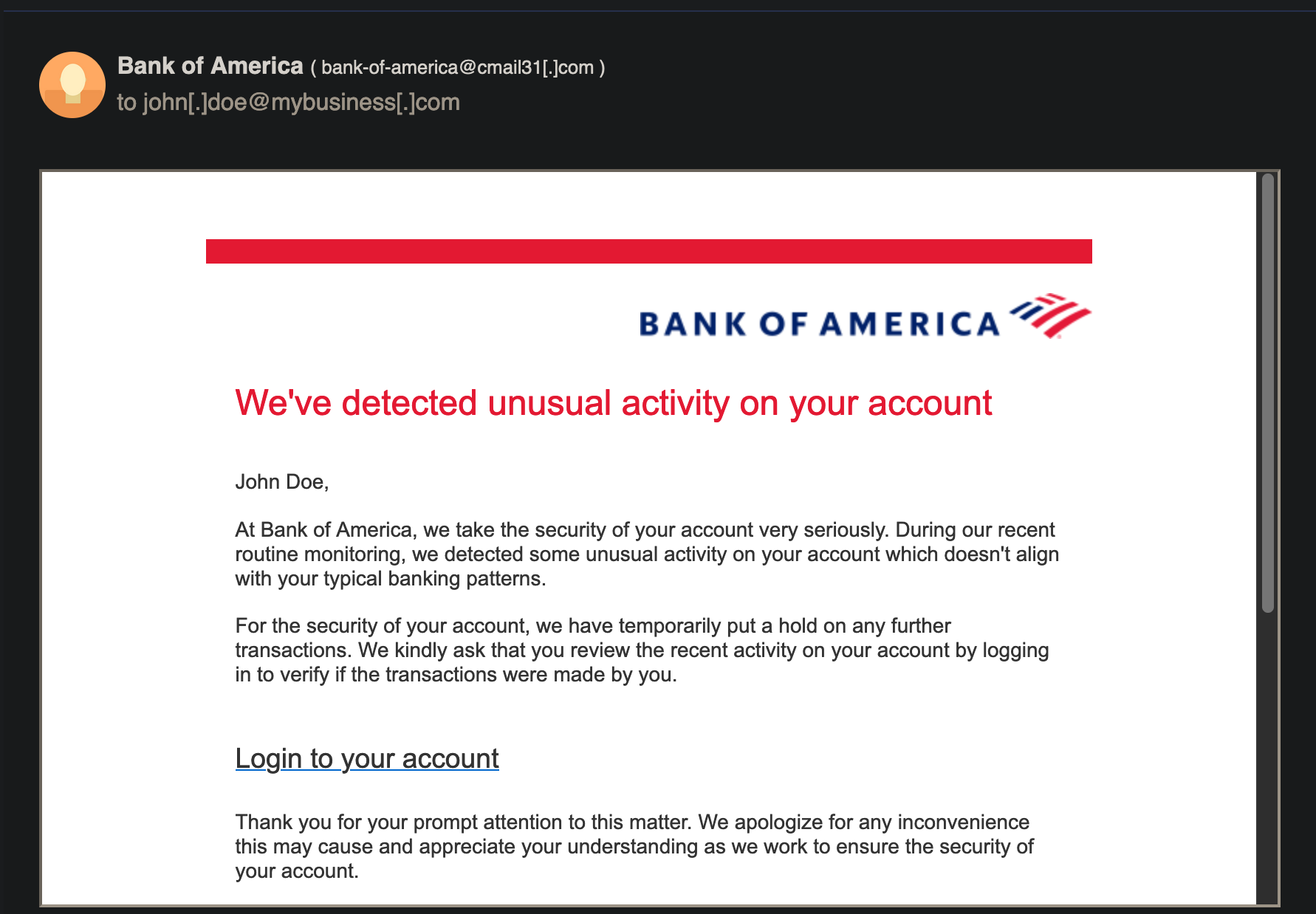
The sender's name, logo, email design format, and message look real. However, even with the best phishing e-mail message, there’s always a way to tell.
First, check the email's authenticity. Does it appear legitimate?
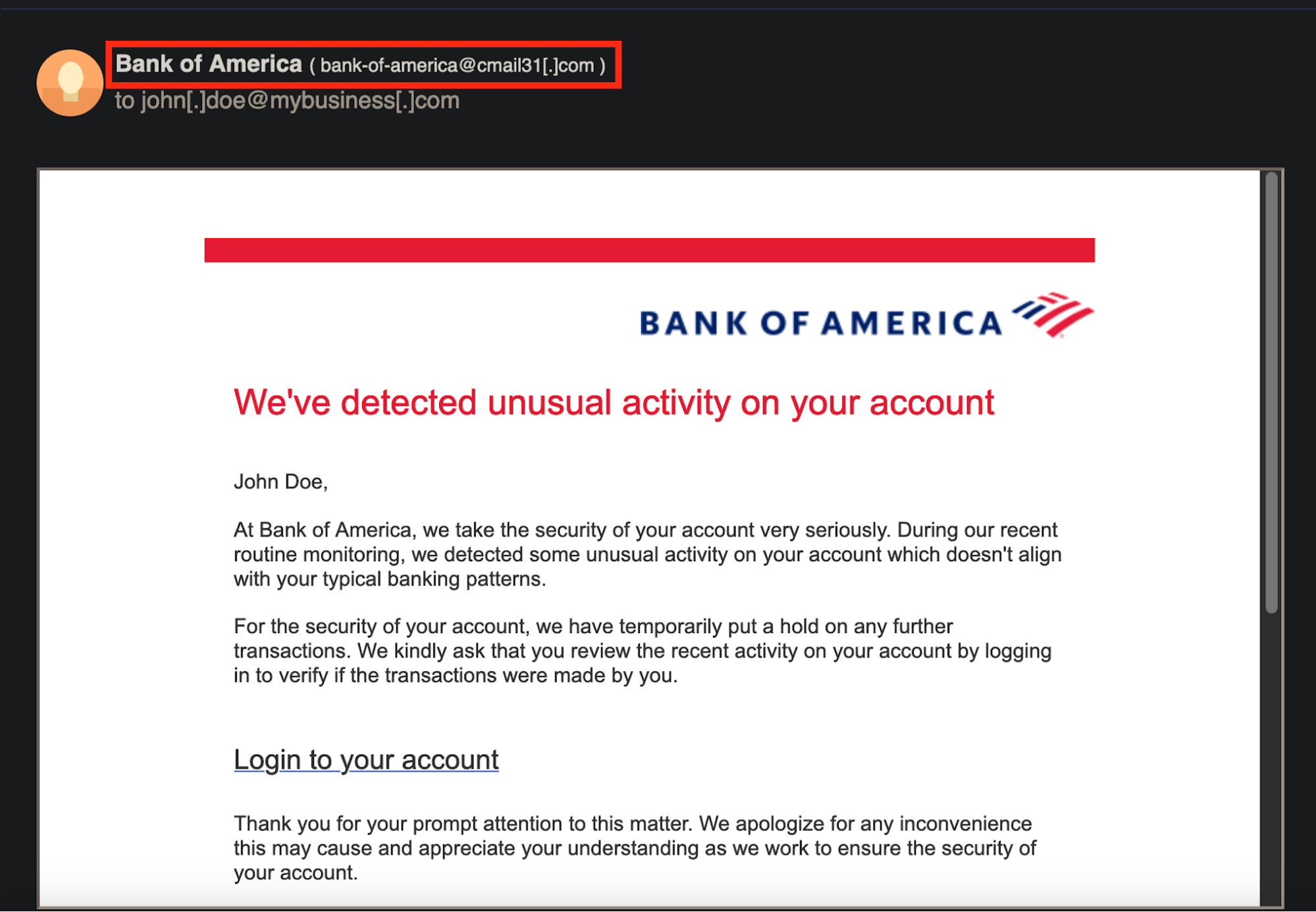
The email above reads bank-of-america@cmail31.com. Again, it’s not Bank of America. Legit Bank of America email addresses always have the @bankofamerica.com domain.
Sophisticated phishing goes beyond just an obvious fraudulent email address. Sometimes, the email addresses are less obvious and look more similar to the real thing, like in the iforgot.apple.com phishing scam. In this case, the Apple ID users are targeted with a phishing email asking them to reset their Apple ID and posing as Apple using replicated email message graphics. As a result, people got their Apple IDs taken over, leading to ID thefts and financial fraud.
Types of phishing attacks
Phishing isn’t just a fake message that looks real; there are many types of phishing to watch out for, and cyberattacks become harder to identify. I’ll show you the most common ones below
- Whaling attacks
- Pharming
- Clone phishing attacks
- Evil twin attacks
- Voice phishing
- SMS phishing
- Calendar phishing
- Page hijack attacks
- Bulk phishing attacks
- Spear phishing
- Business email compromise (BEC)
1. Whaling attacks
A whaling attack targets a big catch! Whaling attacks refer to phishing done on high-profile individuals like corporate board members, politicians, and CEOs. Hackers try to bait these individuals into giving them sensitive information.
On April 30th, 2016, popular toy company Mattel fell victim to a whaling attack. Hackers sent a fake vendor payment to a finance executive involving transferring funds that required the approval of two executives, including the Chief Financial Officer (CFO.) The payment got authorized, which led to the hackers stealing $3 million.
2. Pharming
Pharming is a phishing scam in which an attacker links a victim to a fake website that prompts them to enter their credentials or download a file that would pharm private data once on their device. In farming phishing scams, you usually spot words like “urgent,” “only today,” etc.
As early as 2007, hackers targeted 50 financial institutions globally to carry out a pharming attack. People using an unpatched version of Microsoft Windows 10 would download a trojan horse from the pharming website. The virus had the same name as a normal Windows file, making it difficult to detect. It then captured confidential data and sent it right to the attackers.
3. Clone phishing attacks
Clone phishing attacks involve creating a realistic replica of a popular website, like Facebook, Coinbase, etc. It’s also an email-based attack that involves a victim lured into clicking a link in the message.
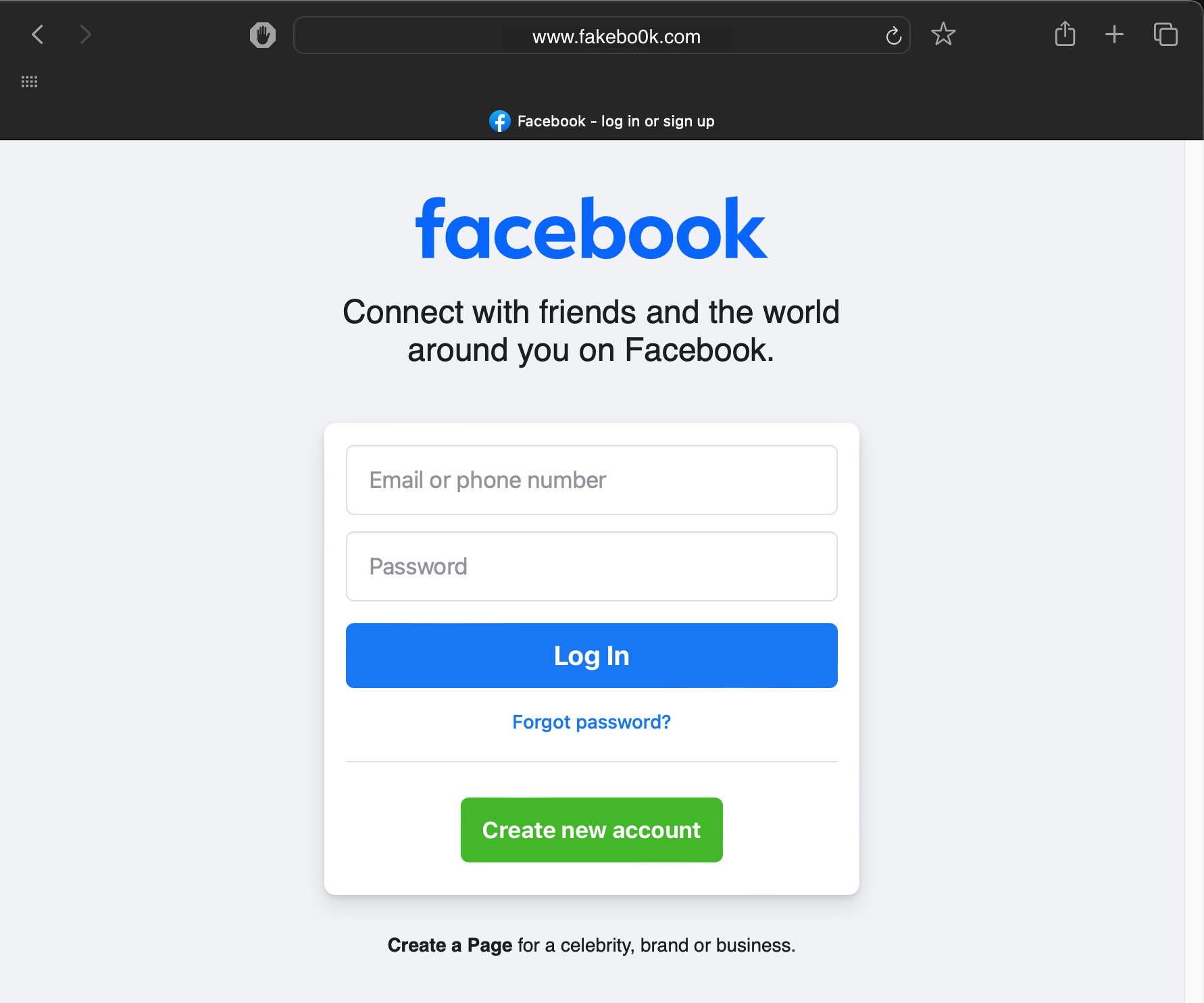
The crypto industry is no stranger to clone phishing attacks. In October 2023, scammers assembled a popular crypto trading news website, Blockworks, alongside an Ethereum blockchain scanner, Etherscan. The hackers then wrote a fake breaking news report involving a multimillion-dollar exploit, encouraging users to visit a fake Etherscan website to connect their crypto wallets. Fortunately, the hackers failed in their attempt to steal any crypto, as their attack was poorly set up.
4. Evil twin attacks
Evil twin attacks use a fake Wi-Fi network to intercept data like your name and passwords when you log in to your accounts. Usually, evil twin attacks use unsecured Wi-Fi networks that look legitimate to fool victims into connecting to these networks by enticing them with free internet.
In 2020, the U.S. Department of Interior’s networks were hacked using an evil twin attack. Thankfully, the hack was part of an internal audit by white-hat hackers from the Interior Office of the Inspector General to detect network vulnerabilities.
5. Voice phishing
Voice phishing, or vishing, involves phone calls to trick people into thinking they’re legitimate sources or family members to steal info or money. Sometimes, hackers will find ways to replicate a loved one’s voice through artificial intelligence.
In August of 2022, Cisco, a multinational digital communications technology company, fell victim to a series of sophisticated vishing attacks. Hackers were able to access databases containing private code and information on product development. Fortunately, no vital data or information was affected despite the potential for large-scale damages.
6. SMS phishing
Using SMS text messages, users will attempt to trick you into clicking on links to fake websites, virus downloads, or get you to disclose private information. SMS phishing is sometimes referred to as smishing.
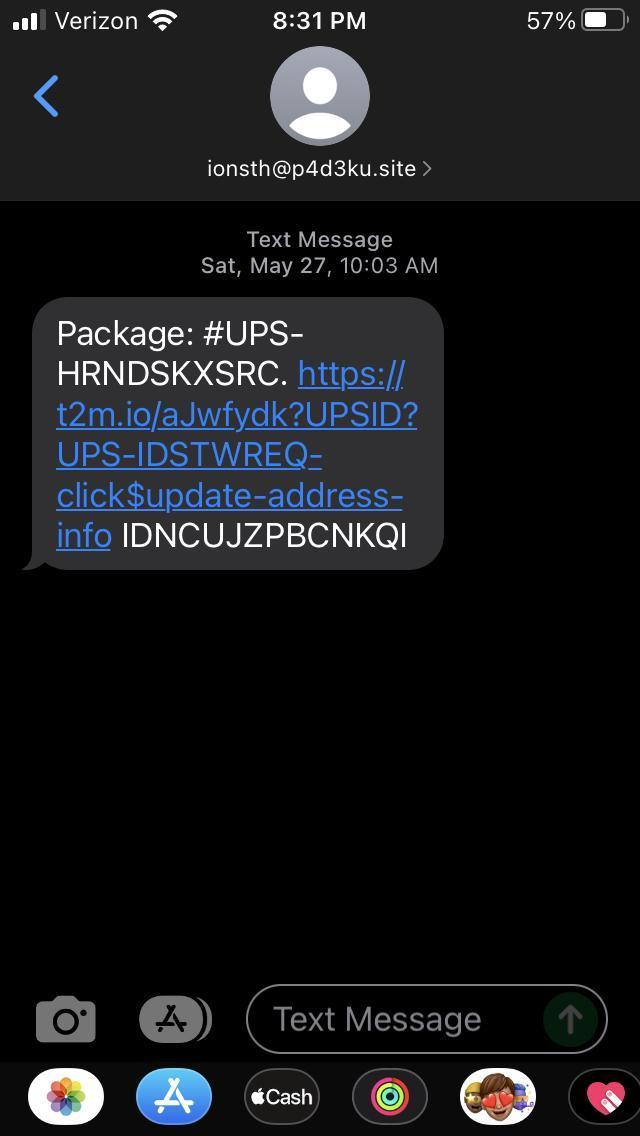
In July 2022, the Federal Trade Commission found that six percent of people who reported SMS phishing attacks fell victim to financial fraud. That same month, the FBI found that since the beginning of 2022, around 244 people lost $42.7 million from SMS phishing attacks involving fake crypto scams. SMS phishing scams occurred in popular text message applications with hackers specializing in social engineering.
7. Calendar phishing
Calendar phishing uses fake calendar invitations to trick users into clicking on malicious links and giving sensitive information. This type of phishing manipulates the user's sense of urgency.
In July 2020, a group of hackers used a calendar phishing technique involving sending multiple fraudulent calendar invites from a Wells Fargo Bank employee. The fake invitation included a Wells Fargo login page that tricked users into submitting their private information.
8. Page hijack attacks
Page hijack attacks are a sophisticated phishing method involving redirecting users from legitimate websites that have been compromised to malicious websites. These attacks are often the hardest to spot. They occur on real sites but are discovered by the link's legitimacy on their page.
9. Bulk phishing emails
Bulk phishing emails involve sending tons of phishing emails to a large number of individuals. This tactic can be deployed by finding large lists of emails online.
Hackers wait for big shopping events like Black Friday to send bulk phishing emails. One example occurred between November 1 and November 14, 2023. There was a 237 percent increase in bulk phishing emails between September 1st and October 31st, 2023. Hackers impersonated popular companies like Amazon, eBay, or Bank of America, sending emails with phishing hyperlinks to fraudulent websites to steal information.
10. Spear phishing
Spear phishing targets specific organizations or individuals from known or trusted senders to build trust and give out information. These attacks are more coordinated and precise.
Between 2018 and 2022, one hacker group began employing spear phishing attacks on banks and telecommunication services in Africa, with 35 successful attacks. They sent out emails with virus attachments that compromised company servers. Using the data from the servers, the hackers crafted realistic emails impersonating government tax offices and hiring agents, with total damages estimated at around $11 million.
11. Business email compromise (BEC)
There are two types of phishing attacks that fall under the Business Email Compromise: CEO fraud and Email account compromise (EAC).
Out of all the types of phishing listed above, business email compromises are some of the most financially damaging. Domestic and international losses surrounding BEC amounted to around $43 billion from June 2016 to December 2021.
CEO fraud
CEO fraud involves attackers pretending to be company executive officers or other board members to trick users into sending private information or transferring funds.
According to the FBI, CEO fraud scams have resulted in total damages of $26 billion. Between June 2016 and July 2019, there have been 166,349 domestic and international incidents related to CEO fraud. These complaints have shown fraudulent transfers sent to banks in around 140 countries.
Email account compromise (EAC)
Email account compromise attacks happen when attackers access an employee’s email. The attacker will attempt to access even more private information or request vendor payments.
Globally, both EAC and BEC attacks caused over $43 billion in damage. These attacks increased by 65 percent from June 2016 to December 2021 during the COVID-19 pandemic due to businesses shifting to remote workplaces.
What are the primary motivations behind phishing attacks
Phishing is primarily used to serve two purposes: collecting sensitive data like login credentials and money. However, there are other reasons hackers attempt to phish:
- Money. Attackers often attempt to acquire money by selling your sensitive data on the Dark Web or trying to convince you to send them money.
- Stealing sensitive data. Phishing usually involves trying to steal sensitive information like login credentials, credit card numbers, social security numbers, or financial information to further common financial fraud or ID theft.
- Identity theft. Attackers seek to impersonate individuals to engage in fraudulent activities like unauthorized transactions and stealing valuable data.
- Spying. Sometimes, phishing is used in state-sponsored or corporate espionage to infiltrate organizations and government agencies to acquire sensitive information.
- Social engineering. Phishing allows attackers to manipulate people with psychological tactics like threatening to reveal private information unless an action is performed.
- Sabotage. More malicious attackers will use phishing to find a way to get users fired, destroy their reputations, or liquidate their assets to cause chaos.
What is a more sophisticated form of phishing
Sophisticated forms of phishing involve making bait more believable and harder to detect. An attacker can try to find an audio of your friend or a loved one online and then attempt to recreate their voice using artificial intelligence. Or they can then trick you into believing you’re talking to someone you know and lure you into making a transaction or revealing sensitive information to the attackers.
In March of 2023, a hacker called an unsuspecting 73-year-old woman pretending to be her grandson. The “grandson” said he was in jail without a wallet and cellphone and asked for the bail money. The sense of urgency caused the grandmother to rush with her husband to withdraw 3,000 Canadian dollars ($2,207 in US currency) to send to the “grandson.”
Upon going to a second bank for more money, a branch manager pulled them aside to tell them about how another customer got a similar call, thus exposing the scam. In 2022, imposter scams were the second most popular scam in America: 36,000 reports with a total loss of $11 million.
What to do if you fall victim to a phishing scam
If you’ve fallen victim to a phishing scam, it’s important to act immediately. The faster you protect your information, the more likely you’ll minimize the potential damage. Here are some steps you can take if you become phished:
- Change your passwords immediately
- Review your account activity
- Run antivirus software to check for malware
- Report the phishing attack
- Notify your contacts
- Watch your accounts
- Learn and stay vigilant
1. Change your passwords immediately
Immediately change the password to the phished account. This could mean you’ll have to change passwords to multiple accounts to make sure hackers can’t access them. Sometimes, after you change your password, there is an option for all users to be signed out; be sure to click that if you have the chance.
Your next password should be a random set of letters (both capitalized and lowercase), symbols, and numbers. Here’s an example: $aV.14x-W1&iA!%0.
2. Review your account activity
Look into your accounts to check if the hacker made any unauthorized steps, transactions, or got access to other accounts. For extra security, note what actions were compromised so you can report the companies.
3. Run antivirus software to check for malware
Run an antivirus scan on your computer. This way, you can check if any harmful malware or virus collects your information in the background.
Use MacKeper’s Antivirus to scan your Mac for viruses:
- Download MacKeeper and take advantage of the free trial to set up an account.
- Select Antivirus from the left-side menu.
- Click Start scan and wait for the virus scan to complete.
- If MacKeeper finds any malicious files, click Delete > Delete.
4. Report the phishing attack
Report the attack to the organization associated with your account. This is often appreciated as it helps ensure the safety of other users. Report the phishing attack to the Federal Trade Commission (FTC) and Cybersecurity & Infrastructure Security Agency (CISA). Your reports can help ensure a safer future against cyberattacks.
5. Notify your contacts
Sometimes, phishing scams can gain enough information to impersonate you or acquire your contact list, thus getting others involved. Immediately tell your contacts that you’ve been phished. That way, they’ll watch out for any suspicious messages.
6. Watch your accounts
Check for any unusual behavior surrounding your emails, messages, accounts, or finances.. Depending on your account, you can sometimes receive email or text alerts about suspicious or new logins for your accounts. Google, for example, will email you when your account is logged in using a new device or at a different location than your usual login area.
7. Learn and stay vigilant
Stay aware of any follow-ups or phishing scams coming your way. Always verify emails, messages, and websites before submitting private information.
How to prevent phishing
Phishing protection has become essential for everyone and every device. You can prevent phishing attacks by following a few tips described below:
- Use antivirus software
- Use desktop and network firewalls
- Add multi-factor authentication (MFA)
- Encrypt your data
- Install an anti-phishing toolbar in web browsers
- Gateway email filter
- Web Security Gateway
- Spam filter
1. Use antivirus software
Sometimes, viruses can live on your computer’s hard drive and implant themselves in a file that can be otherwise difficult to look for. Using antivirus software like MacKeeper can help scan your Mac for malicious files.
2. Use desktop and network firewalls
Desktop and network firewalls can add an extra layer of protection and act as a shield on your device against all incoming traffic:
- Desktop firewalls are used on individual computers or devices, providing localized control over applications and traffic.
- Network firewalls are used in conjunction with larger-scaled internal and external networks, intended to safeguard multiple devices connected to a network or infrastructure like those linked to an internet router.
Both of these types of firewalls—desktop and network—allow you to see and control incoming network connections on devices.
3. Add multi-factor authentication (MFA)
Enable multi-factor authentication (MFA) for all of your accounts whenever you can. MFAs will add an extra form of verification in order to unlock your account or data.
MFAs work by sending you a push notification or a text message with a numerical code to your phone or second email, making it harder for phishers to hack into your account. Apps like Google Authenticator or Microsoft Authenticator provide a convenient and fast way to protect your account.
4. Encrypt your data
Start with your folders and file encryption to safeguard your data. You can use secured encrypted connections for your online activities and back up important files and other information to prevent any losses after a phishing attack.
5. Install an anti-phishing toolbar in web browsers
Use anti-phishing toolbars for your web browsers that will help identify and block phishing attempts. These toolbars can help provide real-time warnings and help users avoid fraudulent sites.
6. Gateway email filter
Use gateway email filters to intercept and filter out any phishing emails that come to your inbox. Gateway email filers can analyze and sort out any emails with odd content or suspicious files. Keep in mind that gateway email filtering is a more advanced admin-specific feature. For Google, this would mean enabling settings in your Google admin account.
7. Web Security Gateway
A Web Security Gateway or Unified Threat Management device is hardware that serves as a gateway between your connected devices and the internet. They’re able to use URL filters and content inspections so you can block access to harmful websites.
8. Spam filter
Sometimes, your inbox gets so many different flavors of spam. Many email clients like Google Mail or Apple Mail allow you to enable spam filters. These filters can detect and throw suspicious and spam emails into your spam folder. Also, check your spam folder in case any legitimate emails are there.
What is spam? Learn all about spam and the dangers it holds in our blog.
Is it better to block phishing emails or report them
It’s important to both block phishing emails from hackers and report them to the property cybersecurity authorities. Doing so helps with stopping phishing in the future.
Screenshotting a phishing email can be used as evidence and a learning tool for counter-phishing measures. You can then submit the screenshot image of the email to the proper authorities, such as the Federal Trade Commission and Google Safe Browsing.
Also, block the agents sending you phishing emails to prevent the attacker from further communicating with you.
Why is it so important to report phishing attacks immediately
When it comes to phishing attacks, timing is everything. Reporting phishing attacks as soon as possible helps with creating a faster response and awareness. Authorities can then take action to investigate, identify, and protect people from phishing attacks. When you send a report, you contribute to the collective effort to inform others and defeat phishing attacks. If you’d like to learn more, you can see our article on how to prevent cybercrime in eight easy steps.
Conclusion
Phishing means sending you emails or messages pretending to be a legitimate company or person to trick you into giving them your private information. All is done to fool you and steal your money, identity, or security.
Prevention is key—use MacKeeper’s Antivirus to scan all files that you download on your Mac for malicious code. Plus, you can also benefit from MacKeeper’s ID Theft Guard feature to scan your emails for potential leaks.