In this article you will find the following:
If something is as unwanted or as annoying as spam, then it may sometimes be tempting to feel sorry for it. Yet, when this unsolicited content starts cluttering up your inbox and device, it’s time to take action.
BEFORE WE BEGIN
If you want your device to be spam-free and run as smoothly as possible, then you should try MacKeeper’s ID Theft Guard. This is a data breach monitoring tool that scans the dark web to check if your email address was involved in any data leaks. If any leaks are found, ID Theft Guard alerts you, so you can take action and secure your email.
The whole idea is to protect your personal information, like your credit card information, and prevent you from becoming a victim of identity theft. Start monitoring your email address with MacKeeper’s ID Theft Guard in these few, easy steps:
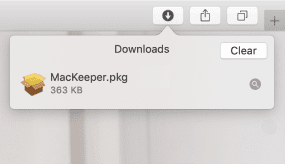
- Download MacKeeper on your Mac
- Select ID Theft Guard in the left pane
- Click Scan new email, enter your email address in the text box, and click the Start scan button.
That’s it. You can now rest assured that you won’t be blindsided in the unfortunate event that your email address is breached.
What is spam?
As online users, we see spam all the time when browsing, on social media, or directly in our inboxes. But what is considered spam?
Well, spam is any form of unasked for digital communication that is distributed in vast quantities to an array of different online users. Spam is the message itself while spamming is the act of distributing these messages. Anyone who sends this kind of content is known as a spammer.
Although it is usually sent to someone as an email, the definition of spam can expand to include unasked for content shared via social media, text message or even phone calls.
You’ll probably be familiar with the spam you often see in your inbox. The latter usually takes the form of a promotional email and while you can usually distinguish them from real messages, you still need to be careful when engaging with them. Some are harmless promotional content, but others can be fraudulent or even part of a malicious attempt to trick you into handing over your personal details.
Why is it called spam?
Spam may be a potential nuisance or threat to online users, but the roots of the word have a more humorous source.
If you remember the hit British TV show, ‘Monty Python,’ then you’ll likely remember the infamous skit where a group of Viking diners pronounce:
“Everyone must eat Spam—whether they want it or not.”
In this instance, Spam refers to the canned pork product.
In the same way, anyone who has an email address, can be targeted by spam—whether they want it or not. When used with a lowercase ‘s’, this word refers to the annoying digital communications that we’re all too familiar with.
Types of spam
Spam can come in many different spam types, some more harmful than others. From emails offering you deals that seem too good to be true to messages asking you to respond in relation to topical news stories. The thing is, it can often be challenging to differentiate between what emails are real and what are spam.
Here, we have identified some of the main examples of spam to help you stay safe online:
- Spam emails
- Phishing emails
- Malware spam
- Tech support scams
- Social media spam
- Current events scams
- Advance-fee scams
- Spam texts & calls
- SEO spam
Now let’s find out how to distinguish one from another.
Spam emails
If you use email, then you’ll probably be all too aware of spam in your inbox.
This is the most common variant of spam you’ll see, usually diverting your attention from genuine emails you actually want to read. The positive is that many email providers not only allow you to filter through these spam messages but block many of them too.
Phishing emails
Spam can take the form of phishing emails distributed by cybercriminals to try and trick online users into handing over sensitive details such as their passwords to an online account or financial details. iForgot Apple scams are a good example of this.
Information these scammers want to access can include a bank account number, date of birth, credit card details, or anything else that could identify someone when online.
Check out how many phishing emails are sent daily.
Malware spam (malspam)
Any malware spam is usually sent to a computer or mobile through a spam email or text message. Cybercriminals will include any variant of malware in their message, ranging from spyware to a trojan.
Learn how to get rid of malware on Mac.
Tech support scams
We are all aware of how invaluable IT experts can be, especially when we’re experiencing an issue either online or with our hardware. We rely on this support to get us out of sticky situations, which is why tech support scams can be so effective in deceiving online users.
These kinds of scams usually start with someone pretending to be from a legitimate company getting in touch regarding a problem with your device. Their aim is to convince you to hand over control of your device to a remote operator. If this happens, then they’ll be able to access your sensitive information and every part of your computer or tablet.
Social media spam
Social media platforms, such as Twitter and Instagram, have become some of the most popular online. So while they attract a huge amount of users, it makes sense that cybercriminals are attracted to them too, potentially as an opportunity to target individuals with bots, spam and dodgy social media accounts. Much of this type of spam aims to increase traffic to a spammer’s website or convince an online user to reveal their personal information.
Current event scams
We’ve all witnessed a period of unprecedented volatility from the conflict in Ukraine to the impact of the pandemic and the recent earthquake in Turkey and Syria.
For spammers, these kinds of seismic events offer opportunities for them to take advantage of such news to further their own ends. For example, you may well be targeted by a spam text or call asking you to donate money to a fundraising campaign for anyone impacted by a natural disaster or war.
Advance-fee scams
As an email user, you’ve very likely to have firsthand experience of this kind of spam. Often dubbed the ‘Nigerian prince’ messages as this used to be the supposed identity of the sender, this spam type promises a huge financial incentive for a user in exchange for a cash advance.
Sometimes, the person requesting money will masquerade as a family member to make the recipient more likely to hand over their cash. The idea is that this initial sum can be paid in exchange for unlocking a far greater financial reward. But of course, as soon as this first payment is made, the benevolent individual requesting financial assistance will disappear.
Spam texts & calls
Spam texts and calls will often be unsolicited, perhaps asking you to visit a website or click on an unverified link. If this message comes in the form of a text, then this is known as ‘smishing,’ a combination of SMS and phishing.
Usually, you’ll be able to report these calls as spam communications or block these numbers from contacting you. Even so, some can get through so you need to be vigilant when receiving messages.
SEO spam
SEO spam is also known as ‘spamdexing’ and is a way for cybercriminals to use search optimization techniques to boost the ranking of a spam website when listed by a search engine. This can take the form of:
Content spam
In some instances, spammers will populate their website with many popular keywords in a bid to ensure their site ranks highly when certain search terms are input into Google. Other examples include utilizing pre-existing and engaging content to drive traffic to their site.
Link spam
Link spam is when a post on an online forum or a blog comment is filled with irrelevant links. In this scenario, the spammer is looking to use backlinking to increase the traffic to their website.
How to identify spam?
Phishing scammers can target any of us at any time but this doesn’t mean you should spend less time online to stay safe. Instead, you just need to familiarize yourself with some telltale signs that a message or social media post could be from a spammer.
Let’s delve into a few of the most common to help you enhance your defenses and protect yourself online.
Email attachments
It’s sensible to always be wary of opening an email attachment, particularly when it comes from a sender you don’t know or is unfamiliar. Using anti-malware software, like MacKeeper’s Antivirus, can help you scan any attachments to ensure they’re safe to access.
Suspicious credentials
A very effective way of verifying the legitimacy of an email sender is to review their email address. If they’re supposedly from a real organization or company, then their email address should match with the website address.
For example, if someone claims to be from PayPal and asks for money, yet their address is example@123456tytuy.net, then it’s obvious something is wrong. More cunning scammers may be less obvious about their intentions by using an email such as example@pay1al.co.uk. Both should ensure that alarm bells ring.
Inserted links
If you get a link in an email or text, then you should always be wary of where this might take you. If it supposedly comes from a company such as LinkedIn or Facebook, where you already have an account, then you can head to the website, log in and see if there are any messages waiting for you. If there aren’t, then you should dismiss the email or text as spam.
If you’re unsure and want to verify the authenticity, contact the company. If you have any doubts, avoid the message and avoid clicking on the link.
Errors in the email text
We can all make grammatical errors or spelling mistakes when writing an email. However, if you are supposedly receiving a message from a big company such as a tax authority or Google, then this should make you think twice about its validity. Many of these organizations have marketing teams dedicated to refining their communications and it’s extremely unlikely that they would share anything with a mistake in it.
Missing personal details
If you receive a message from a verified company, then they'll usually have your personal details on file and address you by your name.
However, if you receive an email and they fail to include a personal greeting, then you should think twice about its authenticity.
In many instances, scammers will want to alarm you and ensure you take action without considering the potential consequences. It means you should try and be careful, look at your email message thoroughly and, if anything seems off, be very wary of how you respond.
Offers that are too good to be true
Scammers know that one way of getting a user to click on a link or open an attachment is by including a tempting offer in their message. The aim is to dupe a reader into clicking so the offer could be something such as a highly coveted prize or even free cash. In the heat of the moment, we might be tempted to click but sometimes you need to take a minute and consider the message rationally. If it’s too good to be true, this could be the truth and you should consider it as a warning sign.
What is the difference between spamming and phishing
This difference between spamming and phishing is in the reason behind a message being sent.
Spammers aren’t often out to hurt you. Instead, they have a product to sell and have chosen spamming as the best way of promoting their service. Admittedly, this might not be great quality or fraudulent, but that is the extent of their ambitions.
On the other hand, phishing scammers are looking to use their email to extract personal information or infect your device with malware. This could be used to commit fraud or identity theft.
Why am I getting spammed?
Many of us are exposed to spamming due to the way that companies use the data of their customers. In a perfect world, we would hand over our personal information to our favorite businesses and we’d only hear from them when they have a great product for us to invest in.
However, the reality is that many businesses sell their customer information to advertisers and other third parties. The spammers use this information to send bulk emails as it’s a cheap way of contacting recipients. Even if only a few respond, the spammers will benefit.
The situation has changed, particularly following the passing of the General Data Protection Regulation (GDPR) by the European Union in 2018. Many companies have decided to avoid the processing of customer data by third-party organizations. However, this rule doesn’t apply to all of them and some businesses still adhere to nefarious business practices.
How can I stop spam?
There are some very simple tips to follow if you want to reduce the amount of spam you are exposed to. They include:
Mark your emails
You can train your spam filter in your email account to recognise spam messages by going through your inbox. If you come across anything in your spam folder that is legitimate, then move it to your regular inbox. This will help it work out what it should block and what it shouldn’t.
Report on spam
The majority of email hosts will give you the option to report messages as spam and this will help your account recognise what is authentic and what is a spamming attack. If you have an email account without this detection function, then you could enhance your privacy by switching to one that does.
Use an alternate email address
If you’re concerned about the amount of spam you receive and your ability to differentiate between legitimate and scam messages, then it’s worth signing up with an alternate email address. This way, you keep all your ecommerce correspondence separate from your personal messages and limit your exposure to potentially harmful messages.
Your personal information is for your eyes only
One of the most effective ways of avoiding spam is by keeping your contact details to yourself as much as possible. Rather than sharing this information online via your social media profiles, do what you can to ensure this information is private.
Scammers often spend time looking for these contact details online. By not sharing them anywhere, you’re making it harder for them to target you and enhancing your online security measures.
In a perfect world, you’d never receive spam or worry about scammers making your life difficult. Unfortunately, that’s impossible. However, you can use MacKeeper’s ID Theft Guard to safeguard against hacking and identity theft.