Viruses, worms, ransomware, adware. Just a few of the potential threats we all face online. Whether you’re on a Mac, a PC or mobile device, there are many ways cybercriminals might target you. Often these hackers do it for fun, but a lot of cybercrime is motivated by financial gain. That includes phishing, a threat quite unlike the ones we’ve mentioned so far, but one that can result in big losses for victims.
In this article, we’ll look at what phishing is and how you can protect yourself from it. And we’ll give you some examples of real-life data breaches.
What is a phishing attack?
Phishing is a type of social engineering. In other words, it’s a psychological technique designed to make people carry out a certain action. In the context of cybersecurity, criminals trick victims into divulging their personal or financial information, so they can access victims’ accounts.
As you can probably guess, the name plays on ‘fishing’, because victims are caught and reeled in like fish. The ‘ph’ spelling is a nod to phreaking, the 1980s practice of hacking phone lines to get free calls.
There are a few types of phishing attacks, but they all follow this basic principle.
1. Phishing via email
A typical example of a phishing attack might see a victim being emailed by fraudsters claiming to be the victim’s bank. Within their email, the criminals will instruct the victim to log into their account using the link they provide. This will take the victim to a replica of their bank’s website, built by the criminals. If the victim falls for this trick, they’ll enter their login details, which then get sent to the scammers, who use them to steal from the victim.
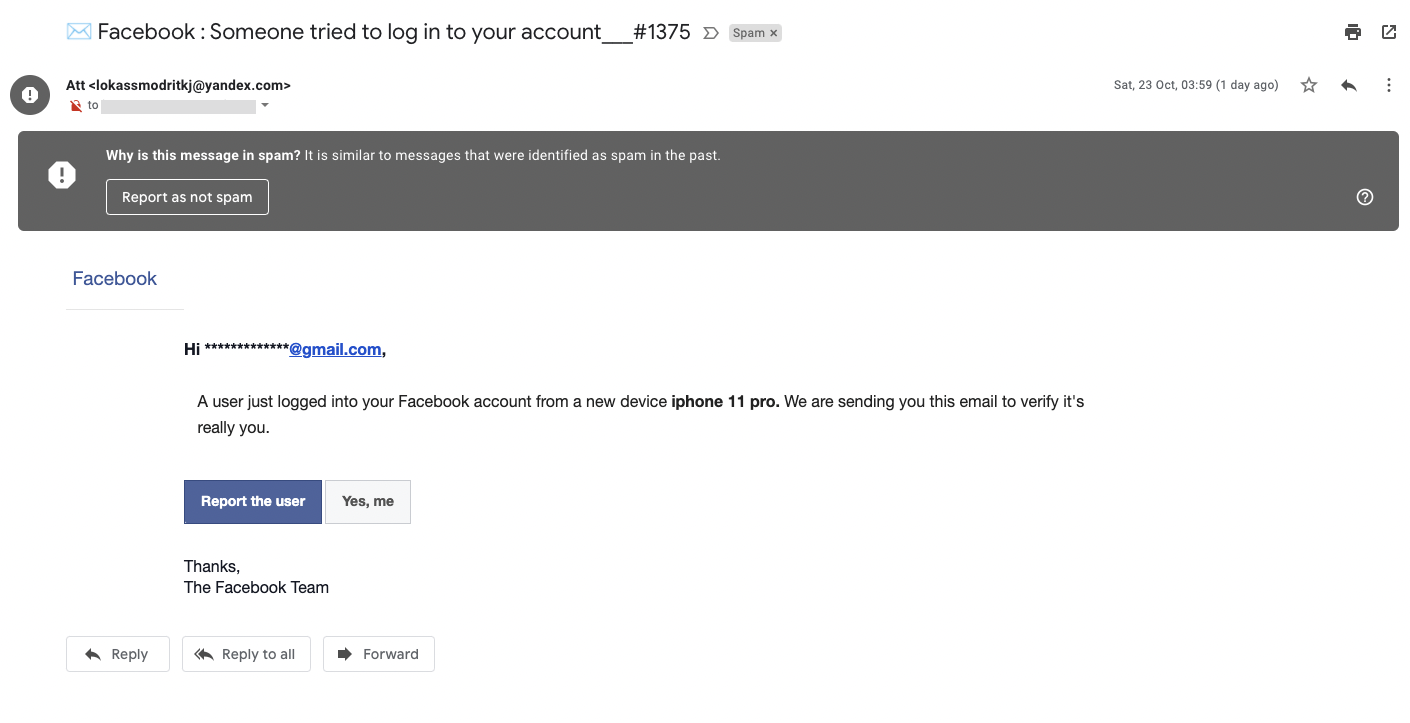
Other phishing scams see criminals stealing login details for email or social media accounts, then locking out the victim. The hackers might then demand a ransom.
There are, thankfully, a few things you can do to avoid email phishing attacks:
- Check email senders’ addresses. Scammers will often email from addresses that have nothing to do with who they’re pretending to come from. But be aware that sender email addresses can be faked too
- Don’t follow links in emails if you can avoid it. If an email asks you to log in to an account, don’t use a link in the email to get there. Instead, type the address into a web browser manually and log in as normal
- Look at the language in the email. Often, cybercriminals will use poor or broken English. If you get an email from your bank, for example, and it’s full of spelling errors, it’s probably a scam
- Look out for generic greetings. If you get an email that starts with something like “Dear customer”, it’s not likely to be legit. The sites and services you hold accounts with know what your name is, and they’ll use it if they contact you
- Don’t reuse passwords. Should you fall for a phishing attack, the scammers will likely try your login details with other services, meaning you could be attacked in multiple places
- Use two-factor authentication on your accounts. Even if criminals get your login details, they won’t be able to access your accounts easily without your phone
2. Spear phishing
Spear phishing is essentially the same as regular phishing - but with one big difference. With regular phishing, fraudsters send out phishing emails en masse to huge lists of email addresses. With spear phishing, it’s a more targeted effort. The email will be addressed directly to you. It will probably purport to be from someone you know.
Generally, spear-phishing emails will be sent to workplace email addresses. Often, they’ll target someone with access to financial information and bank accounts. But they might also try to get you to reveal your company email password or to get access to the workplace network.
Unfortunately, thanks to the rise of corporate websites and social networks like LinkedIn, criminals can easily find out which people hold key positions within businesses. And they can then guess what your work email is.
One well-known case of spear phishing saw Sony employees targeted with fake Apple ID emails. Once they’d stolen those login details, they used them to guess credentials for Sony’s internal systems.
To avoid falling victim to spear phishing, you can do a few things:
- Look for out-of-character language or behavior. Has your boss emailed you using your full name instead of the short version as usual? Is their language more formal than you’re used to?
- Speak on the phone or in person. Quite simply, if you’re ever in doubt about a request, get confirmation by calling or speaking to that person in person.
- Follow the usual rules for avoiding phishing. So make sure to check sender email addresses and avoid clicking links you’re unsure about.
- Use two-factor authentication to protect your accounts, wherever possible.
3. Whaling
Quite simply, whaling is spear phishing targeted at high-level employees like CEOs and COOs. So hackers will use phishing techniques to steal the login details of these ‘whales’, giving them the power to potentially steal billions of dollars or completely take over systems.
Because whaling targets are worth so much, the criminals might also accompany their scam with additional tactics. They might follow up with a phone call, for example, pretending to be someone with authority or influence, like a supplier or important customer.
Of course, if you’re not an executive-level employee or business owner, you’re not going to be targeted for whaling. But if you are or if you’re, say, a personal assistant or secretary to someone like that, you need to be able to spot attempted whaling attacks.
The losses from successful whaling attempts can be huge. In 2016, the aerospace company FACC ended up wiring €52 million to criminals, which led to the firing of its CEO, Walter Stephen.
To guard against whaling, follow the same kind of steps you would to protect against spear phishing:
- Look out for unusual behavior. Think about who’s sending you emails and whether their language and behavior are in keeping with what you expect
- Check the sender’s email address. Does it look like it normally does?
- Don’t click links in emails if you’re at all suspicious of them
- Phone or speak to people in person to confirm they actually emailed you
- Protect your accounts with two-factor authentication
4. Vishing
Vishing means ‘voice phishing’. As its name suggests, it involves criminals phoning up victims and getting them to give up information or take other action that benefits the criminal. A common example is when fraudsters phone you pretending to be from your bank. They’ll say there’s been suspected fraud on your credit card, so they need to reset it, but they need you to confirm your login details.
Like spear phishing, vishing can also be targeted, giving the criminals an air of legitimacy. That’s what happened to guests of the Ritz hotel in London, who found their credit details stolen as a result.
To protect yourself, follow a few basic principles.
- Never give your login details or PIN numbers to someone over the phone. A legitimate contact would never ask you for them
- Keep your calm. Visher may try to pressure you into doing something. They might claim it’s urgent that you take action. Those should be warning signs
- Use caller ID, if you have it. But be aware that criminals can easily buy phone numbers that appear to be local to you, even if they’re based elsewhere
- Wherever possible, make sure you have two-factor authentication enabled
5. Smishing
Smishing is phishing via text messages. The principles are exactly the same as other types of phishing. It can be targeted or it can be a scattergun sort of attack, sent out to many different potential victims. Either way, the idea is to get people to take a particular action, to reveal secret information or grant access to a secure account.
With practically everyone owning a phone, it’s no surprise smishing is on the rise.
The methods to protect yourself from smishing are straightforward:
- Don’t open links sent to you from unknown numbers
- Check the number of the sender. Google it to see whether it’s legit
- Look out for bad grammar or spelling
- Consider whether the message seems out of character for any reason
- Use two-factor authentication wherever you can
6. Pharming
Pharming is when criminals redirect your web browser to fake versions of websites to steal your login information or other important data. To make this work, your computer or mobile device needs to be infected with malware. Or the criminals need to change the settings of routers or wireless access points. Once this is done, the redirect can happen. So you might enter examplebank.com into your web browser, but it’ll take you to a fake version set up by the criminals.
Pharming is particularly dangerous because you can do everything you’re meant to avoid phishing and still get phished.
Protect yourself from pharming by following these steps:
- Don’t install software from sources you don’t completely trust
- Make sure your router’s firewall is turned on
- Install antivirus software on your devices and run regular scans
- Secure your accounts with two-factor authentication
- Don’t open email attachments from addresses you don’t recognize
What to do if you think you’ve been phished
Of course, it’s best to avoid becoming a cybercrime victim in the first place. But unfortunately, many phishing victims don’t realize what happened until it’s too late. They find out when their money is stolen or they can’t log into their accounts. If you do think you’ve fallen for a phishing scam but haven’t seen any consequences, you may still be able to protect yourself.
- Firstly, the quicker you respond, the better. With any luck, even if your details have been stolen, the criminals may not have used them yet
- Start by contacting your bank if you think your credit card or bank account might be at risk. Block your cards and order new ones. Change login details, if possible
- Next, change any passwords you think might be affected. If you’ve reused the same password anywhere else, change it there too, setting unique passwords in each case
- Consider contacting the police. They might not be able to do anything, but it could be important if you need to claim compensation from your bank later
- Scan your devices for malware. This can help to protect you from pharming attempts
Read more: