In this article you will find the following:
What is spear phishing
Spear phishing is a form of fraud where cybercriminals target a specific person or business in a phishing attack. It’s one of many different types of phishing. It can pose a serious threat to individuals and organizations.
Unfortunately, this means they’re often successful.
Cybercriminals may pose as coworkers, family members, or trusted organizations such as your bank or government agencies. They may ask for personal information, tell you to transfer money, or encourage you to download malware.
Note from our experts: Not all targeted phishing attacks take place online. Scammers may also use text messages or phone calls.
In this article, we’ll explain spear phishing, how it works, and how you can stay safe.
A note from our experts:
Here's how to use Antivirus:
- Download MacKeeper and install it on your Mac.
- Open MacKeeper and select Antivirus in the left navigation bar.
- Click Start Scan.
- Delete any malicious files.
How does spear phishing work
Spear phishers put in some research time before beginning their scams.
Nowadays, it’s easier than ever to find information online. If you use Facebook, LinkedIn, or other social media sites, scammers may see where you work, live, and contacts. Your organization’s website or LinkedIn page may have a list of executives.
Once a scammer selects their target, social media and company websites can give them all the information they need to sound like a reputable contact. They rely on these social engineering tactics to sound trustworthy.
How does spear phishing work?
- Scammers research their targets online.
- They attack, emailing them and posing as a contact.
- They might ask for personal details, send links to fake login pages, or ask for urgent payments.
A note from our experts:
Here's how to use Antivirus:
- Download MacKeeper and install it on your Mac.
- Open MacKeeper and select Antivirus in the left navigation bar.
- Click Start Scan.
- Delete any malicious files.
Signs of spear phishing attacks
Fortunately, there are some common signs of spear phishing scams. Do any of these apply to the email you’ve received?
- Haste without reason
- Invalid email address
- Mistakes in text
- Attempts to obtain private information
- Links with a suspicious address
- Strange attachments
1. Haste without reason
Have you received an email that’s asking you to do something urgently? It might set an unrealistic deadline or claim that a payment is late. It may say a friend has lost their wallet or passport, or their phone is about to die—anything that pushes you to act quickly.
Cybercriminals know that giving you time to think also gives you time to reconsider. They’re more likely to get what they want if they tell you to act fast.
Hint from our team: These tactics can also be used for phishing scams over the phone—some scammers convince their victims to immediately withdraw money or purchase items for them.
2. Invalid email address
If the email claims to come from someone you know or trust, check whether the address is right.
If you aren’t sure what the correct address is, do a Google search. You may learn that emails from your bank will come from an email address ending in @bankofamerica.com, so if you’ve received an email that looks different, it may be a targeted phishing attack.
3. Mistakes in text
Official emails from reputable companies should be well-written. At the very least, everything should be spelled correctly!
Look at the email and ask yourself:
- Is your name spelled incorrectly?
- Are there other spelling mistakes in the text?
- Are there grammar mistakes, or places where the text just doesn’t sound right?
If you’ve answered yes to these questions, the email might be a phishing scam.
4. Attempts to obtain private information
Does the email ask for personal information? It may encourage you to open a link and fill in your details or download an attachment containing a form. Some emails may claim this is so you can receive a tax refund, send money to a relative, or update your company’s payroll records.
These might all be signs of targeted phishing attacks.
Even if the email appears to come from a trustworthy person, don’t share your bank account information, credit card details, or social security numbers unless you can verify that it’s genuine.
5. Links with a suspicious address
If there are any links in the email, do they go where they claim?
Important: Hold your cursor over the link to find out the address.
Cybercriminals might make fake login pages, forms asking for personal information, or sites asking you to make a payment. If an email claims to come from your bank or a trusted retailer, links in the message should take you to their website. If they don’t, the email could be a scam.
6. Strange attachments
Are you expecting to receive an attachment? Does the email explain what the attachment is? And does it sound plausible, coming from this sender?
Be wary of forms that ask for personal information, bank details, or information about your company.
If the sender claims to be someone you trust, contact them directly to ask about the attachment before opening it or following instructions.
Attention: Remember, even if it’s not a phishing email, attachments may still contain malware.
How to scan email attachments for malware before opening them:
- Save the attachment, but don’t open it.
- Open MacKeeper.
- Go to Antivirus and choose Custom Scan.
- Select your file, and choose Start Scan.
- If the file is infected, delete it.
How to prevent spear phishing
Much of the advice about preventing spear phishing scams is similar to the guidance on how to prevent phishing in general.
However, because spear phishing targets you as an individual or a member of an organization, it’s easy to let your guard down. That’s how so many victims get tricked each year.
Here are some guidelines to reduce your risk of becoming a victim of a targeted phishing attack:
- Be careful opening emails from strangers
- Security awareness on the internet
- Learn what the basic spear phishing tactics look like
- Multi-factor and adaptive authentication
- Security software
- Use VPN
- Keep your software up to date
- Use a password manager
- Use strong passwords
- Install antivirus software
1. Be careful opening emails from strangers
When you receive an email from a stranger, look critically at it. Are they asking you to do something for them or give them information? Have they included suspicious links or attachments?
However, as we’ve seen, even emails that appear to come from trusted contacts can be part of a spear phishing scam.
2. Security awareness on the internet
A lot of cybercriminals research targets on social media. We’re not advising you to stay off social media entirely, but you should be conscious of the phishing security risks.
Staying safe on social media means the following:
- Look at your privacy settings. What information can others see? Can they see your contacts before sending a connection request?
- Be careful who you add to your networks. Avoid connecting with strangers.
- Be thoughtful about what you post. Limit the personal information that you post, so scammers can’t use it against you. Listing your company on LinkedIn might be important, but you can avoid mentioning your child’s school.
3. Learn what the basic spear phishing tactics look like
In this article, we’ve explained what spear phishing is and how to spot some of the techniques.
Spear phishing relies on the fact that we want to trust and help people. But stay wary—remind yourself of how people may try to steal information or harm your system.
4. Multi-factor and adaptive authentication
Some scammers may get information about you by hacking into your email or other online accounts. Making it harder for cybercriminals to access your accounts can reduce this risk.
Multi-factor authentication requires you to use more credentials than just a username and password—perhaps an authentication app on your phone.
Adaptive authentication asks for more credentials when you log in from a new location or device.
5. Security software
When people think of security software, they may think of antivirus protection. However, security software can do much more.
Some Mac security software contains features such as:
- Real-time malware scanning and removal as the basics
- Cleaning services such as smart uninstallers, duplicate file finders, and ways to find and delete unwanted files
- Performance-enhancing features, including ways to remove login items and clear your Mac’s memory
- Privacy features, such as information about data breaches and ID theft, and VPN services
MacKeeper includes all of these. Its easy-to-use scans will let you know quickly whether your Mac has been compromised.
Install and use MacKeeper to keep your Mac safe:
- Download MacKeeper.
- Open the installer file and follow the instructions on the screen to install it.
- Open MacKeeper from the menu bar, Launchpad, or Dock.


6. Use VPN
A VPN (virtual private network) can increase your security online, making it harder for hackers to track you. It won’t stop people from researching your social media or sending unsolicited emails, but it can stop cyber criminals from watching your browsing habits.
How to use MacKeeper’s VPN:
- Open MacKeeper.
- In the left sidebar, choose VPN Private Connect.
- Choose your server location, and click Turn On.
7. Keep your software up to date
Software companies regularly update their software to patch security vulnerabilities. Download the latest versions to ensure you’re not leaving your computer vulnerable to cybercriminals.
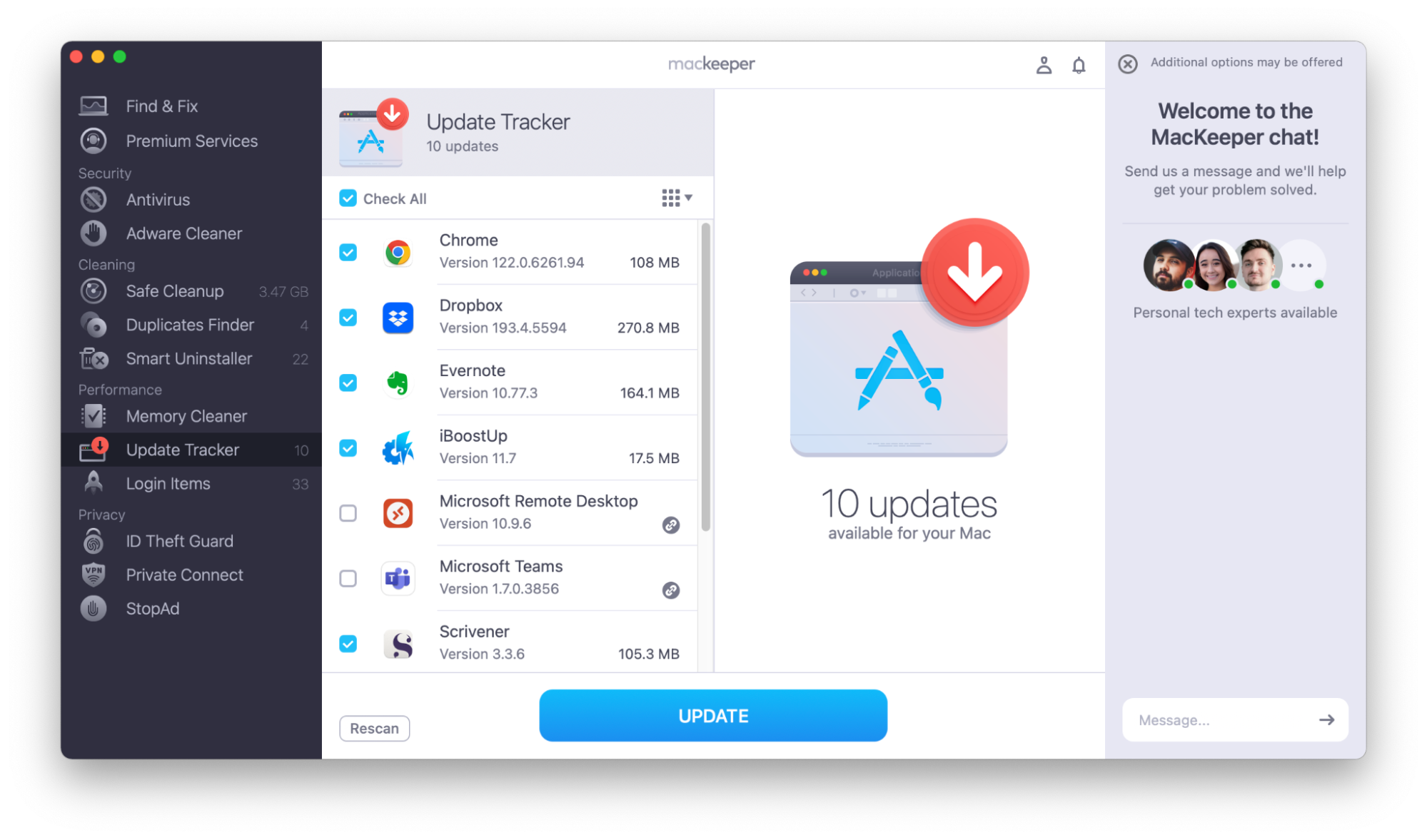
MacKeeper has a handy Update Tracker that helps keep your software current.
Use MacKeeper’s Update Tracker:
- Open MacKeeper.
- In the left sidebar, choose Update Tracker.
- Look at the app updates available, select the ones you want, and choose Update.
8. Use a password manager
It’s important to use strong passwords and not repeat the same one—if one password is breached, hackers won’t have access to all of your online accounts.
However, we know that it can be hard to remember multiple passwords. Fortunately, password managers can help. They store your passwords, and you only need to remember the password for the password manager!
Your browser will probably have an in-built password manager. There’s also a variety of free and paid options available to download.
9. Use strong passwords
Even if you don’t use a password manager, make sure your passwords are strong.
Top tips for strong passwords:
- Don’t use the same password on multiple websites.
- Make your password long—the CISA recommends at least 16 characters.
- Don’t use anything easy to guess, like your child’s name or your birthday.
- Use a mixture of upper and lower case letters, numbers, and punctuation.
- Replace letters in a word or phrase with numbers or punctuation—make it easy for you to remember but hard for someone else to guess.
10. Install antivirus software
Antivirus software can’t prevent email scams, but it can help if you’ve fallen victim to a scam and downloaded malware. Scan your Mac regularly.
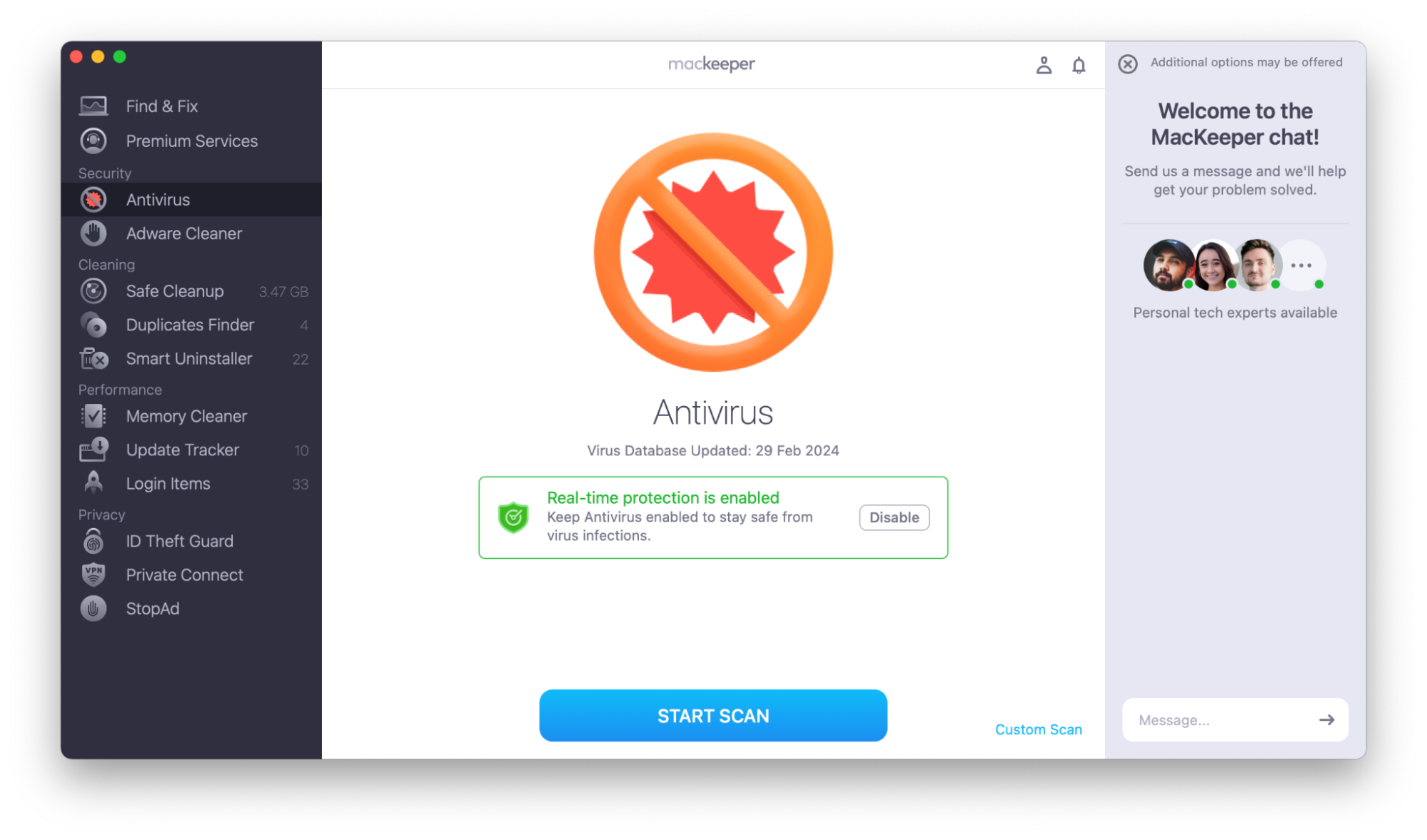
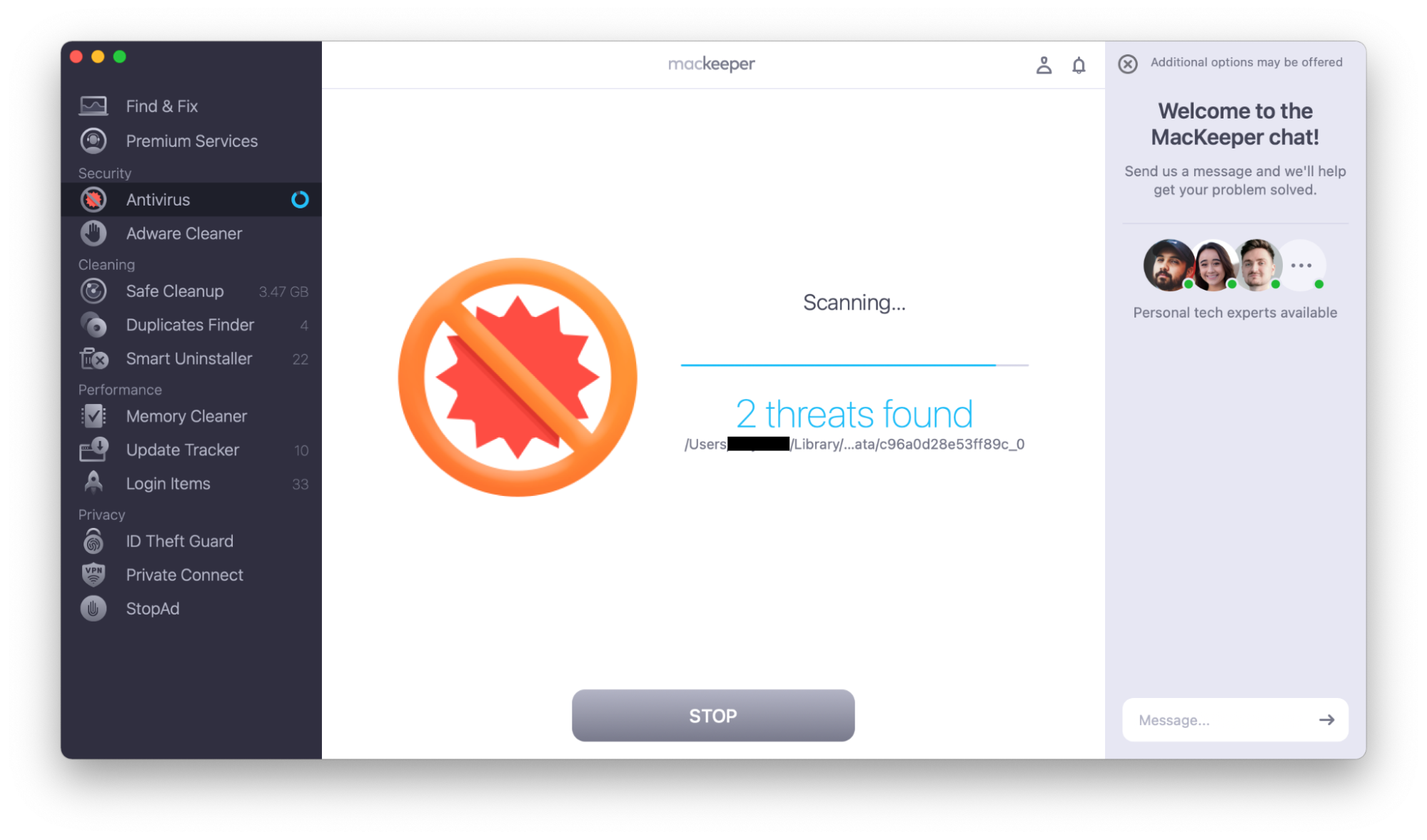
Use MacKeeper’s Antivirus to check for malware:
- Open MacKeeper.
- Choose Antivirus in the sidebar.
- Click Start Scan.
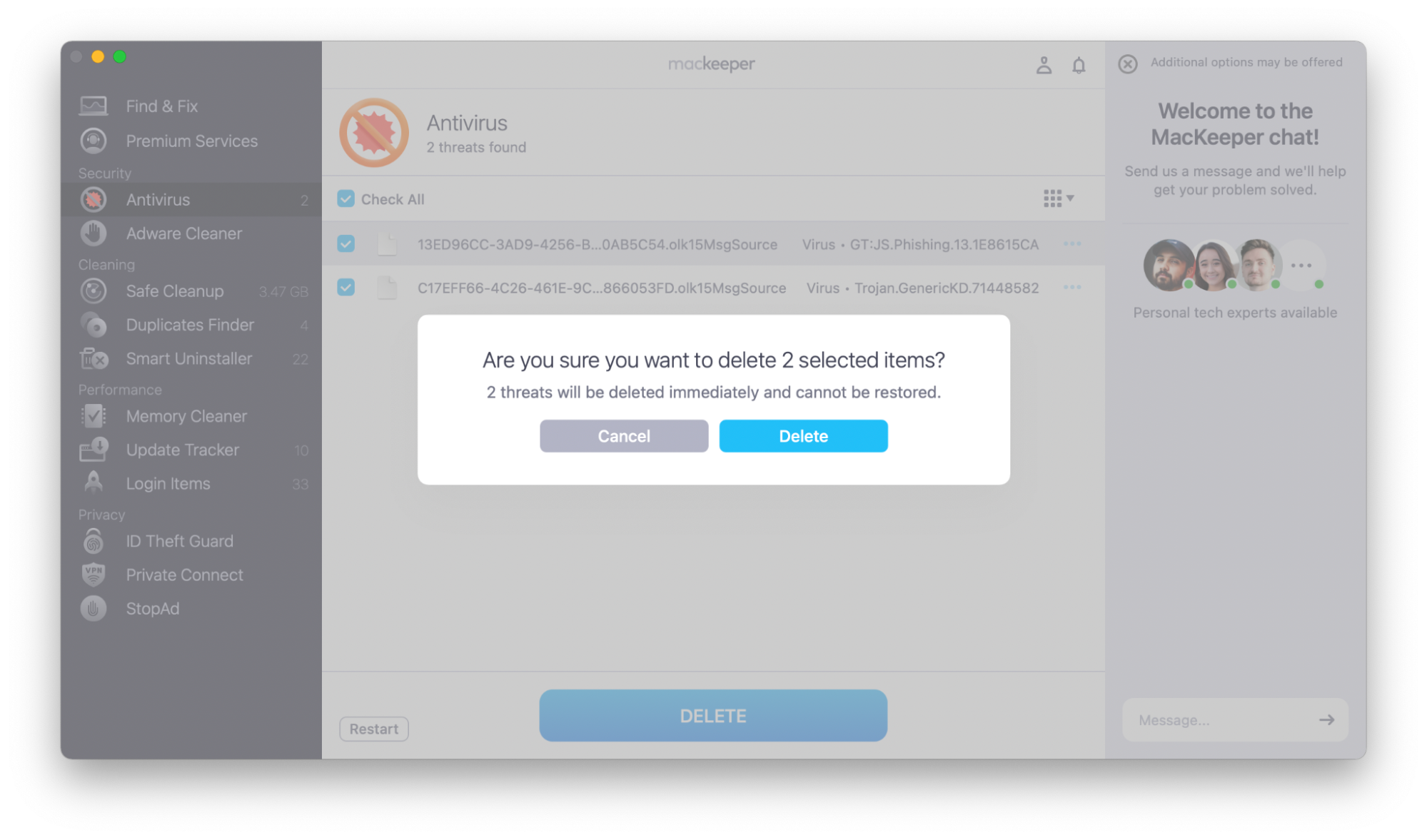
- If the scan finds any malware, choose Delete.
The difference between phishing and spear phishing
Phishing is a scam where someone poses as a trustworthy person or organization. They may want to steal money or information or install malware on your system. They usually contact many people at once. However, spear phishing is personalized.
Scammers conducting spear phishing attacks target specific people or organizations. They may only contact you or others in your organization, rather than hundreds of people.
Cybercriminals carrying out general phishing attacks hope that they'll catch some victims by contacting enough people at once. There are many different types of phishing attacks, like the Apple ID scams.
However, spear phishing personalizes the attack. Victims are more likely to believe an email directly addressed to them from an apparently reputable source.
Final words
We know that email scams can be confusing—and scary. What is spam? What is spear phishing, and how can you avoid it?
If a targeted phishing attack has tricked you, you’re not alone.
Speak to law enforcement or your company or bank, if necessary. Download comprehensive security software and familiarize yourself with the signs of a phishing attack to avoid it happening again.