In 2015 MacKeeper established a partnership with Chris Vickery — a skilled data breach hunter. Chris provided security auditing for MacKeeper, discovered potential threats, and advised the best solutions against future vulnerabilities. Besides that, Vickery reported on the newly emerged security and data breaches as well as provided useful personal recommendations on how companies and users can enhance their security.
2016 was marked by a growing number of data breaches. In this blog post, we’ve gathered the 35 most significant breaches.
This is the first post in a series of data breach reports.
Click on a data leak name to read the report:
- Microsoft Careers Site: vulnerability Attack
- Information on 1,700 children exposed by uKnowKids.com
- The Kinotopic app data leakage
- A series of subway hacks
- Verizon double data breach
- A massive breach of Mexican voter data
- Medical records of 150,000+ patients became available online
- Over 10 million messages from marijuana site leaked online
- A children’s educational site exposes thousands of user accounts and payment data
- Another Mexican leaked database found
- Pacific Gas and Electric database exposed
- Data on 600K+ of international students and 12K+ hosting homes exposed online
- Three mobile app’s user accounts leaked online
- US voter database leak
- World-Check global terrorism database exposed online
- Symantec and Norton vulnerabilities
- Oklahoma DPS security exposure
- Sage servers data exposure
- Luxury Hotel leaks thousands of customers’ credit cards online
- Data breach at Kingo Energy
- Data breach of the awards-screeners.com servers
- Trump’s website leak
- EMR4All data breach exposes 30K medical records
- 2.9 million Louisiana voters’ data available online
- Casual dating website exposes 1.5 million user accounts
- A law firms accidentally publishes online internal file repositories
- Multi-state voter data leak
- Habitat for Humanity breach
- Car dealership database leaked around million records
- Pet Retailer FuturePets exposed credit card data of 110K+ customers
- Joan Jett’s BlackHeart Records data leak online
- Ameriprise data breach
- Special ops healthcare worker breach
- Explosive data leakage of Allied-Horizontal files
- Incident response at Sheet Metal Workers Union
- HP Printer vulnerability risk
Essential reading and tools:
- Read these Mac security tips to learn how to secure your Mac with built-in tools or third-party apps
- Install an antivirus for Mac to scan your whole Mac for threats
- Get a Mac VPN to browse anonymously and have a secure connection when using public Wi-Fi
- Use Have I Been Pwnd to run a quick check to see if your emails have been in a data breach
- How to Get Rid of Malware on Mac guide will navigate you through essential steps towards a malware-free Mac
- How to Check for Malware on Mac will tell what kind of malware is out there and shows you how to detect and remove it
Microsoft Careers site: vulnerability attack
Punchkick Interactive — a mobile web development company Microsoft relied on to handle the database that powers m.careersatmicrosoft.com stayed exposed for a few weeks to the open internet and required no authentication at all to access.
As of February 5th, 2016, following Chris Vickery’s disclosure of the vulnerability to Punchkick and Microsoft, everything was secured. All indications were that the database, a MongoDB instance, was not write-protected. That meant that during the exposed timeframe, an attacker could have modified the database, and thus, the HTML code of job listing pages being served through m.careersatmicrosoft.com.
This situation is the classic definition of a potential watering hole attack. In that scenario, any number of browser exploits could be launched against unsuspecting job-seekers. It would also be a fantastic phishing opportunity, as people seeking jobs at Microsoft probably tend to have higher-value credentials.
Chris Vickery contacted Punchkick Interactive, namely Charles Portwood. The most recent message Chris received from Mr. Portwood contained the following:
The Mongo database is ours but is used for a separate service that is ultimately consumed by the m.careersatmicrosoft.com website. This issue that caused MongoDB to be exposed publicly has been fixed on our end.
Thanks for reporting this to us so that we could quickly correct it.
Charles R. Portwood II | Punchkick Interactive
There was only one hour between Chris’ first email to hello@punchkick.com and the database being secured. This was an example of excellent incident response.
A lesson to learn
The lesson to learn here is that if you’re a big-name player like Microsoft, it’s acceptable for third parties to handle mundane operations like job posting web pages. But be aware that a hole in the third-party’s security can quickly become a hole in your security.
Information on 1,700 children exposed by uKnowKids.com
In February 2016, a parental control platform uKnowKids.com exposed the sensitive information on 1, 700 children. The data exposure occurred because of a misconfigured database that could have been accessed by anyone without requiring login details.
The information collected by Shodan.io suggests that the database had been up for at least 48 days. Being bound by The Children’s Online Privacy Protection (COPPA) Rule, the company failed to “establish and maintain reasonable procedures to protect the confidentiality, security, and integrity of personal information collected from children.”
When informed about the data exposure and failure to comply with the COPPA Rule, the company’s CEO, Steve Woda, tried to brush the incident under the carpet. Furthermore, he attempted to convince Chris Vickery, who discovered the database vulnerability, that an outlet reporting on the breach could face liability under COPPA. Needless to say, the claim has no basis in reality.
A lesson to learn
Parents should be wary of services monitoring their children’s online behavior. These services collect unnerving amounts of data on your child and, when a breach occurs, all of that data can be exposed to untold numbers of people.
The Kinotopic app data leakage
In 2016, data belonging to more than 198, 000 users of the video editing app Kinotopic was in free access. The data resided in MongoDB database apparently belonging to Kinotopic, where it was discovered by Vickery.
Despite the fact that the app ceased to exist in 2013, its users’ email addresses, usernames, and hashed passwords, among other things, were publicly available years later. After an unsuccessful attempt to reach Kinotopic’s developers via email, Vickery contacted Apple. Alas, the company wasn’t able to offer any assistance.
A lesson to learn
The Kinotopic data leakage reminds us of the importance of using unique passwords. If you can’t avoid reusing the same passwords, at least try to change them regularly. By simply updating your password, you are reducing your exposure to a large number of cybersecurity risks.
A series of subway hacks
In 2016, a group of anonymous hackers gained access to 213 computers of the Seoul subway. The hackers, who allegedly acted on North Korea’s behalf, accessed only HR documentation and other information of minor importance.
The same year, the passengers of Moscow’s subway witnessed the results of another subway hack. After connecting to the subway Wi-Fi network, their digital devices showed a threatening message: “Paris was yesterday, Moscow is today.” The message was displayed against the backdrop of the ISIS flag.
Later that year, a similar but less sinister subway hack also occurred in Kyiv, Ukraine where digital screens displayed a character from BBC’s Sherlock.
A lesson to learn
Most countries’ subway cybersecurity is still sorely lacking. Given the ever-growing number of cybercriminals and the audacity of their attacks, it’s essential to tighten security measures for public transportation.
Verizon’s double data breach
In December 2015, Vickery discovered a Verizon database configured for public access without any sort of password or authentication at all. The database contained secret Verizon encryption and authentication keys (PSKs), access tokens and password hashes, as well as massive amounts of data and metadata for DVR, VOD, and Fios Hydra services.
Upon the discovery of the misconfigured database, Vickery immediately informed Verizon about the cybersecurity vulnerability. Even though the alarm was promptly sounded, the company took weeks to address the issue.
In March 2016, Verizon’s data was sold for $100, 000 on an underground cybercrime forum. The criminals also put up for sale information on the company’s cybersecurity vulnerabilities.
A lesson to learn
Most data breaches go unnoticed by the general public. When the incidents are reported by the media, companies tend to claim that the breaches have occurred in a test environment. This is precisely what happened with Verizon’s cybersecurity vulnerability discovered by Vickery.
Although there’s no way of telling whether the incident involved real customer data, be skeptical of companies’ claims about data breaches. In most cases, such claims are shaped by PR policies and expediency rather than a genuine interest in customers’ cybersecurity.
A massive breach of Mexican voter data
See the interview with Chris Vickery commenting on this breach.
On April 14th, 2016, Chris Vickery discovered a publicly accessible database, hosted on an Amazon cloud server, containing Mexican voter data. After reporting the situation to the US State Department, DHS, the Mexican Embassy in Washington, the Mexican Instituto Nacional Electoral (INE), and Amazon, the database was finally taken offline on April 22nd, 2016.
Back in 2001, the United States acquired a similar database through a brokerage firm known as ChoicePoint. Earlier, the firm purchased the Mexican voter database in exchange for $250,000 back in the early 2000s.
A lesson to learn
Under Mexican law, voter records are “strictly confidential”, carrying a penalty of up to 12 years in prison for anyone extracting such data for personal gain. If cybercriminals are daring enough to target governments, no private individual or company is safe. Therefore, it’s essential to implement good cybersecurity practices and always be in a heightened state of alert to protect one’s data and privacy.
Related article: Another Mexican leaked database found
Medical records of 150,000+ patients became available online
In 2016, MacKeeper’s experts discovered the open and unsecured databases of medical records belonging to management companies Carebox and HealthELT. The databases contained the private medical data of more than 150,000 patients and were not encrypted or password protected.
The companies had detected and eliminated the cybersecurity vulnerability before they were contacted by MacKeeper experts. However, it’s worth remembering that the HIPAA Privacy Rule prohibits the disclosure of private medical records even for brief periods.
When contacted, a representative of HealtELT assured the MacKeeper experts that the publicly available database contained test data. The experts questioned the veracity of that statement because the databases clearly contained Social Security numbers and other sensitive information.
The other company did not respond to the cybersecurity warning but restricted access to its data.
A lesson to learn
Medical professionals all agree that Electronic Medical Records (EMRs) are the future of medical records because they can be easily tracked and accessed at a moment’s notice by any medical provider. However, if not properly secured, EMRs are vulnerable to data leaks and online exposure. This is yet another lesson of how important it is to secure and encrypt private data collected by digital service providers.
Over 10 million messages from marijuana site leaked online
In May 2016, over 10 million messages from TheTreesNetwork.com, a marijuana-enthusiast site, leaked online.
Upon discovery of the leak, Chris Vickery joined the chat and posted the following message: “What would you do if I had proof that this site is leaking user details?”. When asked for proof, Vickery posted an Imgur.com link to an image showing an overview of the database (but not the specific IP address or any user details).
Once notified, the website’s administration sealed the data leakage in mere minutes. This doesn’t change the fact that over 10 million chat messages coming from over 44,000 users got online.
If anyone had admitted to criminal activity in one of those chat messages, then that person might be alarmed to learn that TheTreesNetwork.com also kept logs of its users’ IP addresses. So, even when chatting under a pseudonym, all it would take is a subpoena to one’s internet service provider to find out who they are (assuming that a proxy or VPN is not being used).
A lesson to learn
The lesson to learn here is to always use VPN and be careful about what you say online. You never know when it might come back to haunt you.
A children’s educational site exposes thousands of user accounts and payment data
In 2016, the MacKeeper team discovered a misconfigured database belonging to ABCya, a company that claimed to be the leader in free educational kids computer games and activities for elementary students. The website was frequented by approximately 4 million visitors each month. The visitors would be surprised to discover that the publicly available company’s database contained the following information:
- credentials and info of 11k+ archived customers (incl. IPs, emails, names, temporary access code, hashed and salted passwords)
- credentials and info on 21k+ active customers (incl. credit cards details such as hashed ID, fingerprints, expiration year and month, last 4 digits and card name in plain text).
- more than 3k+ Stripe tokens and info
- credentials of 4 “super admin” users for ABCya with encrypted/salted passwords and details.
ABCya didn’t respond when notified about the issue. However, MacKeeper’s experts noticed that the access to the database was restricted shortly after.
A lesson to learn
With each and every breach, it becomes clear that companies that store customer data must take every precaution to protect that data. Companies that store and collect credit card data should be even more cautious about cybersecurity. Knowing the heightened risk of breaches, credit card providers discourage businesses from storing credit card data.
Another Mexican leaked database found
On May 18th, 2016, Chris Vickery discovered another publicly exposed Mexican database with voter records. The researcher reported it to the Mexican electoral authority (INE) that same day.
Later, INE held a press conference where it reported that the database had been taken offline. INE’s initial investigations indicated that the data stemmed from the region of Sinaloa.
In the INE’s report, no political party was named responsible for the leak. However, Vickery discovered that the database was titled “DBPRI” and all signs pointed to the PRI party as being connected to the leak.
A lesson to learn
When the stakes are high, organized cybercrime groups stop at nothing to pursue their objectives. The second Mexican leak of voter records serves as a reminder to tighten cybersecurity and protect valuable data worldwide.
Pacific Gas and Electric database exposed
In May 2016, Chris Vickery discovered a data breach involving Pacific Gas and Electric (PG&E), a very large electric utility company in California. The publicly exposed database appeared to be PG&E’s asset management system.
Among other things, the database contained information from over 47,000 PG&E computers, virtual machines, servers, and other devices. Specifically, IP addresses, operating systems, hostnames, locations, MAC addresses, and more. This would be a treasure trove for any hostile nation-state hacking group. That’s not to mention the 120 hashed employee passwords, or the plaintext NTLM, SOAP, and mail passwords.
When the news of the exposed database reached the company, its IT department claimed that the database was “fake”. However, fictitious databases do not generally have areas specifically marked development, production, and enterprise. Fictitious databases do not generally have over 688,000 unique log record entries. That database did.
Shortly after the incident, PG&E took down the exposed databased and issued the following statement:
With this incident, it is important to know that none of PG&E’s systems were directly breached in any way and no customer or employee data was involved.
A PG&E vendor was hosting an online demonstration using PG&E asset management data to show the capabilities of a platform that they were developing for us. This data contained information on PG&E’s technology assets, such as computers and servers.
Our initial review indicated that the data was non-sensitive, mocked-up data. We based this feedback on an initial response from the vendor stating that the information in the database was a demo or “fake” data. Following further review, we learned that the data was not fake and removed access.
We continue working with all of our vendors to have appropriate procedures in place at all times to protect PG&E data in those instances when they have it.
A lesson to learn
It’s theoretically possible to create software that could generate massive amounts of fake data, but companies don’t usually do that.
Even if a database is for development purposes only, companies tend to fill it with real production data. They do that because production data is easily available and free. Companies generally do not pay for the creation of great swaths of false data when plenty of real data is already available. Any claims to the contrary should be questioned with extreme skepticism.
Data on 600K+ of international students and 12K+ hosting homes exposed online
In 2016, a database belonging to the Cambridge Institute of International Education (CIIE), a Boston-based educational consulting firm, became publicly available online.
The database had a folder titled "NewStudentsApplicationReportForFinanceV1" that contained 600K+ records for international students and included personal information such as names, emails, passwords, phones, account details, relatives info, passport details (all in plain text). Moreover, there were even correspondence records between the CIIE team members, housing reports and working links to the pdf's and payment confirmations.
In addition, the database held an additional collection of records on 12,000+ hosting houses. Among the records, there was the information on a household, family member details (such as medical conditions, if any, religious beliefs, even frequency of attending religious activities), occupation details, including emails and phones, birthdates, and other extremely sensitive data on the personal privacy of the host families.
The database contained a treasure trove of sensitive data could have been used for a wide range of illicit activities and in addition to the possible illegal or criminal uses of this data, it is extremely embarrassing to see documentation of housing reports and detailed descriptions about students’ conflicts, medical conditions, personal problems, living conditions, and much more.
Other notable leaks and breaches of data belonging to educational institutions that occurred between 2014 and 2016 are listed below:
- The University of Maryland exposed SSNs and more for 300,000 students and employees
- North Dakota University lost data on 300,000 students to hackers
- Butler University lost 200,000 to hackers, and Indiana University exposed information on 146,000 students.
- In 2015 vendors seeking to do business with the Chicago school district were given the personal data of 4,000 students
- 2016 The University of Greenwich's accidentally published the personal data of students on their website
A lesson to learn
Since 2014, the number of students who have had their data compromised online has grown exponentially. With over half of a million accounts exposed, the CIIE breach is yet another example of the importance of data protection in the educational field.
Three mobile app's user accounts leaked online
In December 2015, Chris Vickery stumbled upon three separate, publicly accessible databases containing hundreds of thousands of user records. Vickery had all reasons to believe that the databases were operated by three apps: Bunt, Huddle, and Kick. The apps belonged to the Topps — American baseball card company.
The databases were secured before Vickery had a chance to reach the company. However, in 2016, a similarly exposed and publicly accessible database appeared online (with all three apps’ data lumped together on one server).
The researcher sent emails to three different Topps support addresses. Alas, the only response he got was a single automated message informing him that his request had been received.
A lesson to learn
A takeaway here is that, even if it doesn’t necessarily apply to Topps, not all companies acknowledge data leaks and breaches. According to a recent report, almost 60% of organizations don’t disclose data security incidents to their customer base. It means the chances are high you won’t be alerted should a breach occur.
US voter database leak
In June 2016, Chris Vickery came across a database containing information on 154 million US voters. The database was configured for public access with no username, password, or other authentication required.
The leaky database was located on a server rented from Google’s Cloud services. After a brief investigation, Vickery determined that the data originated from a data brokerage company L2.
When informed about the leak, L2 confirmed that the data was sold to its client who had been hacked. Then, the database was taken offline within three hours of the notification, which was an incredibly quick remediation of the issue.
During a close examination of the database, Vickery discovered that a Serbian IP had interacted with the database. Even if that was just a proxy server, it is still very troubling that the US voter information was globally available.
A lesson to learn
The US voter database leak underscores severe vulnerabilities of the country’s voting system. The incident discovered by Vickery could be followed by additional leaks, which could be exploited by hostile nations. Therefore, the US election system should be prepared for data hacks that are likely to come.
World-Check global terrorism database exposed online
In 2014, Chris Vickery discovered a leaked database called World-Check with information on over 2.2 million heightened-risk individuals.
World-Check was used by over 300 government and intelligence agencies, 49 of the 50 biggest banks, and 9 of the top 10 global law firms. The 2016 version of the database contained, among other categories, a list of 93,000 individuals suspected of having ties to terrorism. It also had information on individuals suspected of being related to money laundering, organized crime, bribery, corruption, and other unsavory activities.
Three years before the incident, the company that created the database was purchased by Thomson Reuters for $530 million. After the leak, Reuters claimed that the database had been exposed by a third-party and confirmed the elimination of the cybersecurity vulnerability.
A lesson to learn
If the database became publicly available, the individuals on the list could have taken steps to conceal their identities. There is no saying how much harm could be caused by the leaked information in the wrong hands. Fortunately, the leak was discovered by MacKeeper’s partner Chris Vickery who has not released the database to the world.
Symantec and Norton vulnerabilities
In June 2016, Tavis Ormandy discovered Symantec and Norton vulnerabilities that could be exploited by cybercriminals to access people’s data.
According to Tavis, who discovered the vulnerabilities, the flows don’t even need any user interaction, they affect the default configuration, and the software runs at the highest privilege levels possible. “In certain cases on Windows, vulnerable code is even loaded into the kernel, resulting in remote kernel memory corruption.”
The list of vulnerable solutions in the Symantec enterprise line included 17 items. These items had been posted as a security advisory on the Symantec website a bit earlier than Tavis’ post was published.
Anyone could exploit the vulnerabilities in Symantec’s product by just emailing a file link to a victim. Symantec’s antivirus software couldn’t detect the malware until the executable was decompressed. Given that Symantec decompressed files in the operating system’s kernel, malware hidden in an executable file had an opportunity to gain complete access to the computer running the operating system.
The most astonishing fact is that the wormable vulnerability made it possible to compromise one’s data even if a user didn’t click the malicious link.
A lesson to learn
To avoid multiple cybersecurity risks, use a reliable antivirus from a trusted software vendor. Also, update the antivirus regularly to ensure that vulnerabilities discovered and patched by software developers are not exploited by cybercriminals.
Oklahoma DPS security exposure
In July 2016, Chris Vickery discovered an exposed database containing information belonging to the Oklahoma Department of Public Safety (DPS). As happened with most of the data leaks previously discovered by Vickery, the database could be accessed without login details and contained an alarming amount of information.
Among the exposed data, there were photographs of security mechanisms (e.g. locks, RFID access panels, and controller boards) from within protected Oklahoma DPS buildings. Database entries also contained motor vehicle records such as manufacturer and model, location, warranty coverage, and even whether or not the unit was still functional.
Upon the discovery, the cybersecurity expert called Automation Integrated’s service hotline to report the database vulnerability. Several hours later, Vickery received a call from a VP from Automation Integrated who thanked him for alerting them to the issue. The VP took personal responsibility for the oversight and couldn’t have been nicer to the cybersecurity expert.
A lesson to learn
The organization’s reaction to Vickery's report was an example of excellent incident response.
The VP didn’t call Vickery a hacker, he didn’t claim that it was a fake database filled with test data, and he didn’t try to deflect responsibility onto another company. What he did do was fix the issue promptly, verify with the original reporter that the issue was fixed, and he appreciated the fact that someone would go out of their way to make sure an issue like this was taken care of. More organizations should adopt a similarly cooperative approach to tackling cybersecurity challenges.
Sage servers data exposure
In 2016, Chris Vickery found over 20 unprotected databases under the control of Sage customers, powering “on-premises” versions of Sage’s X3 server software suite. Some of these servers contained massive amounts of company records in the form of PDFs, DOCs, and XLS spreadsheets.
When contacted, the Sage representatives were very clear that while the company allegedly was not at fault for these breaches, it was extremely concerned with any situation involving their software being implemented insecurely by clients. Then, Sage immediately began a process of reviewing the IP addresses provided by Vickery and notifying affected customer companies that have been insecurely utilizing Sage’s X3 server software.
Upon a close examination of the issue, Vickery found that identical password hashes were present across many of the installations, which indicated the use of default passwords. Later, Sage confirmed that one of the exposed X3 servers was set up by the company itself as a demonstration unit. That begs the question of why Sage would deploy a server, even if it was a demo, that contradicted its own best practices and instructions.
A lesson to learn
Sage’s on-premise X3 software is not designed to be exposed to the public internet. If you are a customer of a similar company, make sure that your software installations are behind a firewall and implement access restrictions. Most companies do, but at least 20 Sage’s customers involved in the database exposure did not. The possible repercussions for those clients are frightening.
Luxury hotel leaks thousands of customers’ credit cards online
On August 12, 2016, MacKeeper’s experts discovered an open database belonging to the Silverland Hotel in Ho Chi Minh City, Viet Nam, with information on over six thousands of unencrypted credit cards.
The cardholder accounts included the payment information of Australian, US, and UK citizens as well as a range of international guests who have stayed at the hotel. Along with the payment information, the database also contained login details, IP addresses, and special requests of the guests.
The open database was publically available and required no password to access. What’s more, it shared the same IP address as the hotel’s website.
Immediately upon discovery of the open database, MacKeeper’s researchers notified the hotel administration about the issue. With some delay, the hotel eliminated the database leak and notified affected customers. Additionally, Silverland Hotels & Spas hired the US attorney Ira J. Bornstein to assist them in handling this matter.
A lesson to learn
At home or abroad, at work or on vacation, cybersecurity challenges know no bounds and can reach you anywhere. Imagine having saved and planned for a perfect holiday trip to Vietnam and a stay in a luxury hotel only to discover that your card details are available online. To spare their customers such scenarios, companies are well-advised to tighten their cybersecurity.
Data breach at Kingo Energy
In August 2016, Chris Vickery came across a completely unprotected CouchDB installation sitting out on the open internet. The database contained high-resolution photographic images for both the front and back of Kingo customers’ Guatemalan national ID cards.
Apparently, along with photos of the signed client contract, Kingo required agents to take pictures of a new customer’s national identification card. Unfortunately, Kingo stored this highly sensitive data in an open, unprotected database that anyone in the entire world could access with a regular web browser.
When notified about the breach, the company took swift action and password-protected the database. Then, the Kingo team expressed gratitude to Vickery and assured him that the company was going to direct the necessary resources toward ensuring the privacy of their customers’ personal data.
A lesson to learn
Although this story doesn’t offer a particularly insightful cybersecurity lesson, the company’s polite response is noteworthy. It didn’t try to call Vickery a hacker or blame the breach on a third-party contractor. Nor did the company try to claim that it was just a fictitious database. Those are the usual knee-jerk reaction statements Vickery habitually got from companies with exposed databases.
Let’s just hope the researcher was one of only a few people to discover that database while it was unprotected and exposed.
Data breach of the awards-screeners.com servers
In 2016, awards-screeners.com and the company responsible for running it, Vision Media Management, had a data breach problem discovered by Chris Vickery.
The biggest immediately recognizable concern within this database was the existence of around 160 usernames and hashed passwords for people whose email addresses end with domains such as @paramount.com, @disney.com, @warnerbros.com, @fox.com, and @spe.sony.com. The user table had a total of about 1,200 entries, but there was a reason to believe that some amount of load-balancing test data was also included. The 160 “actual logins” number is what Vision Media claimed to be accurate.
The passwords that accompanied these accounts were strongly hashed (bcrypt algorithm) and salted. While this means that a chance to quickly crack any of them was low, given enough time an attacker could still possibly compromise a few accounts. Those accounts were high-value targets, so the motivation was definitely there for someone to spend the necessary hash cracking time.
Upon reaching the company and laying out the details of the breach, Vickery was connected with the company’s lead internal counsel. Later, the researcher communicated with Vision’s CTO, Doug Woodard, to further clarify the issue and expedite its resolution.
As often happens in database exposure cases, Vickery was assured that he discovered test data. The researcher questioned the claim, which allowed him to discover more freely-available data belonging to the company.
A lesson to learn
Although the lesson you are about to read has been proffered before, it bears repeating nevertheless. Companies’ claims after a data breach should be taken with a great deal of salt. Especially when it comes to assurances that only test data has been leaked.
Trump’s website leak
In September 2016, Chris Vickery discovered that Trump’s asset repository was publicly available due to bungled settings of the Amazon S3 server.
After discovering this asset server’s existence, and his URL fuzzer being met with code 301 redirects instead of code 403 denials, the investigator started digging. Because directory listing was disabled, there was no easy way to enumerate folder names within the asset bucket. Vickery was running through a small dictionary of common folder names when he got a hit on a folder named “resumes.”
After a brief investigation, Vickery found 24 resumes that contained scores of personal details, work/education history, and professional references, among others. Then, Vickery requested assistance from a journalist friend who was able to contact the right people and get word of the leak to Trump’s staff. Shortly after, the breach was eliminated.
A lesson to learn
Ultimately this was an entirely avoidable mistake on the part of Trump’s tech staff. Given that Trump’s campaign failed to acknowledge the data leak, there’s no way to assess the extent of the damage caused by it.
People sending their resumes to companies should always keep in mind that they could eventually become public due to mishandled data protection settings.
EMR4All data breach exposes 30K medical records
In September 2016, Chris Vickery found an Amazon S3 repository (known as a bucket) containing approximately 30,000 medical records. The records were displayed to the investigator without so much as a username or password being requested.
When trying to reach the company, Vickery encountered a hindrance — EMR4all website was just a login portal for their clients with no contact phone number or email address to be seen. To inform the company about the breach, MacKeeper’s researcher requested assistance from a friend who was able to get Amazon’s attention, who, in turn, notified EMR4All of the security issue.
EMR4all quickly responded with a promise to rectify the issue and inform authorities. In subsequent correspondence, the company revealed that no more than 30,000 total patients could have been affected by this breach. Vickery was unable to verify that number due to the heterogeneous nature of the .txt and .edi transmittal files included in the data dump.
Also worth mentioning is the fact that the company’s representatives didn’t ask the researcher if he had downloaded the data. That was glaring data privacy and security oversight on their part.
A lesson to learn
If there’s one piece of advice that could be imparted to all holders of healthcare data, it’s this: Make sure you prominently display some method of contact on your homepage. When someone notices you are leaking data, you want that person to be able to contact you directly. Things get exponentially more complicated with each additional person that has to be contacted before the breach is secured.
2.9 Million Louisiana voters’ data available online
In 2016, MacKeeper’s experts discovered an open and publicly available database that contained detailed information on every voter in the state of Louisiana. The voter database named 'lavoter' was hosted on Google Cloud IP and contained 2,919,651 records.
The information included the following categories (among others): Names, Full Address (including mail address), Sex, Race, Political Party Code, Voter Status, Registration Date, Registration Number, Personal Phone No., Last Voted data, and Voting History data. The same categories can be found on Louisiana’s Secretary of State website.
Another database hosted on the same IP was named ‘ladps’ and contained 6,978,508 records. Most likely, it was connected to ‘Department of Public Safety”, since the following categories were presented in the database: Full Name, Residence Address, Race, Sex, DOB, Height, Weight, Residence Parish code, Driving License Number, SSN code (but not the SSN itself), and issue number.
MacKeeper’s experts were shocked to discover that all voter data is for sale to basically anyone willing to pay for it. One didn’t even have to prove that the data would be used for political purposes, research, or any related election purpose. Voter data was priced at $0.01 per name on the list.
A lesson to learn
It is unclear if the database discovered by MacKeeper’s experts belonged to the State of Louisiana, a political organization, or to some other entity. What’s clear is that voter data and election should be considered "critical infrastructure" and not sold off to the highest bidder or wholesale prices. Citizens should at a minimum have the right to “Opt Out” of having their data sold if they live in a state that sells voter information.
Casual dating website exposes 1.5 million user accounts
A database discovered by MacKeeper’s researchers in 2016 contained over 1.5 user accounts.
The database appeared to be part of C&Z Tech Limited, a New Zealand registered company that operated a number of dating websites and a mobile application "Hook-Up Dating". These dating sites targeted men and women "who are either attached/married seeking something fun on the side or single seeking something casual".
The exposed database contained login details in plain text as well as personal information such as height, weight, DOB, gender, gay body type, and race among others. It was left unattended for almost a day before it was secured.
Shortly after MacKeeper’s experts informed the company about the breach, it got a response from the company’s representatives. They alleged that the exposed information was “just dummy data with randomly generated emails and passwords and not our live database.”
A lesson to learn
It seems that the sensitive user data was exposed for only one day. The question then arises: How long should sensitive data be exposed and unsecured before it is called a data leak? In line with what some US courts have ruled, a breach occurs the very moment that data is put in a publicly accessible place.
If the leaked data got in the wrong hands, the users of the dating service could have been blackmailed and extorted. Given the poor cybersecurity practices of such services, you might want to reconsider their use.
A law firm accidentally publishes online internal file repositories
In 2016, Chris Vickery stumbled across more than 500 gigabytes of client files belonging to a law firm — Ferguson, Praet & Sherman. Client files are the crown jewels of a law firm and supposed to be kept under lock and key, which makes these internet-accessible discoveries even more surprising.
When reviewing the files to determine their importance, Vickery discovered sensitive information on a client of the firm. The case involved Daniel Oppenheimer who hanged himself while in a holding cell at the La Habra city jail. Oppenheimer’s daughter was suing for wrongful death at the moment of the file discovery.
Although the District Attorney’s investigation concluded that there was no wrongdoing on the part of jail staff, Vickery found evidence to the contrary. The investigator requested the Orange County District Attorney to take another look at the discovered evidence.
A lesson to learn
Can you imagine what would happen if someone other than MacKeeper's researcher found the law firm’s legal documents? There’s no saying how such discovery would have influenced ongoing legal cases. One thing is clear, though: No client of the law firm would have benefited from having their files hosted on public IP addresses with no username or password protection.
Multi-state voter lata leak
In 2016, MacKeeper’s digital security experts discovered a publicly available database of voter records totaling more than 350K. The records belonged to four states: Montana, New Jersey, California, and Virginia.
The personal information included names, home address, phone number, gender, date of birth, state voter ID, race, marital status, unique voter ID, date of voter registration, phone number, political affiliation and participation in primary elections, among others.
Some states restrict how the data may be used and set restrictions for commercial or charity. Most states require that voter data be used only for political and election-related activities, but what if the records were leaked online?
MacKeeper’s researchers were not able to identify the database’s owner to stop the leak.
A lesson to learn
This is the second leaked voter records database discovered by MacKeeper researchers.
The challenge going forward is to secure voter records that are likely already compromised or in some cases up for sale by the state election commissions.
Unfortunately, there’s no easy way to address the issue. Once leaked, the data cannot become private again. Most likely, voter data will just become a public record similar to court records.
Habitat for Humanity breach
In 2016, Chris Vickery found over 400 gigabytes of virtual hard drive data belonging to the Michigan branch of an international charity that builds and provides low-income housing — Habitat for Humanity.
When examining 400 gigabytes of data, the researcher found a directory with over 700 folders containing PDF background and credit check reports. You can imagine how sensitive these reports were. They contained everything a malicious actor would need for identity theft. Vickery also quickly found a SQL database backup file with a bevy of information, including over 4,600 peoples’ social security numbers, names, addresses, and phone numbers, among others.
The MacKeeper’s researcher contacted the organization’s Internet Service Provider (ISP) that contacted Providence who was the main hosting provider of the Habitat’s Michigan branch. Although the data exposure was eliminated, there was no indication that ISP or Providence notified the organization about it. More details on the incident can be found in Dell Cameron’s investigation.
A lesson to learn
The exposed data’s discovery came on the heels of the hack of the charity’s Colorado hack that crippled its operations. Two breaches within a month indicate poor cybersecurity practices adopted by the organization.
This all goes to show that the current state of data breach response leaves much to be desired. Just a few companies own up to making mistakes, very few accurately communicate information surrounding the event, and even fewer follow through with a well-planned incident response plan. Most companies do everything possible to avoid notifying the affected individuals.
Car dealership database leaked around million records
In 2016, MacKeeper’s experts came across nearly a million records of automotive dealership employees and customers inadvertently leaked online. The database belonged to dealerbuilt.com, a dealer management and payroll system.
There were several folders containing the private and personal information of over a thousand customers and employees. Some of the files had social security numbers and even spouse social security numbers.
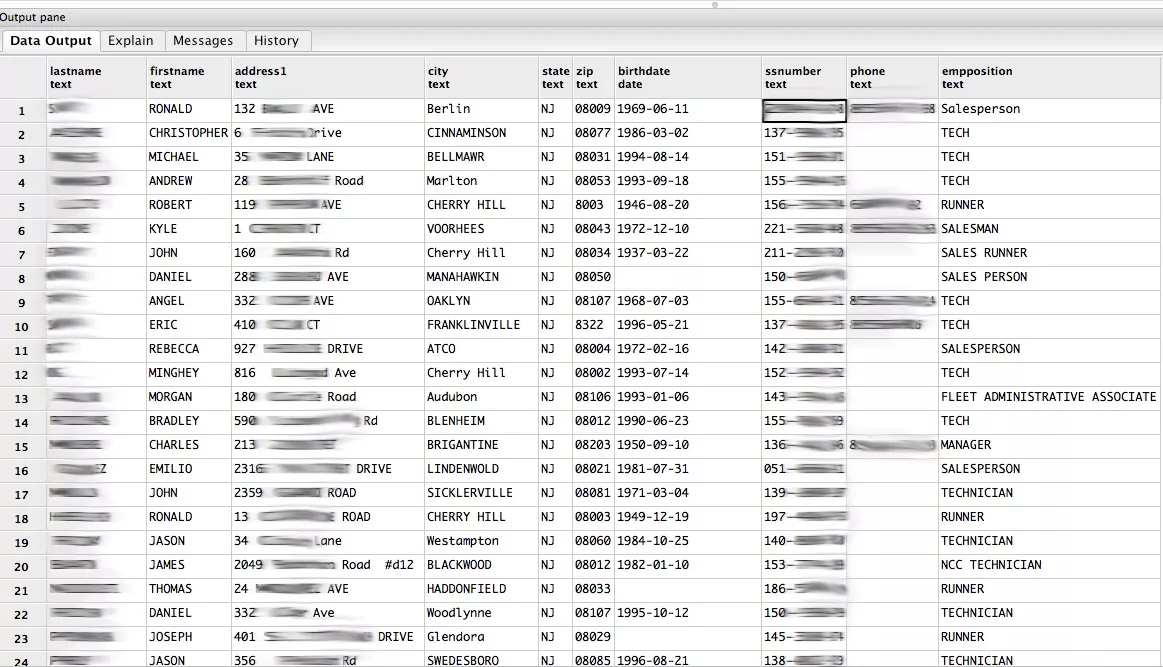
When employment data is leaked that contains social security numbers it makes it a higher risk for criminals to engage in identity theft, filing false tax returns, or other forms of fraud. This same risk applies to thousands of customers who have purchased vehicles or even applied for financing the purchase with dealerships that had used the services of dealerbuilt.com.
A lesson to learn
This massive leak is just another reminder of the importance of protecting your privacy online. It also offers a painful lesson of what happens when private and sensitive data is stored without encryption or modern data security practices. The dealerbuilt.com database is now secured and it is unclear how many other people may have accessed the data or what steps DealerBuilt will take to notify the millions of affected customers and salespeople.
Pet Retailer FuturePets exposed credit card data of 110K+ customers
In 2016, MacKeeper’s researchers found that Futurepets.com, a US online pet store, had leaked credit card details and private information of more than 110,000 customers.
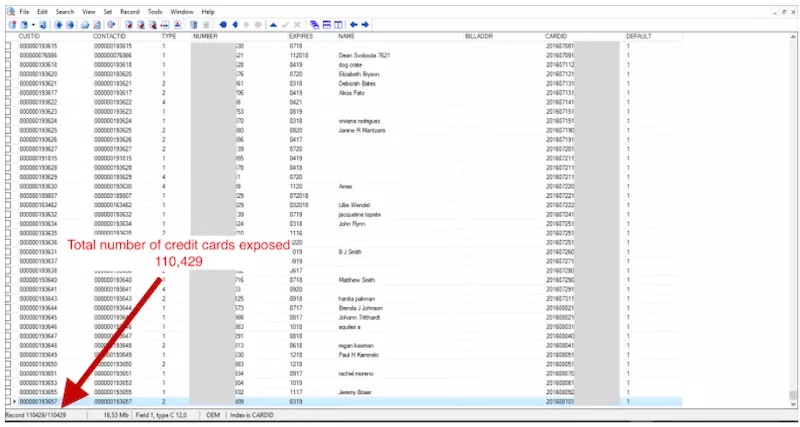
The company incidentally set the Rsync protocol to stream data without any password protection. Thus, anyone with an Internet connection and an Rsync client could have downloaded the data that in addition to credit card details contained checkout information, shipping addresses, emails, names, and phones. The company started collecting that data in 2002.
When the researchers came across the database they immediately notified the owners of Futurepets.com about the data exposure.
A lesson to learn
According to Payment Card Industry Data Security Standard (PCI DSS), retailers do face serious potential consequences for non-compliance with standard security protocols in their daily operations. In addition, sensitive authentication data such as CVC, CVV, and CVV2 must not be stored after authorization, even if encrypted.
The prohibition to store CVC, CVV, and CVV2 makes sense in light of the data protection findings by MacKeeper’s researchers. They discovered that it’s possible to make an online purchase without knowing a CVV code.
Joan Jett’s BlackHeart Records data leak online
In December 2016, MacKeeper’s researchers found a misconfigured backup server containing hundreds of gigabytes of data belonging to a rock star’s Joan Jett record label, BlackHeart Records. The exposed data was a massive treasure trove for fans and cybercriminals alike. There were unreleased tracks, never-before-seen pictures, even rejection letters from 1980 when the artist tried to get a record deal.
Generally, when dealing with software, the word "vulnerable" is used to describe a system that can be, or is, exploited in some fashion. In that case, no exploit or deception was utilized in any way.
MacKeeper’s experts discovered the backup server when looking for vulnerable rsync ports. It was open to the public with no username, password, or other authentication methods in place. Anyone in the entire world could have downloaded the data.
Soon after the discovery, the data was secured. However, it is unknown for how long the database was publically available.
A lesson to learn
With the social security numbers, banking information, scans of passports, and IDs it is easy to see that cybercriminals could have exploited that data for identity theft, fraud, or extortion. Therefore, system administrators relying on rscync to copy and backup data should always protect database ports with passwords to prevent unauthorized access.
Ameriprise data breach
In 2016, Chris Vickery found an unsecured Network Attached Storage (NAS) device containing data belonging to a financial services company, Ameriprise. After an initial investigation, Vickery determined that the NAS was not on the internal Ameriprise network, but rather it was physically located inside an Ameriprise employee’s home.
The NAS was synchronized with another identical NAS over the open Internet. After learning about the incident, Ameriprise pulled both devices and examined them in an internal IT lab.
A lesson to learn
An Ameriprise employee indicated to Vickery that the examination of the NAS devices was, in part, to make sure there wasn’t a bigger problem to worry about. It indicates that there was at least some concern that Ameriprise offices had more similarly misconfigured devices.
In the age of daily data breaches and ransomware attacks, it’s essential to ensure that NAS devices are not connected to the Internet. If a company needs a storage solution that can be accessed from anywhere, it’s worth considering the use of a cloud storage service.
Special ops healthcare worker breach
In 2016, Chris Vickery found a collection of publicly accessible backups belonging to Potomac Healthcare Solutions. The company provided healthcare workers to the US Government through Snowden’s former employer, Booz Allen Hamilton.
Immediately after the discovery of unprotected backups, Vickery informed the company’s CEO about the data exposure. Much to the researcher’s surprise, the unprotected file repository was still up and available an hour later.
Understanding that national security was at stake, Vickery contacted several government agencies and arranged the database shutdown. Potomac’s files went offline about 30 minutes later.
A lesson to learn
It’s not hard to imagine a Hollywood plotline in which a situation like that results in someone being kidnapped or blackmailed for information. Let’s hope that MacKeeper’s researcher was the only outsider to come across the exposed data.
Explosive data leakage of Allied-Horizontal files
When conducting cybersecurity research in 2016, Chris Vickery found exposed data of a wireline company, Allied-Horizontal. Given that the company also handled explosive materials, it was tightly regulated by the Bureau of Alcohol, Tobacco, and Firearms (ATF).
The leaked data contained high-quality scans of explosives handling licenses, which raised the possibility of impersonating authorized explosives handling personnel. After downloading over 7 gigs of internal Allied-Horizontal files, which represented only a small fraction of the overall exposure, Vickery became convinced the data was legitimate and the leak should be plugged immediately.

The researcher contacted the organization’s CEO and IT department and provided them with the vulnerable IP address. The leaky server was secured shortly afterward.
A lesson to learn
The moral of this story is that companies should be regularly hitting their important IP addresses with tools like nmap and masscan (or even looking themselves up on Shodan.io, Zoomeye.org or Censys. io.). Keeping an eye on all potential exposure points is a tough task. It’s unfortunate that most companies either can’t afford dedicated network security staffers, or the C-level executives don’t understand the immense impact of a data breach scenario.
Incident response at Sheet Metal Workers Union
In October 2016, Chris Vickery found a database backup belonging to the Northern California branch of Sheet Metal Workers Union. The database backup contained over 24,900 members’ names, social security numbers, phone numbers, addresses, ethnicities, and beneficiaries, among others. It was left completely exposed to the public Internet through a passwordless rsync server.
In addition to that database backup file, there were PDF union member files named in the following fashion: “Last Name, First Name, Social Security Number.pdf”. Can you believe someone thought that would be a good idea?
On October 10th, Vickery reached the Northern California branch’s main office and left a voicemail explaining the security blunder. The database and other files were secured sometime shortly thereafter (within a day or two).
A lesson to learn
Although this has been mentioned above, the lesson is important enough to repeat it twice. Never run unprotected remote synchronization (rsync) service for backup. Make sure to restrict access to rsync ports to reduce the risk of a data breach.
HP printer vulnerability risk
In 2016, MacKeeper’s researcher, Chris Vickery, looked at the way misconfigured printers could leak data. It turns out that HP printers had a publically accessible port 9100.
At the time, there were a few free, open-source pieces of software that could be used to upload and interact with HP printer hard drives over port 9100. After uploading to a printer, a file could be accessed by visiting http:///hp/device/ with any web browser.
The vulnerability opened up a world of possibilities for hackers who could host malicious web pages and scripts on people’s printers and link them to potential victims. Cybercriminals could have even explored the vulnerability to store highly illegal materials this way.
Given that printers are usually powered up and online twenty-four hours a day, the likelihood of their use as illegal file repositories was not negligible. What’s more, the organizations leaving their printers exposed to the Internet probably don't have the greatest, if any, logging systems in place. For the malicious actor, the chances of being caught are extremely low.
A lesson to learn
At this point, you may be questioning Vickery’s decision to draw attention to the security vulnerability. Disclosing vulnerabilities will always be a double-edged blade. Sure, some people could have taken advantage of the information, but the researcher wanted to ensure that anyone seeking tips on how to protect themselves should also be made aware.
So, if you’re concerned about security, put your printers behind a firewall and, if it’s a Hewlett-Packard, make sure port 9100 isn’t open.
* * *
To minimize the risk of a data breach, protect your Mac with a comprehensive security solution, MacKeeper. The solution has been designed from the ground up by seasoned cybersecurity professionals dedicated to shielding your data and privacy.
Read more guides: