The recent cyber attacks of 2022 include apps and websites you probably use daily. These are breaches that you (or someone you know) could have fallen victim to—some of which might shock you.
Let’s look into each event in more depth.
1. WhatsApp
Number of victims affected: 487 million
Type of information stolen: Mobile numbers
Summary of what happened: On November 16, 2022, a bad actor attempted to sell databases containing the mobile numbers of WhatsApp users on a popular hacking forum. For perspective, WhatsApp has more than 2 billion active users. The majority of the numbers belonged to users in the US, France, Egypt, Italy, Saudi Arabia, and Turkey. The prices for each database differed, depending on the country the users were from. Cybernews investigated a small sample sent by the bad actor, which confirmed that the numbers included in the data set were legitimate WhatsApp numbers.
Lesson learned: Using a reliable VPN could prevent you from falling victim to a breach like this.
2. Twitter
Number of victims affected: 5.4 million
Type of information stolen: Phone numbers and email addresses
Summary of what happened: The story started in January 2022, when Twitter was accused of API vulnerability and paid the blaming party to fix the issue. But later, in July, a bad actor attempted to sell the personal information of millions of Twitter users for $30,000 on Breach Forums. Twitter confirmed the July 2022 breach in August 2022. The bad actor later published the numbers and email addresses from that breach on the dark web in November 2022.
Lesson learned: Bad actors can find their way around security systems. Using two-factor authentication (2FA) can help protect you from becoming a victim of similar breaches.
3. Neopets
Number of victims affected: 69 million
Type of information stolen: Account information—including passwords, IP addresses, email address, countries, genders, and birth dates
Summary of what happened: In July 2022, the Jellyneo website posted that it had received an anonymous tip about a breach affecting Neopets users. Both the database and source code were breached. The source code was being sold for 4 Bitcoin, but buyers could buy live access to Neopets’ database at an extra cost. Neopets encouraged users to change their passwords on Neopets and other websites where they used the same passwords. There was no confirmation about the vulnerability having been patched.
Lesson learned: Use a password manager to manage all your online passwords. Create strong passwords and avoid using the same passwords for multiple accounts.
4. Uber
Number of victims affected: 77,000 workers
Type of information stolen: Full names, work email addresses, work location information, serial numbers, device makes and models, and technical specifications
Summary of what happened: Uber suffered a data leak due to a data breach affecting its third-party vendor, Teqtivity. On December 10, 2022, a Breached Forum user posted a database of more than 20 million internal records belonging to Uber. Of those records, 77,000 included the personally identifiable (PII) information of Uber employees. The user wasn’t selling it, but was sharing it with other users on the forum instead. A second data dump posted on the same day included source code, web app data, and more information related to the leak.
Lesson learned: Data breaches aren’t always the result of your negligence or that of the companies you’re signed up to, but of third parties.
5. AT&T Data
Number of victims affected: 23 million
Type of information stolen: SSN, names, cell phone numbers, landline phone numbers, business phone numbers, email addresses, dates of birth, street addresses, and zip codes
Summary of what happened: On August 4 2022, Hold Security discovered a data dump containing the information of AT&T’s TV, internet, and landline customers on the dark web. The data belonged to both current and previous customers. The information included in the database matched up with AT&T internet areas, corporate addresses, and more. The data set included 28,511,318 records, including 22.8 million unique email addresses and 23 million unique SSNs. AT&T denied that the data was stolen from its systems.
Lesson learned: Your personal information is a hot commodity. When you sign up for services, you voluntarily share your information with those companies and inadvertently accept the risk of it being compromised.
6. Microsoft
Number of victims affected: 0
Type of information stolen: Unknown
Summary of what happened: On March 20, 2022, the hacker group LAPSUS$, also known as DEV-0537, announced it had breached Microsoft’s systems in a Telegram post. Microsoft confirmed the breach two days later. LAPSUS$ is responsible for several attacks against large organizations, including the Brazilian Ministry of Health, Samsung, NVIDIA, and Vodafone. Unlike other hacking groups, LAPSUS$ claims its data breaches. It also publicly seeks out employees and company insiders from tech and telecommunications companies to aid them in their efforts.
Lesson learned: Staying informed about security trends can help organizations minimize the impact of breaches.
7. CashApp
Number of victims affected: Roughly 8.2 million
Type of information stolen: Brokerage account numbers, financial information, full names, portfolio values and holdings, and stock trading information for one day of trading
Summary of what happened: In April 2022, CashApp’s parent company Block filed a report with the Securities Exchange Commission (SEC) about a data breach incident. A former employee had illegally downloaded customers' sensitive information on December 10, 2022, as an act of revenge following their dismissal. Due to the delay in reporting the incident, some customers had their money stolen. The incident resulted in a class action lawsuit filed against CashApp and Block.
Lesson learned: Businesses should implement tools that can detect breaches fast so that action can be taken immediately.
8. Crypto.com
Number of victims affected: 483
Type of information stolen: Millions of dollars worth of bitcoin and Ethereum
Summary of what happened: On January 17, 2022, cybercriminals bypassed 2FA to access user wallets and steal roughly $18 million in bitcoin, $15 million in Ethereum, and other cryptocurrencies. Crypto.com acknowledged the breach two days later after initially dismissing it. The company stated that it had reimbursed affected users, tightened its security measures, and audited its systems. It also introduced the Worldwide Account Protection Program (WAPP)—an insurance program that reimburses qualifying users up to $250,000 in lost funds.
Lesson learned: While 2FA is advisable, it can be bypassed. A password manager can prevent attacks that might leave your sensitive information exposed.
9. Flexbooker
Number of victims affected: More than 3.7 million
Type of information stolen: ID, photos, passwords, and driver’s license information
Summary of what happened: Between December 2021 and the beginning of 2022, Amazon’s AWS servers were compromised, and Flexbooker was breached. The hackers, Uawrongteam, infected the servers with malware and took over the system. Customers were unable to access their accounts, and Flexbooker couldn’t service customer accounts. This is known as a distributed denial-of-service (DDoS) attack. The stolen information was sold on dark web platforms, and many clients stopped using Flexbooker, which took a big hit.
Lesson learned: Flexbooker wasn’t Uawrongteam’s first victim. The hacking group had previously shared a data dump allegedly hacked from Racing.com and the Redbourne Group. Had Amazon been tracking the group’s nefarious acts, it could have prevented the attack and the financial consequences thereof.
10. PressReader
Number of victims affected: Unknown
Type of information stolen: Unknown
Summary of what happened: PressReader distributes digital magazines and newspapers for public consumption. In March 2022, the online newsstand distributor suffered a three-day attack that prevented the platform from publishing content from 7,000 local, regional, and international news sources. These news sources included large and small publications—including the New York Times, Forbes, Vogue, and The Guardian. In addition to the PressReader website, hackers also infiltrated and compromised the PressReader app and Branded Editions website, which experienced a network outage that Thursday.
Lesson learned: Always check your accounts for any suspicious activity and use a VPN service, especially when using public Wi-Fi or a friend or family member’s Wi-Fi. When in doubt, or if you suspect something is amiss, change your passwords and log out of your online accounts.
Don’t want to join the list of victims?
Data breaches can occur to large, medium, and small organizations in various industries—no industry is exempt. That’s why it’s essential that organizations keep their security software updated.
Below is a list of industries in which data breaches occur:
- Government departments
- Healthcare
- Pharmaceuticals
- Retail
- Finance
- Education
- Research
- Insurance
- Technology
- Telecommunications
- Construction
- Transportation
- Media and entertainment
- Agriculture
- Accommodation, etc.
Hackers can attack a system from opposite ends of the world. Thus, no matter how safe you think you’re, you can also fall victim to a data leak. The chances are much higher if you don’t use smart software to prevent cybercriminals from obtaining your personal data.
Protect your privacy with MacKeeper’s ID Theft Guard
When dealing with data breaches, time is of the essence. MacKeeper’s ID Theft Guard is a reliable data breach monitoring tool that scans the dark web for data dumps involving your email address. What’s more, all these scans occur automatically, with no need for you to get involved in the process. As a result, you stay safe and protected every day you use your Mac.
ID Theft Guard is simple to use and quickly secure your email address before anyone can steal your identity.
1. Download MacKeeper on your Mac
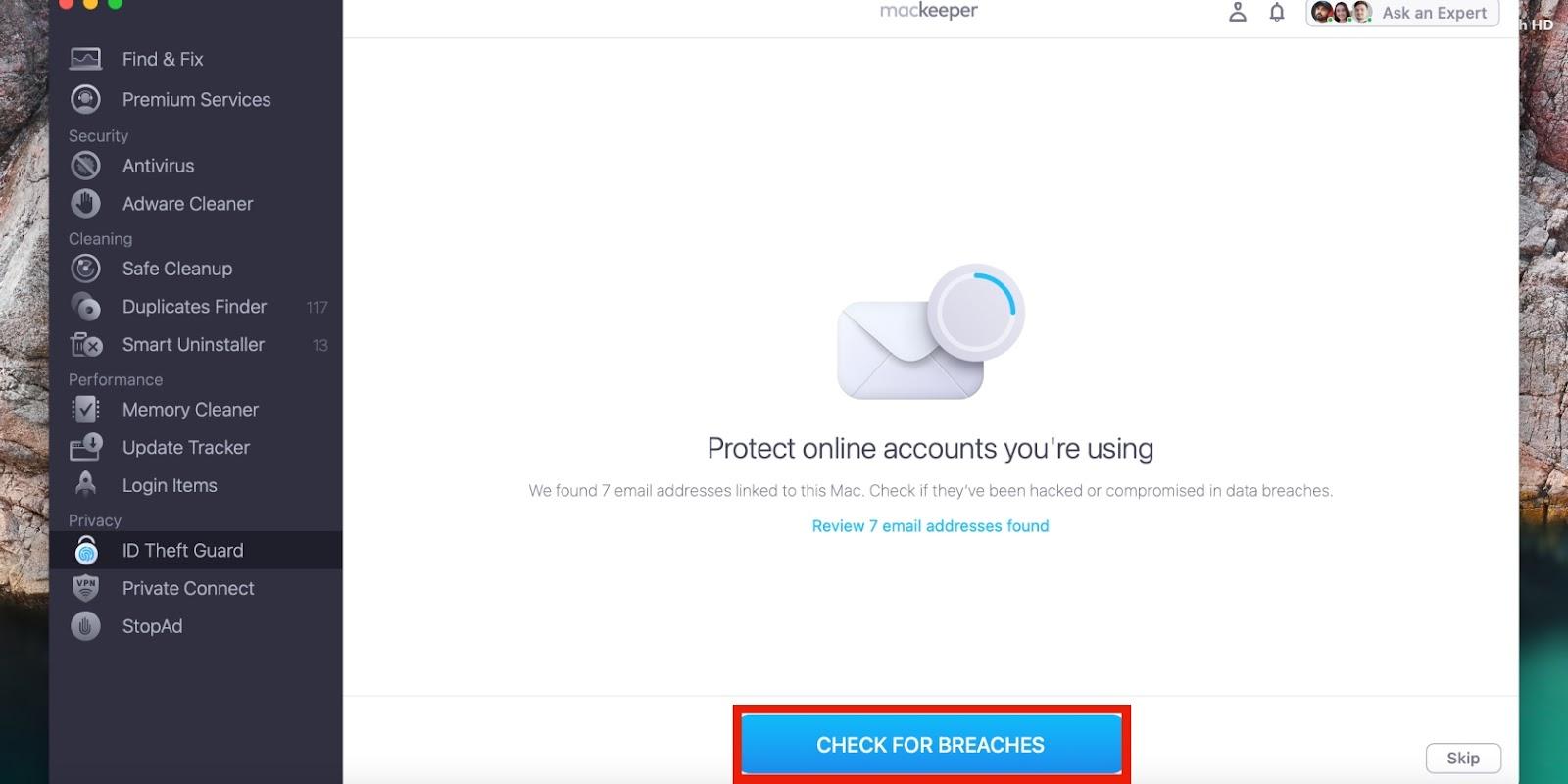
2. Click on ID Theft Guard in the left pane and click Check for breaches
3. Next, select the relevant email, click the Send code button, and follow the on-screen prompts to secure your email
4. For better security, make sure you’ve enabled the Data Breach Monitor tool for the ongoing scanning of data breaches on your device.
Keep your personal data locked
When it comes to data breaches, no one is safe. However, you can play your part in protecting your personal information.
Here’s what to do to avoid the risk of becoming a victim of data infringements:
- Create passwords that are difficult to guess
- Change your password if a company you have an account with was involved in a data breach
- Use a password manager
- Use a VPN service
- Set up multi-factor authentication
- Set up push notifications and emails for your accounts
- Don’t give your personal information to strangers or click on suspicious links.
Secure your data with MacKeeper
As we’ve established from the top 10 data breaches of 2022, you can’t take chances with your privacy, and you can never be too careful. Protect your personal information by using MacKeeper’s ID Theft Guard regularly to stay in the loop about data breaches affecting you.