Malware, or malicious software, is an umbrella term used to describe any programs or files that are harmful to your computer. It is software designed with the intention to gain access to or damage your computer without your knowledge or approval.
Here at MacKeeper, our job regarding malware is twofold.
First and foremost, we act as a malicious software removal tool. We scan our users' Macs for potentially harmful software and remove it from their devices once detected. Second, we share information about the importance of online security and keep our malware detection criteria transparent to anyone interested in this information.
The criteria MacKeeper uses to identify malicious software
Malicious software refers to various forms of harmful or intrusive software. This includes computer viruses, worms, Trojans, ransomware, spyware, adware, and other malicious programs.
From a technical point, malware can take the form of executable code, scripts, active content, and other software.
General criteria we use to detect malicious software:
- Malware is defined by its malicious intent, acting against the requirements of the computer user.
- Official programs supported by legitimate companies can be considered malware if they covertly act against the interests of the computer user.
- Potentially unwanted programs (PUPs) are programs that may be unwanted, even though users might have consented to download and execute them (under certain circumstances they may even cause harm to the computer user).
Detailed criteria we use for potentially unwanted programs or malicious software:
Other apps or unrelated app components are installed before obtaining the consumer's permission through an explicit user action during the installation process (PUP).
The application intentionally shows invalid information to the customer (Malware / PUP).
- The application intentionally shows invalid information in advertisements or pre-download landings (Malware / PUP):
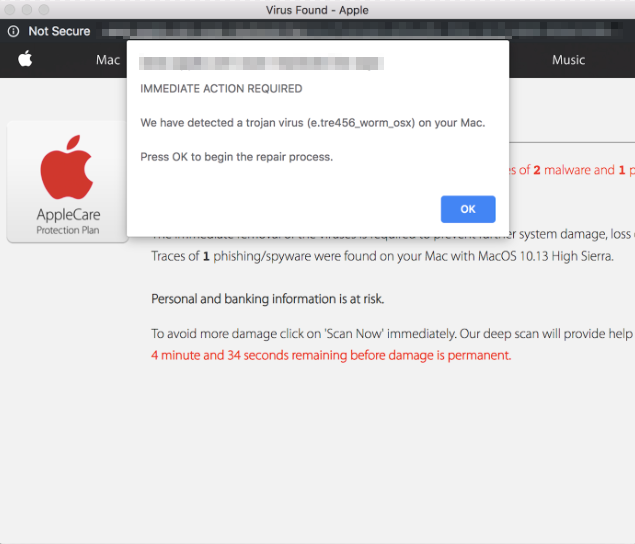
- The application intimidates or threatens the user to take action (PUP).
- The application is hiding and/or limiting the user’s ability to close/delete/disable or uninstall it (PUP).
- The application exploits a vulnerability (Malware).
- The application downloads a malicious program (Malware).
- The application claims to be from another vendor (Malware / PUP).
- The application claims to be another application (Malware / PUP).
- The application changes, installs, or uninstalls other apps or services and unrelated documents without the user’s permission (Malware).
- The application collects sensitive information without the user’s consent (Malware).
- The application impersonates or mimics a system, browser, or component message or prompt (Malware).
- The application replaces existing hyperlinks and/or hijacks to display advertisements without the user’s consent (Malware).
- The application automatically or unexpectedly sends spam, makes calls, or clicks on ads and links (Malware).
- The application attempts to evade the security investigation or detection and attempts to hide its behavior (Malware / PUP).
- Once disabled or deleted, the application replicates itself or with the help of another app (Malware / PUP).
- The application changes the browser’s homepage, default search engine, etc. without the user’s permission (Malware / PUP).
- The application changes system and/or network settings without user confirmation (Malware).
- An explicit, informed user consent is obtained before the application affects the integrity of other programs, including disabling/circumventing security and protection measures and intercepting/redirecting network traffic (unless this behavior is the value proposition of the app and is integral to the functionality and the stated purpose of the app.) (Malware).
- The application collects the user’s credentials (Malware).
- The application uses computer resources for purposes and activities other than stated in the EULA or Privacy Policy (Malware).
- The application uses available APIs to change the application’s settings and behavior. If no API is available, the app is not extensible (Malware).
- The application exposes the user’s sensitive information (PUP).
- The application acts like ransomware, i.e. blocks access to a computer system or specific files until a sum of money is paid (Malware).
- The application uses a vulnerable piece of code (PUP).
To keep our anti-malware activities as prompt and accurate as possible, we regularly review and, when necessary, update the criteria listed above.
We understand that in most cases, publishers of PUPs are not amateurs but top-level experts using their skills the wrong way. We just as well understand that the only way to push back against them is to encourage tech experts of the same (or higher) level to fight back.
For this reason, we created the Malware Research Lab—a team of security experts whose main focus is to protect MacKeeper users from malicious software and the potential harm it may cause to their Macs.