In this article you will find the following:
In this blog post, we’ve gathered the 22 most significant breaches that happened back in 2017. All of the reports were conducted by Chris Vickery — a data breach hunter, who had partnered with MacKeeper to provide reports on the 'hottest' security and data breaches on the MacKeeper blog.
This is the second post in a series of data breach reports. Go here to read the 2016 Data Breach Reports Archive.
Click on a data leak name to read the report:
- Militarysleep.org breach
- World Wrestling Entertainment 3 million email leak
- Harak1r1 the 0.2 Bitcoin ransomware attack
- SpaSurgica: Canadian plastic surgery customers' records leak
- Interpreters Unlimited: personal data of employees and customers leak
- Telemarketing company leaks nearly 400K of sensitive files
- IndyCar data leak
- PIP Printing and Marketing Services data leak
- Extensive breach at Intl Airport
- Amazon AWS issue takes down the internet
- MacKeeper Security researchers discover sensitive the United States Air Force data
- Schoolhouse data breach
- Report: 313 large databases went public
- Auto financing company leaks 500K+ of customer’s info online
- Global communication software: a massive amount of data online
- Mexican tourist tax refund company: leak in customer records
- MacKeeper Research Center discovers massive Elasticsearch infected malware botnet
- Auto tracking company leaks hundreds of thousands of records online
- Verizon wireless employee: online exposure of confidential data
- Report: virtual keyboard developer leaked 31 million client records
- Ashley Madison's private pictures went viral
- Report: cybercriminals steal voter database of the State of California
Essential reading and tools:
- With Mac security guide you'll dive deeper into macOS security settings
- Get a Mac antivirus that will guard your Mac in real-time
- Install a VPN for Mac to have a secure connection each time you use the internet
- Malware Removal Guide for Mac Owners will show you how to remove various kinds of malware
- How to Check Your Mac for Malware guide will tell you how to spot and remove malware from your Mac
- Run Have I Been Pwnd to check if your emails are in a data breach
- Spend a few minutes reading our guide on how to prevent a data breach
Militarysleep.org breach
Militarysleep.org is a patient portal where users can create their accounts, discuss treatment options, and ask questions about their sleep disorders. Researchers from the MacKeeper Security Research Center have discovered a publicly accessible Mongo database that contains the private medical data of thousands of military veterans who suffer from sleep disorders.
The database contained a total of 2+ Gigs database containing more than 1,300 messages (sensitive communications between patients and doctors) and personal data of more than 1,200 users, including their names, emails, personal cell numbers, unencrypted passwords, and military history/ service rank. The most damaging information discovered are the stored notes and chat logs where patients ask questions about sensitive medical issues they are experiencing and believing the communication is confidential. Many of the email addresses are @us.army.mil and we can assume treat both active and former military service members.
Medical privacy is extremely important for both citizens and military veterans and if details are leaked about their diagnoses and treatment, it could affect their current employment, future employment, security clearances or other areas of their lives. Even worse the fear that employers could discriminate against an applicant or employee based on their leaked medical records or likelihood of illness. This is why protecting medical records is so important and every step for cybersecurity must be taken.
The site is registered to Maryland-based Dr. Emerson Wickwire Ph.D. and according to his personal website “My research interests focus on biobehavioral sleep processes including sleep as therapy for the body and brain, the most common sleep disorders, sleep in special populations, and dissemination of best practices.”
Luckily, this database did not fall victim of the Harak1r1 the 0.2 Bitcoin Ransomware - a malicious actor who targets unprotected MongoDB all around the world. Shortly after we sent email notifications to the database was closed down, though without any word or comment from the developers.
We would like to thank Dissent from databreaches.net for assisting in covering/securing that breach. Please make sure to read her story here.
The Militarysleep.org database was discovered just one day after thousands of similarly misconfigured Mongo databases were infected and had all of the data removed and held ransom for 0.2 Bitcoin to recover their files. This unfortunate data leak may have just saved their data from being deleted by the Harak1r1 Bitcoin Ransomware. Earlier this week the MacKeeper Research Center discovered a database connected to Emory Healthcare were an estimated.
World Wrestling Entertainment leaks 3 million emails
World Wrestling Entertainment was also known as the WWE is a popular American entertainment company and promoter of professional wrestling. Although wrestling is their primary focus they also earn revenue from films, music, video games, product licensing, direct product sales, and more.
This Week Security Researchers from MacKeeper discovered two open and publically accessible Amazon S3 Buckets that contained a massive trove of information collected by third parties agencies specifically for WWE marketing purposes. We estimate that around 12 percent of all the information (several gigabytes) was set to “Public” access and available for anybody with an internet connection to view and download.
What data WWE leak contains
First of the unsecured Amazon S3 bucket contained a big grouping of emails in txt files. The data were from 2014-15 and contain fans' names, email, physical address, and results of a demographic survey of their fans by asking education, age and race, children's age, and children's gender. The total count of records was 3,065,805 and researchers checked to see if there were duplicates and in the sampling, it appears that they were all unique.
Data fields for 3M+ records:
action|wweuid|email|address1|address2|city|region|zipcode|countrycode|firstname|lastname|mi|gender|dob|source|source2|phone|title|favstar1|favstar2|favstar3|ethnicity|education|income|newsletterPref|childrens age|childrens gender|cableprovider|adddate|network
Despite all of the scripts and arguably staged matches they have a massive fanbase and following. WWE is watched by 15 million fans each week in the United State alone and in 2016 they announced that they are expanding into China giving them a potential new fanbase of 1.4 billion!
One of the archives stored with public access also included a configuration file with another WWE-related bucket name.
The second bucket was also partially (around 12-15 percent of data) set for public access and contained another giant portion of marketing and customer data, including billing details (addresses, user names, etc) of several hundreds of thousands of European customers from 2016.
The documents also included spreadsheets with social media tracking of the WWE social media accounts, like YouTube with weekly totals of plays likes, shares, comments, and a more in-depth look at how they manage their social media and gauge fan interactions. The list was even broken down by country so one would imagine that they can better target their ads or localized content.
Also, found was a large cache of Twitter posts, saved as search results for specified keywords related to WWE.
Big entertainment companies never share that kind of stuff publicly so it is a rare view into how the WWE uses big data to understand their fanbase and the content they produce.
Both buckets were secured within a couple of hours after we sent notification messages to the emails of the WWE Corp developers found in the first bucket. However, no answer or feedback was received as to how long these data were exposed, how many customers had their info exposed, and how many IP addresses may have accessed the database by now.
Despite being a global entertainment organization, very little is known about the behind-the-scenes inner workings of the privately held company. According to some estimates, the WWE is valued worth is as much as $4 Billion. Many of the folders were protected and did not allow external access. No information on the wrestlers or staff was accessible, but the leak of fan emails, names, and other data is a cybersecurity wake-up call.
This news comes on the heels of a series of hacks involving the WWE Divas’ leaked nude photos and even a sex tape scandal involving British superstar Paige. Also, hacked were WWE stars Maryse, Victoria, and Alexia Bliss.
Attention - Portions of this article may be used for publication if properly referenced and credit is given to MacKeeper Security Research Center.
Another victim of Harak1r1 the 0.2 Bitcoin ransomware
As you may know, medical records are protected in the US under Federal and State law. Hospitals, Doctors, and Insurers can face big fines and penalties when medical records are leaked online. On Dec 30th, 2016 the MacKeeper Security Research Center discovered a misconfigured Mongo database that contained hundreds of thousands of what appeared to be patient records and other sensitive information.
The IP was hosted on Google Cloud and results for domain names hosted on that address (Reverse IP) identified Emory Brain Health Center. On Jan 3rd, 2017 when the research team went back to review the data it was identified that the database had been a victim of the Harak1r1 the 0.2 Bitcoin Ransomware.
This non-traditional ransom method actually takes and removes the victims’ data and holds it until the ransom is paid. The data is wiped out completely from the database and is not simply encrypted like most common types of ransomware attacks. See details here.
In the original scan of the database by the MacKeeper Security Research Center, the estimated number of records exposed appeared to be more than 200 thousand! They were broke down into the following file names and records:
- 'Clinicworkflow' contained 6,772 records (medical record number, address, birth date, name, last name)
- 'Orthopaedics' contained 31,482 records (first name, last name, medical record number, address, email)
- 'Orthopaedics2' contained 157,705 records (cellphone, first name, last name, address, email)
- 'Orthoworkflow' contained 168,354 records (cellphone, first name, last name, birth date, address, email)
The following message was found in the database:
"mail" : "harak1r1@sigaint.org",
"note" : "SEND 0.2 BTC TO THIS ADDRESS 13zaxGVjj9MNc2jyvDRhLyYpkCh323MsMq AND CONTACT THIS EMAIL WITH YOUR IP OF YOUR SERVER TO RECOVER YOUR DATABASE !"
Text example of records and data collection that has now been extracted by the Harak1r1 the 0.2 Bitcoin Ransomware. This example was taken before the data was removed.
The big question: If the database discovered by the MacKeeper Security Research Center did in fact belong to Emory Healthcare. Have they taken the proper steps to inform their customers and the authorities regarding this data theft and breach?
In cooperation with Dissent from databreaches.net, we have reached out to multiple contacts in an attempt to identify the connection to Emory Healthcare or get a comment regarding how they plan to recover their data or notify patients.
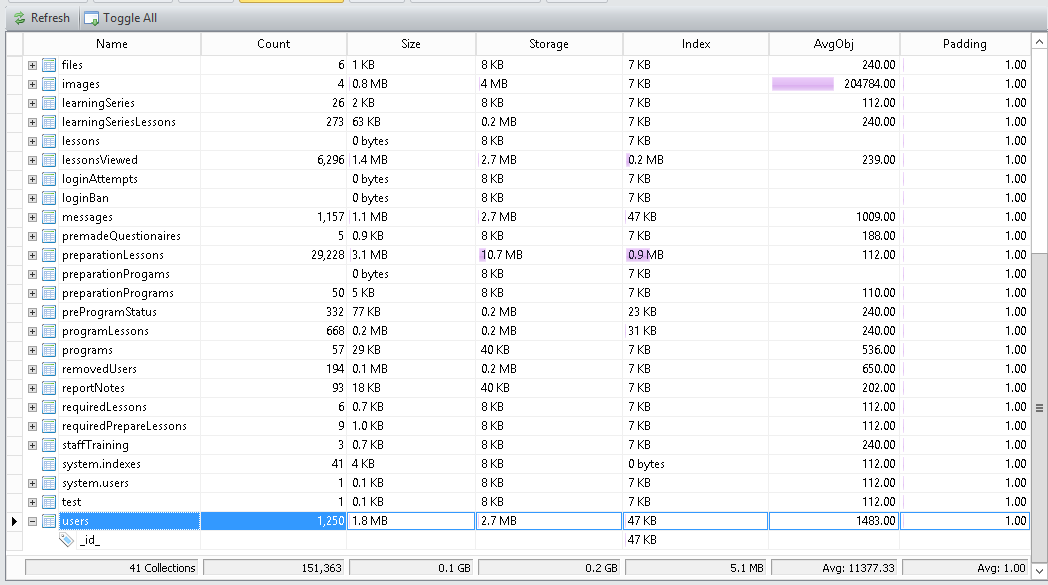
SpaSurgica: Canadian plastic surgery leaks customers' records
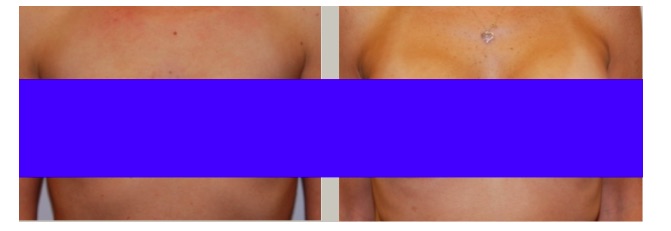
The files contained before and after pictures of breast augmentation, implants, and reduction. SpaSurgica also offers labial reduction, liposuction, and a wide range of plastic surgery options that many customers would want private. The pictures, descriptions, and medical history of each patient gives an intimate look at what type of data was leaked. These are not just home addresses and medical records, these are intimate pictures of patient's bodies. There was also access to unencrypted text files containing usernames and passwords for accounts, printers, and other password protected protected logins.
The MacKeeper team are grateful to Dissent from databreaches.net who participated in this investigation and helped to notify Dr. Mohamed Elmaraghy’s office of the leak. Access has since been closed and is no longer publically available. We never heard back from SpaSurgica, although several notification emails were sent immedidately after discovery.
Read more on her story here.
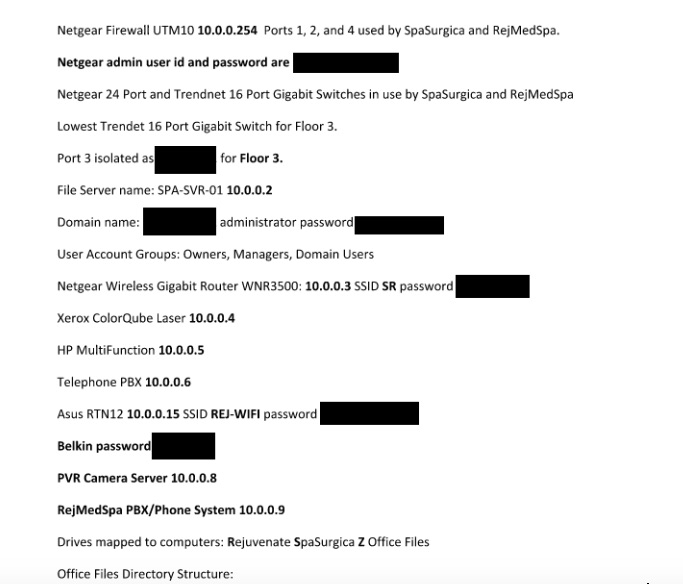
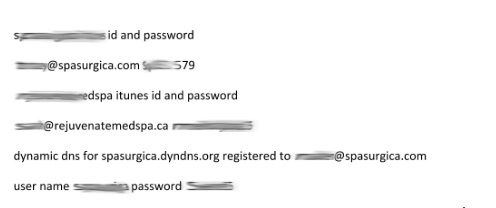
Network infrastructure passwords in plain text.
Patient Pictures archive contained hundreds of images.
The patients' names are associated with the images.
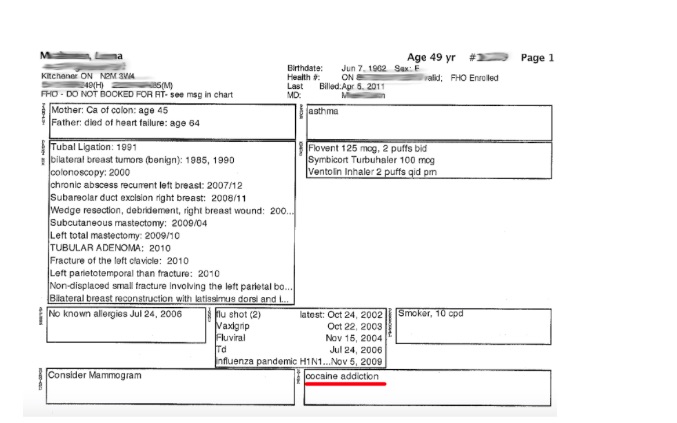
Medical records can be extremely private and sensitive. This is just an example of one of the thousands of scanned or fax files shows a patient who not only shared how her parents died and every major medical issue she has faced, but also included details about cocaine addiction. Drug addiction and health records unfortunately can influence employment or how employers view employees with private medical conditions or challenges.
Canadian law protects patients in data leaks
According to the website of the Information and Privacy Commissioner of Ontario there is a strict process regarding the theft or leakage of private medical data. Under the Personal Health Information Protection Act, 2004 (PHIPA), physicians are obligated to keep their patients’ personal health information confidential. PHIPA also provides a legal obligation on physicians to maintain and comply with information practices that keep their patients’ personal health information protected against theft, loss or unauthorized use or disclosure. If personal health information is stolen, lost or accessed by unauthorized individuals.
The law requires containment and notification:
If faced with a privacy breach, there are two priorities that must be addressed immediately:
- Containment: Identify the scope of the potential breach and take the steps necessary to contain it.
Notification: Affected individuals must be notified as soon as possible. - Investigate and Remediate: once the breach is contained and the affected parties are notified, you must conduct an internal investigation.
***
Interpreters Unlimited personal data leak
The device contained the private information (our estimation is 4,500+ records) of clients, employees, salary data, social security numbers, emails, and much more sensitive data in plain text as part of Excel spreadsheets and .txt files.
Special folders included all server access details, all email logins, passwords for almost every employee.
The website’s technical admin is listed in the Whois registration and there were a trove of personal documents stored on the device that belong to IT manager.
As a general rule Social Security Numbers should never be stored in a plain text document and when combined with names, addresses, emails and other identifiable information it provides cybercriminals with all of the information they need.
The data discovered by MacKeeper researchers even had the number of money translators earned with the company the previous year. This one document provides enough information that would allow criminals to file fake tax returns, get loans, or other forms of fraud.
Interpreters Unlimited offer translation services such as onsite interpretation, video, phone, and a range of other services. According to their website “We act as a “matchmaker,” finding you the best-fit language service that suits your needs”. Their client profile includes companies like Google, Boeing, United States Postal Service, and others.
We have been working on this case together with Zack Whittaker from ZDNet, who was able to contact the company's president and alert him on the incident (our initial notifications sent via email to the company's IT manager were left unnoticed). NAS device has been isolated. The company is seeking counsel and a third-party security audit company. But the company will be informing people — the translators — of the exposure.
The data was streaming for "four to six months," he said.
You can read Zack's story at ZDNet.
Telemarketing company leaks nearly 400K of sensitive files
Researchers from the MacKeeper Security Research Center have made one of the biggest discoveries to date with several hundred thousand files publically available. The files belong to a controversial Florida based marketing company VICI Marketing LLC and include thousands of audio recordings where customers give their names, addresses, phone number, credit card numbers, CV numbers and more. In 2009 VICI Marketing LLC agreed to pay $350,000 to settle a complaint by the Florida Attorney General's Office that the firm obtained stolen consumer information and did not take proper steps to ensure data was acquired legitimately. Researchers have confirmed that despite the fine and penalties they have still not secured customer or company data and there is a date range of recordings going back several years. Under the agreement: If the terms of the injunction are violated, Vici could be subject to a $1 million civil penalty.
There is enough information in each call to provide cyber criminals with all they need to steal the credit card information or commit a wide range of crimes. Some of the recordings do not warn customers that the calls are being recorded or stored. Eleven states require the consent of every party to a phone call or conversation in order to make the recording lawful. These "two-party consent" laws have been adopted in California, Connecticut, Florida, Illinois, Maryland, Massachusetts, Montana, New Hampshire, Pennsylvania and Washington.
Improper data storage or misconfigured databases can happen to companies big and small, but for a company who has already paid a hefty price and has been the subject of regulatory violations it seems like they would take cyber security more seriously. In the 2009 case where they were accused of obtaining stolen consumer information VICI's lawyer, Robby Birnbaum claimed "We don't have proof of that". Under the terms of the 2009 settlement Vici is permanently prohibited from acquiring or using data without due diligence, using data of unlawful or questionable origin, accessing and using data for consumer telemarketing without background due diligence, and unlawful telemarketing.
The files that The MacKeeper Security Researchers have discovered contains hundreds of thousands of records and could take several weeks to go through them all and It is unclear if the sensitive data is being sold or acquired by 3rd parties. Researchers have downloaded a 28 GB copy of the backup for verification purposes and will securely delete the publically available documents once the case is closed. MacKeeper works closely with law enforcement and US Homeland Security in cases where data becomes part of a criminal or civil investigation. There is no suspected wrongdoing at this time other than leaking as many as 17,649 audio recordings with credit card numbers and private customer files.
There is also 375,368 audio recordings that can be qualified as "cold calls", with some of those containing personal information as well.
The internet if full of complaints of how VICI Marketing LLC operates or claims and allegations from former employees. When searching for customer reviews and employee comments we discovered a blog post describing how VICI would give customers a promotional gift if they only pay for the shipping. They offered Skin DM/RejuvaGlow cream that was supposed to cost $3.95 and ended up costing $92.61 after everything was over. A former employee by the name of Justin Tyme says:
“For everyone's knowledge the name of the actual company ripping you off is VICI Marketing LLC, it is a company based out of Largo FL. I worked here for a period of time not knowing what kind of scams they were pulling on people, but it didn't take me long to realize what was REALLY going on, It would take ages to explain in detail the elaborate scam these people have going on, but what I can tell you is that they advertise these products (which usually can be purchased in drug stores for $20 or less) in hopes that the consumer will either not read the terms and conditions, or simply forget to call in and cancel…and believe me IT HAPPENS OFTEN.
By the time the consumer realizes what has happen they have already been bill in excess of $100 or more….when the customer calls in for a refund, they make it sound like you can't get one by offering them to keep the products and only giving them partial refunds. Im sure there are some of you who returned the product to sender and refused shipments right? And when you call in to ask about your refund your told that you can't have one because you didn't send the product back properly and it wasn't processed back into the warehouse!!! The very same person telling you that can clearly see in your account that the product has been return successfully but they mark it “no RMA” so the company knows not to give your money back.”
Although we can not verify the claims of former employees many of the complaints online tell the same story and describe exactly the same sales and billing methods.
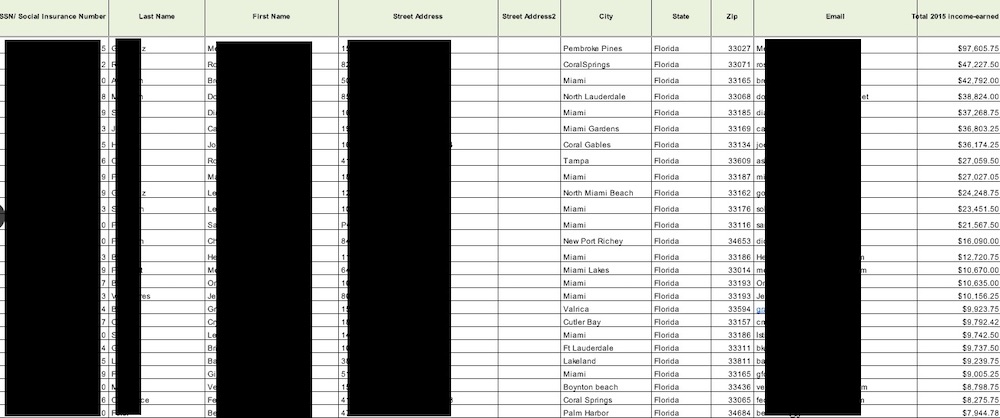
IndyCar data leak
The majority of these backups appear to be merely operational, but what stands out are the Indycar employee login credentials as well as the 200k user accounts containing such fields as email, physical address, first and last name, password hash, username, security question and answer, date of birth, and gender. Which essentially makes the find an identity theft treasure trove.
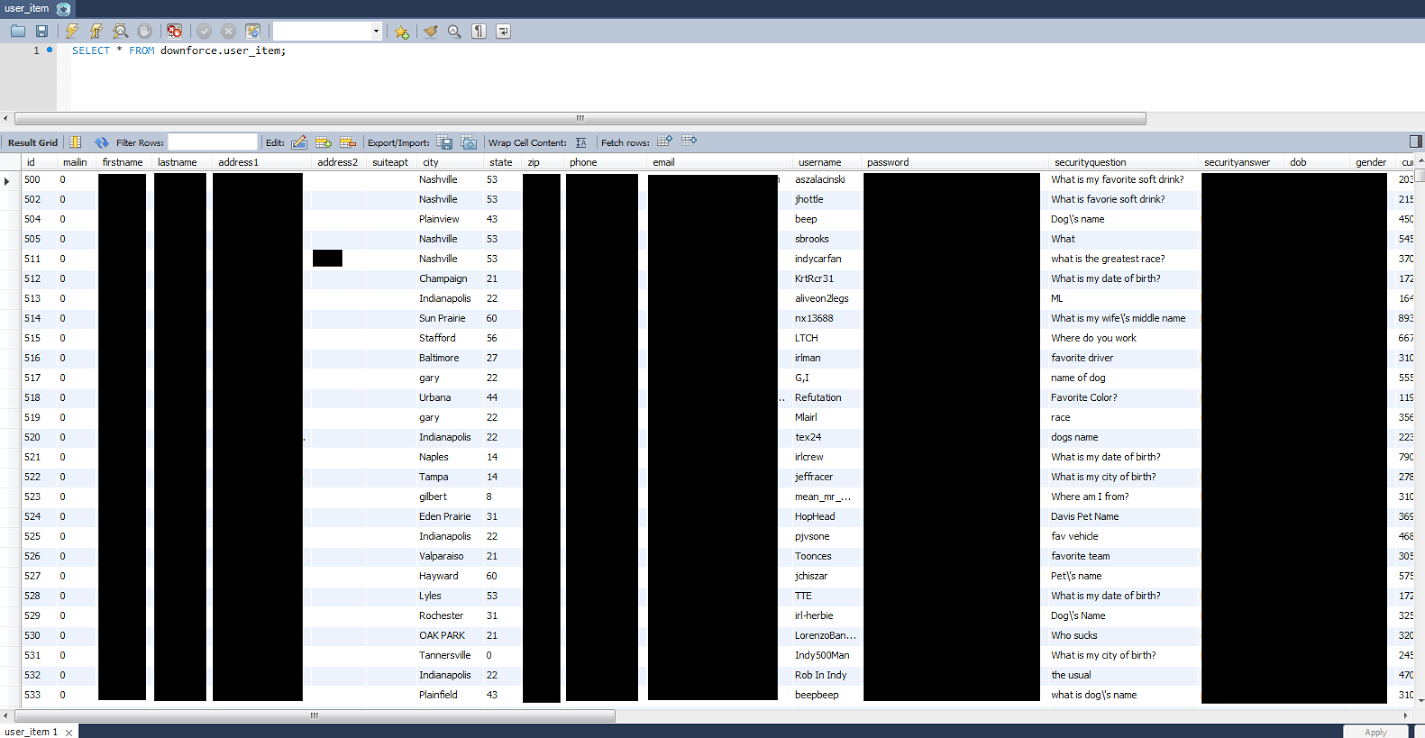
It’s important to point out that the Indycar bulletin board these accounts come from has since been retired. So, there is no need to change your Indycar forum login password. However, if you’re the type of person that reuses passwords (and it’s a shame that most people are), then you should reset any accounts that might be using the same password. If malicious folks came across this data set, they could be deciphering those passwords and attempting to use them on your other online accounts right now.
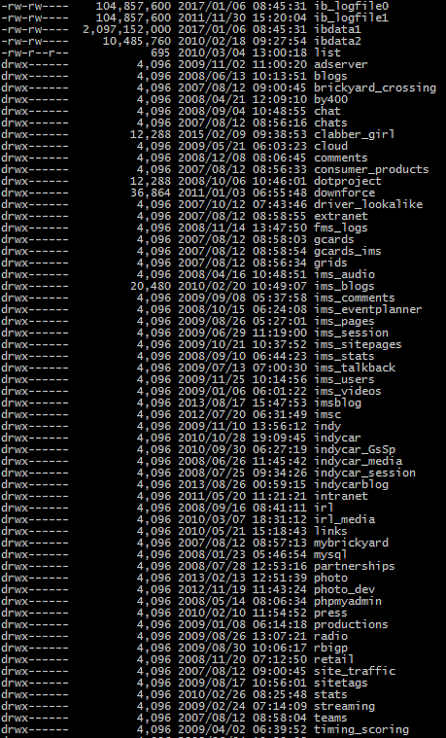
That leads me to something I’ve wondered for a while now- Why do companies hold on to password hashes long after the associated site has been shuttered? That’s nothing but liability. They are putting customers at risk for no gain. There was absolutely nothing for Indycar to gain by holding on to these password hashes. And now they are faced with negative PR as word of the situation gets out to racing fans.
I can only assume the attorneys and risk-management folks working for Indycar were unaware that defunct forum logins were being stored. Taking big risks, with zero chance of reward, is not how those types of people keep their jobs. If you’re reading this, and you manage risk at a large company, you should really ask your IT staff two important questions:
- What are we storing?
- Do we really need it?
PIP Printing and Marketing Services data leak
The majority of 400+ GB server is dedicated to designing files and images relating to the printing business. The most sensitive information is contained within the “Outlook archives” and “Scans” folders. These contain around 50+GB of scanned documents relating to court cases, medical records, well-known companies, and celebrities. There is an archive of correspondence where the company's clients ask managers to make copies of the attached documents. This archive contains more than 2,200 messages and some of them have credit card numbers and billing details in plain text.
PIP Printing and Marketing Services, a printing, and design company, is an award-winning printing and production company that has franchise locations all over the US and ranks among Entrepreneur Franchise 500.
This is just another example of how digital our lives have become and even something as simple as printing documents can expose customers’ sensitive data. MacKeeper Security recommends that any company that receives and stores sensitive customer data take every possible step to secure and protect it.
Among sensitive data: documents of former American professional football players, with data, included NFL retirement info, Social Security Number,s and some medical information; thousands of confidential files of Larry Flynt’s Hustler Hollywood retail stores. The files date back as far as 2010 and include HR documentation, internal investigations, sales numbers, goals, and profit and loss statements for each store.
Once again shows us the dangers of any company big or small not properly securing their data online. Leaks can be more than just embarrassing when they expose confidential store sales data and internal communications.
Important note
The information discovered by the MacKeeper Security Research Center was publically available and no password is needed to access the data.
First, it appeared on our radar back in late October 2016. Despite our attempts to notify the printing company, our calls and emails were never addressed seriously. We also recorded a call with receptionist who was acting weird and not willing to transfer the information further.
We are thankful to Tom Spring of Threatpost who assisted in this case and conducted his own investigation. See more details by following his story on Threatpost: https://threatpost.com/printing-and-marketing-firm-leaks-high-profile-customers-data/123530/
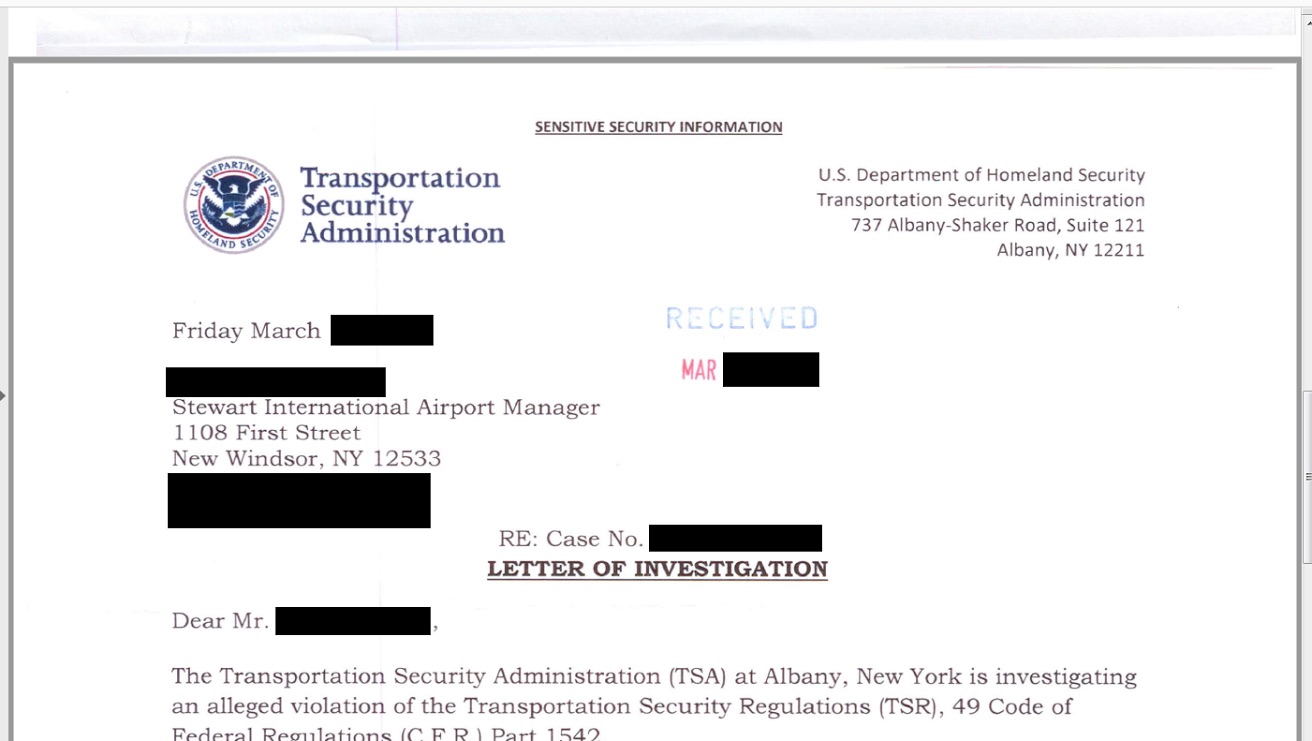
Extensive Breach at Intl Airport
The leaky data set includes everything from sensitive TSA letters of investigation to employee social security numbers, network passwords, and 107 gigabytes of email correspondence. Until I notified the facility’s management this past Tuesday, there existed a real risk to the security and safety of this US airport.
This is an important case study of how business practices can result in data breaches. According to the materials present, the Port Authority of New York & New Jersey contracts out management of Stewart International to a private company named AvPORTS. That company then contracts with a sole IT guy that is only on-site two or three times per month.
You cannot expect one person to maintain an airport network infrastructure. Doing so is a recipe for security lapses. This is a classic example of what can go wrong with privatization. For-profit companies have every incentive to, all too often, prioritize revenue over best practices.
This is emphasized by the AvPORTS incident response performance. In an industry at the level of airport management, every employee needs to have at least cursory data breach readiness training. The first person I spoke with at AvPORTS was very nice to me, but at one point asked me if this “could wait until tomorrow”.
The answer to that question is no. When your company is leaking government-created documents with phrases such as “Confidential”, “For Official Use Only”, and “Unauthorized release may result in civil penalty or other action”, you cannot simply wait until tomorrow. It requires immediate action.
Initial response
I was somewhat relieved when an AvPORTS COO did call me back a few minutes later, around 12pm Pacific US time. He assured me that I would be hearing from their IT staff shortly to further investigate and remedy the situation.
Three and a half hours later I had not heard back from anyone and the data breach was still live. I decided to call the Port Authority. They instructed me to call the Stewart terminal and provided a phone number. During that next call, to the terminal operators, the server’s exposed port was closed off to the outside world. It’s unknown whether or not this was coincidental timing, as the terminal guys claimed that their department cannot make such a change.
The IT guy
A few hours later, around 7 pm Pacific, I finally received a call from the IT guy. The conversation took an initial downturn. He informed me that I had committed a crime by downloading this data and used the analogy of breaking in and stealing items from someone’s home (which could not be further from the truth).
Fortunately, the conversation evened out when I explained to him that my actions were in no way criminal. The device had been configured in a manner that was distributing these files publicly without a single username, password, or another authentication measure in place. Regardless of intention, this machine was, in essence, acting as a public web server.
Possible explanations
So, how did this happen? Here are some clues—The IT guy I spoke with informed me that a few months ago the airport had experimented with using a backup software known as ShadowProtect. I was informed that part of the process involved opening port 873 on the firewall and that the ShadowStream service, part of ShadowProtect, may have been utilizing some aspect of the remote synchronization service (rsync). This is just what I was told in that conversation.
That may be a bit of a red herring though and only part of the puzzle. Within the backups, I was able to locate an email chain indicating that AvPORTS purchased at least one Buffalo Terastation backup NAS device in March of 2016.
Those of you that keep up with my work may recall this same make and model of NAS device being at the center of a recently reported Ameriprise Financial data breach. In fact, I have made several other recent breach findings involving this particular device.
My hypothesis is that there may be a default opening of port 873 on some number of Buffalo Terastations. Keep in mind that port 873 had been intentionally opened on Stewart International’s firewall during part of the experiment with ShadowProtect.
The current working theory is that these two factors aligned and resulted in a breach scenario. But all of this begs the question: Would such an oversight happen if AvPORTS employed even one full-time IT guy at Stewart?
You get what you pay for, even in IT.
For more info, see the ZDNet article.
***
Attention - Portions of this article may be used for publication if properly referenced and credit is given to MacKeeper Security Researcher, Chris Vickery.
Amazon AWS issue takes down the internet
It’s still not clear what was the problem with the services. Furthermore, the problem still persists and partially affects the East Coast-based websites. As Amazon says on its official Twitter account, “S3 is experiencing high error rates. We are working hard on recovering”.
S3 is experiencing high error rates. We are working hard on recovering.
— Amazon Web Services (@awscloud) February 28, 2017
AWS is an Amazon cloud storage service that is popular with such large companies as Netflix, Adobe Systems, Airbnb, BMW, etc. MacKeeper also relies on AWS to keep operations running smoothly. But the number of small businesses that use AWS is hard to imagine.
You can check the latest fixes updates on the Amazon Service Health Dashboard.
However, many Internet users have found the services outage funny and gave advice to Amazon:
Hey @amazon, have you tried turning it off and on again?
— The Practical Dev (@ThePracticalDev) February 28, 2017
MacKeeper Security researchers discover sensitive the United States Air Force data
Researchers discovered a trove of sensitive documents that included Personnel by Eligibility and Access Reports that contained the names, rank, social security numbers of several hundred service members. At the bottom of each page is a notice that reads:
“Under the Privacy Act of 1974, you must safeguard personnel information retrieved through this system. Disclosure of information is governed by Title 5, United”
The most shocking document was a spread sheet of open investigations that included the name, rank, location, and a detailed description of the accusations. The investigations range from discrimination and sexual harassment to more serious claims. One example is an investigation into a Major General who is accused of accepting $50k a year from a sports commission that was supposedly funneled into the National Guard. There were many other details from investigations that neither the Air Force or those being investigated would want publically leaked.

There is a file that contains Defense Information Systems instructions for encryption key recovery. This is a comprehensive step-by-step guide of how to regain access to an encryption key and all of the urls where someone can request information regarding a Common Access Card (CAC) and Public Key Infrastructure (PKI). The possible danger of leaking the email addresses and personal information of senior military officials is that through social engineering and other methods, bad actors could potentially gain access.
Among the sensitive documents was a scanned image of the Lieutenant’s JPAS account (Joint Personnel Adjudication System) from the Department of Defence. This included the login URL, user ID, and Password to access the system. JPAS accounts are only provisioned for authorized individuals and we can assume there would be classified information to anyone who would access the account. The database also included a copy of the North Atlantic Treaty Organization (NATO) Information Security Training Manual and many other documents that may or may not be publically available.
The device has since been taken offline and it is unclear if anyone other than members of the MacKeeper Research Team had access to the files or how long they were available.
Please see more details on the story in Zack's feature at ZDnet: https://www.zdnet.com/article/leaked-us-military-files-exposed/
Schoolhouse data breach
Schoolzilla, a student data warehousing platform, made the all-too-common mistake of configuring their cloud storage (an Amazon S3 bucket) for public access. I discovered the bucket after noticing a few other unsecured buckets related to the Tableau data visualization platform. There was an exposed “sz.tableau” bucket, so I started looking for other “sz” iterations. That’s when I came across “sz-backups”, which turned out to be the main repository for Schoolzilla’s database backups.
I downloaded several of the production backups, the largest was titled “Web_Data_FULL” and weighed in at 12 gigs. After loading them into a local MSSQL instance I did some review and concluded that this was most likely real student data and did indeed come from Schoolzilla. The possibility of a false-flag operation is always in the back of my head (a scenario in which an unscrupulous company creates a false data breach that appears to originate from a competitor).
Schoolzilla was quick to respond when I submitted a data breach notification ticket. They secured the data and opened dialogue with me to learn the full extent of the issue. I applaud their incident response. This was the first situation of its kind for them and they reacted professionally. It must have been grueling for the CEO to phone each client and relay the unpleasant news, but they did it within only a few days of my report.
Additionally, Schoolzilla understood the problem and took responsibility. They did not try to shoot the messenger or claim that I had somehow “hacked” them. That’s worth an extra-large gold star on the board for them.
Unlike most reports, I do not have any redacted screenshots to share for this one. The sheer volume of private student data, including scores and social security numbers for children, convinced me that it should be purged from my storage in an expedited fashion. I did however seek guidance from the US Department of Education before overwriting my copies just in case they wanted them preserved for any investigatory purposes. Unfortunately, the Department’s voicemail box is currently full and I could not leave a message.
A message from Schoolzilla’s CEO regarding the situation can be found here: https://schoolzilla.com/commitment-information-security/
Information for editors:
The MacKeeper Security Research Center was established in Dec 2015 with the goal of helping to protect data, identifying data leaks and following a responsible disclosure policy. Our mission is to make the cyber world safer by educating businesses and communities worldwide. Many of our discoveries have been covered in major news and technology media, earning the MacKeeper Security Research Center a reputation as one of the fastest-growing cyber data security departments.
Auto financing company leaks 500K+ of customer’s info online
As part of our research on publicly available Amazon AWS S3 buckets, MacKeeper Security Researchers discovered yet another repository, (mis)configured for public access, which contained 88 megabytes of spreadsheet documents in *.csv format with names of hundreds of auto dealerships around the United States.
Upon further investigation we were able to identify what appeared to be customer purchase information (such as full names, address, zip,last 4 SSN digits), credit scores (FICO auto scores), year, makes, and models. Once it was clear this was automotive financing data we found the name of who we believed were associated with the exposed data.
The files allegedly belong to Alliance Direct Lending Corporation, an automobile finance company in that refinances auto loans or uses a network of dealers to match with pre-qualified buyers.
The leaked data contained 124 files (each of them containing from 5 to 10 thousand records, which brings us to 550K - 1M customer details in total), with financing records broken down by dealerships and 20 audio recordings of customers agreeing to auto loans or refinancing of auto loans. These consent calls were the customers agreeing that they understood they were getting an auto loan, confirming that the information was correct and true. They included the customers' name, date of birth, social security numbers, and phone numbers. These calls were in both English and Spanish.
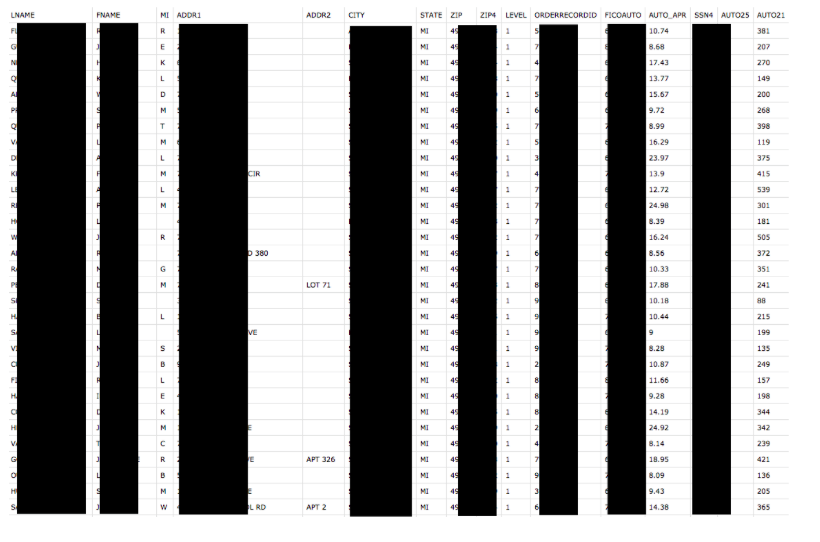
A member of MacKeeper Security Research called and spoke with an IT administrator who looked at the url of the publically accessible data and confirmed that it appeared to belong to Alliance Direct Lending. When searching online for Alliance Direct Lending it appears that they really do have a solid reputation and nearly all of the reviews are positive, but data breaches can and do happen. This is yet another wake up call for anyone dealing with financial data, social security numbers, or other sensitive data to audit your data often. One simple misconfiguration could allow your entire organization's data storage publically available online to anyone looking for it.
Did anyone else see this data?
It is unclear if anyone other than security researchers accessed it or how long the data was exposed. According to the bucket properties, it was last modified on Dec 29, 2016. It contained 210 public items and 790 private ones (not available but listed) - logs. The IT Administrator claimed that it had only recently been leaked and was not was not up for long. He thanked us for the notification and the data was secured very shortly after the notification call.
The danger of this information being leaked is that cyber criminals would have enough to engage in identity theft, obtain credit cards, or even file a false tax return. Alliance Direct Lending is based in California where the law requires notification of a breach when a California resident's unencrypted personal information is compromised. California was the first state in the U.S. to require notification of security breaches (its law became effective in 2003).
Information for editors:
The MacKeeper Security Research Center was established in Dec 2015 with the goal of helping to protect data, identifying data leaks, and following responsible disclosure policy. Our mission is to make the cyber world safer by educating businesses and communities worldwide. Many of our discoveries have been covered in major news and technology media, earning the MacKeeper Security Research Center a reputation as one of the fastest-growing cyber data security departments.
Troy Hunt did a great job describing all details about that, so this is why I have reached out to him first to see if this dump is something special.
After running a sample set at his HIBP project, Troy identified 243,692,899 unique emails, with almost every single address is already in HIBP, mostly centred around the big incidents.
And while it is not the news itself, the availability of this data almost publicly (I mean, unprotected MongoDB equals publicly) is alarming.
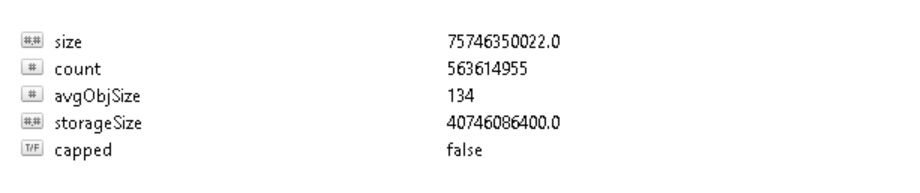
During our research, we were surprised to see as many as 313 large databases, with a size over 1GB, with several terabytes of data, hosted in the US, Canada, and Australia.
The database in question is hosted on a cloud-based IP, and it is unclear who actually owns it. We sent notification emails to the hosting provider, but usually, it is not the quickest way to shut it down.
After a series of ‘ransomware’ attacks targeted on MongoDBs left without authorization in the beginning of this year, I was not sure if somebody still uses early versions of Mongo where default configuration is possible. It appears that “Eddie” did.
Database is 75+ gigs in size and contains data structured in a readable json format which included at least 10 previously leaked sets of data from LinkedIn, Dropbox, Lastfm, MySpace, Adobe, Neopets. RiverCityMedia, 000webhost, Tumblr, Badoo, Lifeboat etc.
The lesson here is simple: most likely, your password is already there and somebody might be trying to use this just now. So isn't that a good time to change it now?
***
Attention - Portions of this article may be used for publication if properly referenced and credit is given to MacKeeper Security Research Center.
313 large databases went public
Troy Hunt did a great job describing all details about that, so this is why I have reached out to him first to see if this dump is something special.

After running a sample set at his HIBP project, Troy identified 243,692,899 unique emails, with almost every single address is already in HIBP, mostly centred around the big incidents.

And while it is not a news itself, the availability of this data almost publicly (I mean, unprotected MongoDB equals publicly) is alarming.
During our research, we were surprised to see as many as 313 large databases, with size over 1GB, with several terabytes of data, hosted in US, Canada and Australia.
The database in question is hosted on a cloud-based IP, and it is unclear who actually owns it. We sent notification email to the hosting provider, but usually it is not the quickest way to shut it down.
After a series of ‘ransomware’ attacks targeted on MongoDBs left without authorization in the beginning of this year, I was not sure if somebody still uses early versions of Mongo where default configuration is possible. It appears that “Eddie” did.
Database is 75+ gigs in size and contains data structured in readable json format which included at least 10 previously leaked sets of data from LinkedIn, Dropbox, Lastfm, MySpace, Adobe, Neopets. RiverCityMedia, 000webhost, Tumblr, Badoo, Lifeboat etc.
The lesson here is simple: most likely, your password is already there and somebody might be trying to use this just now. So isn't that a good time to change it now?
***
Attention - Portions of this article may be used for publication if properly referenced and credit is given to MacKeeper Security Research Center.
Global communication software left a massive amount of data online
Online communication has become a vital part of today's business environment and it is essential that business owners have tools and analytics to gauge efficiency, communication, and a range of data sets. One of the top companies that provide cloud-based unified communications has just leaked more than 600GB of sensitive files online.
The MacKeeper Security Center has discovered not just one but two cloud-based file repositories (AWS S3 buckets with public access) that appear to be connected to the global communication software and service provider BroadSoft, Inc. They have created an infrastructure for cloud unified communications tools that can be service provider hosted or cloud-hosted by BroadSoft. The publically traded company has over 600 service providers across 80 countries and supports millions of subscribers according to their website. Their partners are some of the biggest names in the communication business, telecom, media, and beyond, including Time Warner Cable, AT&T, Sprint, Vodafone among many other well-known companies. When 25 of the worlds top 30 service providers by revenue all use BroadSofts infrastructure and with so many subscribers it is easy to see that this data leak could have a massive reach.
BroadSoft business applications
- UC-One = single, integrated business communications solution
- Team-One = chat, take notes, track tasks and share files in organized workspaces.
- Also provides access to Google, Drive, Salesforce and other apps? Team-One is integrated with over 50 other popular apps.
- CC-One= omni-channel, cloud contact center solution that uses predictive analytics to lower operating costs and improve business performance.
- Hub =unified experience, bringing together BroadSoft Business and cloud apps
Other BroadSoft Business Platforms include BroadWorks, BroadCloud, Carrier, PaaS, Reseller, BroadSoft Mobility.
How the leak happened
The problem is that the repository was configured to allow public access and exposed extremely sensitive data in the process. They used Amazon's cloud but misconfigured it by leaving it accessible. Amazon AWS buckets are protected by default but somehow were left publically available. It is most likely that they were forgotten by engineers and never closed the public configuration. This would allow anyone with an internet connection to access extremely sensitive documents. Not only could they access the documents but any “Authenticated Users” could have downloaded the data from the URL or using other applications. With no security in place just a simple anonymous login would work.
This leak shows once again just how insecure data can be when improper security settings are used. In this instance the same mistake leaked the data and information of potentially millions of BroadSofts customers and that their partners service. This is not unique to BroadSoft and happens to companies big and small, but what does stand out is the size and scope of their business. Their infrastructure and portfolio of applications is used by millions of customers and many of them had their data exposed. It is unclear if BroadSoft will be notifying affected customers of this data exposure or if the partner companies who use their infrastructure will.
How it was discovered
In July MacKeeper Security researchers discovered an Amazon S3 cloud-based data repository that was connected to the WWE (World Wrestling Entertainment) hosted on the public 'wwe-test' S3 domain. This raised the flag that many administrators could potentially open a back up for testing and never close it. After the discovery researchers began testing other variations of the '-test' suffix and came across 2 of the connected repositories (one using the underscore sign '_' - not recommended by Amazon). Searching for the test resporsities is how it was discovered and we can only assume there are many more cloud-based data leaks actively available that started out as a testing ground, but were never secured.
On Aug 29th a security notice was sent to engineers based in BroadSofts Indian office (Bangalore) whose email communications was found in the repository. He replied “Who gave you my contact and it does not belong to us”. Then ironically one of the two repositories was closed to public access almost immediately after the notification. This would logically conclude that engineers may have been trying to do damage control by denying that the 600GB of data belonged to Broadsoft or their clients.
The second bucket was quickly secured only after a notification email to Charter-related people was sent.
What the leak contained
In short, the repository contained a massive amount of sensitive information and researchers estimate It would take weeks to fully sort through all of the data. The most potentially damaging discovery was the fact that it contained internal development information such as SQL database dumps, code with access credentials, access logs, and more. These are all things that should not be publicly available online. The two repositories contained thousands and thousands of records and reports for a number of Broadsoft clients with Time Warner Cable (TWC) appearing to be the most prominent and including applications like Phone 2 Go, TWC app, WFF etc.
Much of the internal development data apparently saved by Broadsoft engineers related to Time Warner Cable, Bright House Networks (BHN/Charter). For example “User Profile Dump, 07-07-2017” text file contains more than 4 million records, spanning the time period 11-26-2010 - 07-07-2017, with Transaction ID, user names, Mac addresses, Serial Numbers, Account Numbers, Service, Category details, and more. Other databases also have billing addresses, phone numbers etc. for hundreds of thousands of TWC customers.
Bob Diachenko, chief communications officer, MacKeeper Security Center:
Cyber criminals and state-sponsored espionage is a real threat to major corporations, businesses of all sizes, and individuals. We see more and more examples of how bad actors use leaked or hacked data for a range of crimes or other unethical purposes. The bottom line is that data is valuable and there will always be someone looking for it. Improperly securing data is just as bad if not worse because it was preventable. In this case engineers accidentally leaked not only customer and partner data but also internal credentials that criminals could have easily used to monitor or access company's network and infrastructure.
The threat and risk
Cyber criminals and state-sponsored espionage is a real threat to major corporations, businesses of all sizes, and individuals. We see more and more examples of how bad actors use leaked or hacked data for a range of crimes or other unethical purposes. One example is the infamous Yahoo email breach and the belief that it was used to identify dissidents, trade secrets, and gather other sensitive data. The bottom line is that data is valuable and there will always be someone looking for it. Improperly securing data is just as bad if not worse because it was preventable. BroadSoft accidentally leaked not only customer and partner data but also internal credentials that criminals could have easily used to monitor or access their network and infrastructure.
The MacKeeper Security Research Center has downloaded the contents of the repository for verification purposes and it is unclear if anyone else has had access to the data.
As we continue to see more and more cloud leaks appear it reminds us that companies large and small must conduct regular audits to secure their data. Misconfiguration of cloud-based storage repositories that allow public or semi-public access can result in a devastating data leak that requires no hacking or password. The MacKeeper Security Team is dedicated to identifying threats and vulnerabilities and helping to secure them or bring attention that will help make data more secure online.
Alex Kernishniuk, VP of strategic alliances, MacKeeper:
Unfortunately, oftentimes developers like to simplify their life or quickly resolve some technical problems and grant public read access to the buckets There are at least two tools already provided by AWS to detect this critical security flaw with your S3 buckets - AWS Trusted Advisor and AWS Config.
UPDATE: The article has been updated to reflect that no evidence except a similar report name was identified to mention AMC among affected companies.
Mexican tourist tax refund company leaks customer records
Have you been to Mexico in the last year as a tourist and applied for a tax refund on the money you spent while shopping there? If you have, chances are your passport, credit card, or other identification might have been leaked online. The MacKeeper Security Research Center has discovered a misconfigured database with nearly half a million customer files that were left publically accessible. These tourists traveled from around the world to enjoy Mexico’s beaches, warm weather, historical sites, or cities and had their private data exposed in the process.
The database appears to be connected with MoneyBack, a leading provider of tax refund (value-added tax refund or sales tax refund) services for international travelers in Mexico.
MoneybBack is part of Prorsus Capital SAPI de CV, a Mexican Investment Fund. The most dangerous aspect of this discovery is the massive amount of data totaling more than 400GB.
How MoneyBack works
They have created a network of affiliate stores who offer the tax refund as a type of discount to lower the final purchase price of certain goods tourists buy. These refunds would make sense for luxury jewelry, gold, and diamonds that cost many thousands of dollars. According to MoneyBack’s General Director Danielle Van Der Kwartel “International travelers can receive an 8.9% refund of the total amount they spend when shopping at any of the 6,500 MONEYBACK affiliated stores”. They also claim to provide service in more than 98% of Mexico’s air and maritime points of departure and have 55 offices, airport booths, cruise ports, and shopping mall locations.
MoneyBack works closely with travel agents by providing training on its services to help them promote the tax refunds to their clients traveling to Mexico. It seems to be a profitable business and encourages shoppers to spend more but are customers really saving that much money? Some credit card companies charge 3% foreign transaction fees and it is unclear what fees MoneyBack charges customers or the travel agent commissions. There are some complaints online about the bureaucracy of the Mexican Government taking up to 6 months to disburse refunds. Are the savings worth it?
How the leak happened
During a routine security audit, MacKeeper Security Researchers discovered a misconfigured CouchDB that allowed public access to the data via browser. Those who follow cybersecurity news may remember that in early 2017 10% of CouchDB servers were victims of ransomware because of the same misconfiguration. Although MoneyBack is based in Mexico the hosting and IP address is located in the United States. The database was publically accessible and required no password protection or other authentication to view or download MoneyBack’s entire repository.
Bob Diachenko, chief security communications officer, MacKeeper Security Center:
Improperly storing digital data is one of the biggest threats facing consumers, businesses, and governments. Data can be backed up, copied, reproduced very easily and one small mistake could expose everything as this case has demonstrated. It would seem logical that organizations would have multiple copies of production data in the event of some type of catastrophic event, ransomware, hacking or other threats. However, the same backups that provide a kind of “insurance policy” when recovering from data loss is also the same culprit that makes a data leak more likely. The reality is that the more copies an organization has of their data the higher the likelihood that a leak will occur.
What was leaked and who is affected?
Researchers identified passports from all over the world who used MoneyBack’s services. Among the top passports identified were citizens of the US, Canada, Argentina, Colombia, Italy, and many more. It appears to be every client that has used their services between 2016 and 2017.
- Over 300 GB+ database in size
- 455,038 Scanned Doccuments (Passports, IDs, Credit Cards, Travel Tickets & More)
- 88,623 unique passport numbers registered or scanned
Mexico has a booming tourism industry despite travel warnings to certain areas, a history of gang violence and kidnappings. It was estimated that the country welcomed a record 35 million international tourists in 2016. Many tourists who will be buying expensive items on their vacation likely love the idea that they can have a portion of the sales taxes returned, but is it worth having your data exposed online?
How Tax-Free Shopping in Mexico works?
Tax-free sounds great but their are some restrictions. Tourists must spend at least 1200 pesos ($67 USD) on Mexican goods (this does not apply to services such as hotel stays and food expenses). Tourists must also enter and leave Mexico by sea or air. The minimum purchase per store is 1,200 pesos with electronic payment and cash purchases can not exceed 3,000 pesos ($168 USD). Another issue to consider is that you will have to file yourself with the bureaucracy Mexican Tax Authorities or give your personal information, credit card, and identification to a 3rd party company such as MoneyBack.
- Tourists need to shop at an affiliated store with “Tax Free shopping”.
- They must ask for an official invoice with the stores tax id number
- When tourists leave the airport or by ship there are Tax Free booths, they can visit one of the offices, or several other ways to submit their tax paperwork.
- Although they estimate 40 days to receive a refund complaints state up to 6 months.
The danger of this data?
Alex Kernishniuk, VP of strategic alliances, MacKeeper:
Cyber criminals could have all of the information they would need to commit identity fraud or use the hundreds of thousands of credit card numbers that were in the database. This is once again a warning to companies or organizations who collect sensitive data to take every possible step to ensure that proper data security measures are used. Time and time again simple human errors that could be easily avoided expose sensitive data on the internet. It is unclear if anyone other than security researchers accessed the data or how MoneyBack will notify their customers around the globe that their data has been exposed.
***
Attention - Portions of this article may be used for publication if properly referenced and credit is given to MacKeeper Security Center.
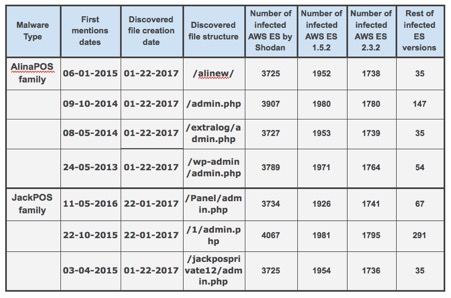
MacKeeper Research Center discovers massive Elasticsearch infected malware Botnet
One of our recent researches was focused on the publicly accessible Elasticsearch (ES) nodes and we discovered suspicious indices names that did not have any relations to Elasticsearch file structure.
Among the many “red flags” some of the file names referenced to AlinaPOS and JackPOS malware. These are the type of POS (Point-of-Sale) malware that attempts to scrape credit card details using a range of different techniques. As an example of how this malware is so effective, JackPOS attempts to trick the system that it is java or a java utility. It can copy itself directly into the %APPDATA% directory or into a java based sub-directory inside %APPDATA%. JackPOS uses the MAC address as a bot ID and can even encode the stolen credit card data to go undetected as it is extracted. This malware first became widespread in 2012, but it is still effective today and available for sale online.
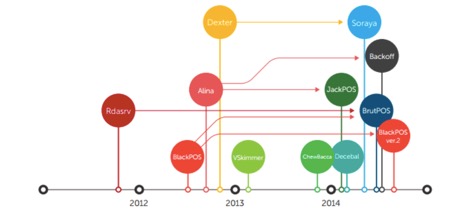
In 2014 the family tree looked as follows:
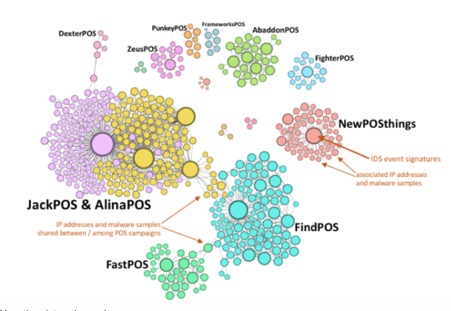
Today the picture is much worse and much more widespread.
Despite some security warnings and industry-related news, It appears POS malware has been out of the headlines for a while, but the danger is still there for millions of cardholders. Kromtech researchers started looking for any updates about that specific type of malware and the status of files being distributed on unsuspecting servers. What surprised researchers is that there are new and updated versions of the malware that are currently for sale to anyone.
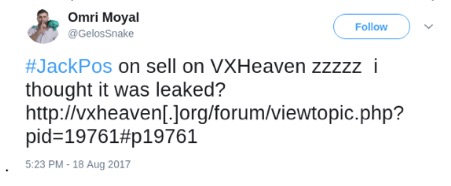
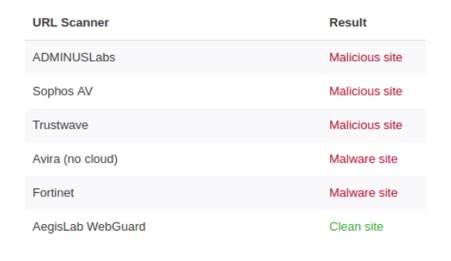
At Cybercrime tracker https://cybercrime-tracker.net/index.php?search=alina we've seen new samples of these malware types and low detection rate by the most popular AntiVirus engine (tested with VirusTotal).
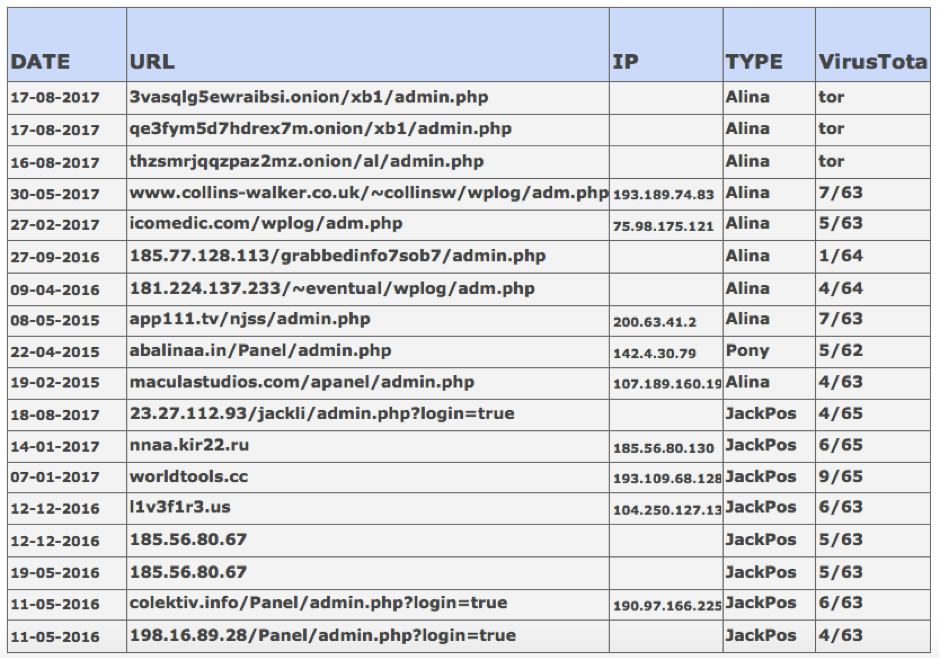
Even for the relatively old C&C servers hosting sites (Command and Control servers), there is not enough information to flag the real risks. The VirusTotal URL Scanner indicated that only 6 of the antivirus engines and website scanners out of the 65 available were able to identify the new versions of the POS Malware.
Why did it happen?
The lack of authentication allowed the installation of malware on the Elasticsearch servers. The public configuration allows the possibility of cyber criminals to manage the whole system with full administrative privileges. Once the malware is in place criminals could remotely access the resources of the server and even launch a code execution to steal or completely destroy any saved data the server contains.
In our case, a bunch of AWS-hosted Elasticsearch instances was under attack for malicious use. Moreover, every infected ES Server became a part of a bigger POS Botnet with Command and Control (C&C) functionality for POS (point-of-sale) malware clients. These clients are collecting, encrypting and transferring credit card information stolen from POS terminals, RAM memory or infected Windows machines.
Old C&C interface used by POS malware is displayed below (taken from https://blog.malwaremustdie.org/2014/02/cyber-intelligence-jackpos-behind-screen.html)
We checked with Shodan (our commonly used IoT search engine which returns service banners with meta-data of the server) how many systems on the internet have similar signs of infection.
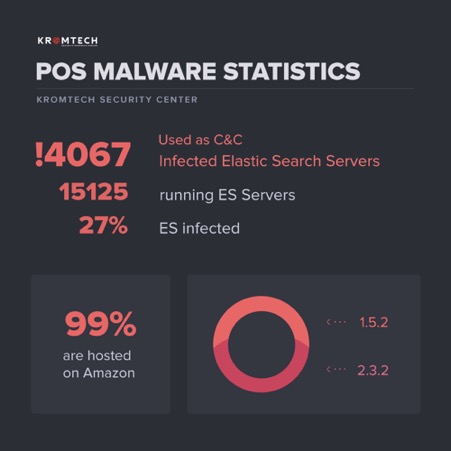
As of today, there are nearly 4000 infected Elasticsearch servers, and about 99% of them are hosted on Amazon.
Why are nearly all of the Elasticsearch servers hosted by Amazon Web Services?
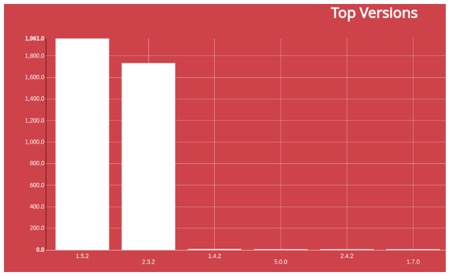
Amazon Web Services provides customers with a free T2 micro (EC2 / Elastic Compute Cloud) instance with up to 10 Gb of disk space. These T2 instances are designed for operations that don't use the full CPU for general purpose workloads, such as web servers, developer environments, and small databases. The problem is that on the T2 micro, you can set only versions 1.5.2 and 2.3.2.
The Amazon hosting platform gives users the possibility to configure the Elasticsearch cluster just in few clicks, but usually, people skip all security configuration during the quick installation process. This is where a simple mistake can have big repercussions and in this case it did by exposing a massive amount of sensitive data.
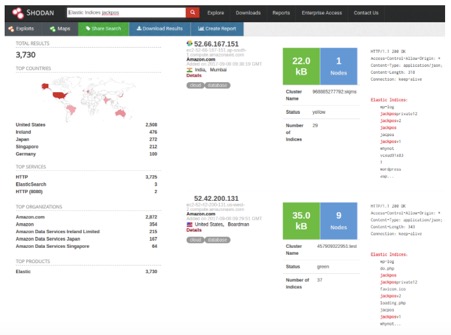
Kromtech Security Researchers discovered similar file structures on Shodan.io for Elastic Search Services. Then they compared the modification time of suspicious files on these infected Elasticsearch Servers and made some logical conclusions:
- There are different packages of C&C malware, i.e. servers were infected multiple times
- Different packages can be related to different Botnets (because POS malware was seen selling not only on Darknet but on public domains as well)
- There is a lot of servers infected, for the same packages on different servers the time of infection could be different due to periodical scans and Botnets network expansion
- Nearly 99% of infected servers are hosted on Amazon Web Services
- 52% of infected servers run Elastic Search 1.5.2 version, 47% - 2.3.2 version, and 1% for other versions.
- Recent infections were made at the end of August 2017
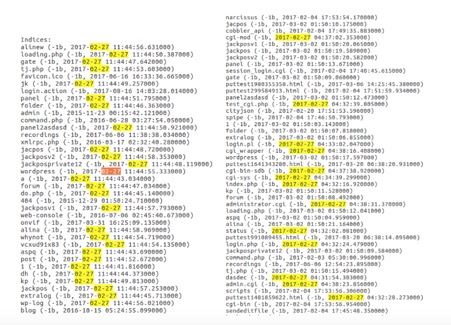
The following table represents Kromtech Security Centers findings and the attack distribution of the infected AWS instances through vulnerabilities in the Elasticsearch Server and the Amazon security configuration:
Kromtech Security Center highly recommend you to take the following actions required for effective incident response:
- Check your log files on all servers in your infrastructure
- Check connections and traffic
- Make a snapshot/backup of all running systems
- Extract samples of malware and provide it to us for further analysis (security@kromtech.com)
- Reinstall all compromised systems, otherwise, you need to clean up all suspicious processes, check your systems with antivirus and also monitor your system during next 3 months for any anomaly connection
- Install latest Elastic patch or completely reinstall it
- Close all non-used ports from external access, or white-list only trusted IPs
Here are also some recommendations from Elastic Search site that need to be taken: https://www.elastic.co/what-is/elastic-stack-security
Vulnerability types in ELK
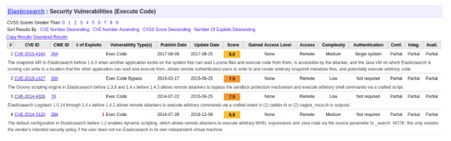
Infographics for infected ES Servers:
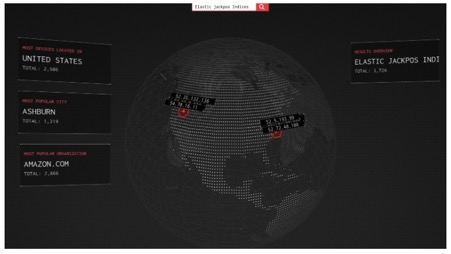
The following graph represents vulnerable versions of Elasticsearch Servers used by attackers to distribute and control malware through vulnerable or misconfigured Elasticsearch Servers:
Auto tracking company leaks hundreds of thousands of records online
Have you ever heard of the term SVR? The “SVR” stands for “stolen vehicle records.” The MacKeeper Security Center has discovered a repository connected to the vehicle recovery device and monitoring company SVR Tracking. And this is what we’ll cover in this article.
In 2017 researchers found an Amazon AWS S3 bucket (public cloud-based storage) that happened to be misconfigured and left publically available. This breach exposed information on their customers and the reseller network, along with the device attached to the cars.
The repository we mentioned above had records of over half of a million logins and passwords, emails, IMEIs of GPS devices, VIN (vehicle identification number), and other information collected on their devices like customers or auto dealerships. What’s curious, the exposed database also had the data where the tracking unit was hidden precisely in the car.
What was discovered?
A Backup Folder called “accounts” held the record of 540,642 ID numbers, information about accounts including many plates and VINs, hashed passwords, IMEI numbers, emails, and more.
- 71,996 (02/2016)
- 64,948 (01/2016)
- 58,334 (12/2015
- 53,297 (11/2016
- 51,939 (10/2016)
- 41,018 (9/2016)
- 35,608 (8/2016)
- 31,960 (7/2016)
- 31,054 (6/2016)
- 29,144 (5/2016)
- 38,960 (4/2016)
- 32,384 (3/2016)
- 116 GB of Hourly Backups
- 8.5 GB of Daily Backups from 2017
- 339 documents called “logs” that contained data from a wider date range of 2015-2017 UpdateAllVehicleImages, SynchVehicleStatus, maintenance records.
- Document with information on the 427 dealerships that use their tracking information.
The number of devices could be much higher because many of the resellers or clients had multiple devices for tracking.
If you feel at risk, learn how to act after a data breach occurred.
Detailed tracking 24hrs a day, even if the car is not stolen or missing
This software tracks wherever the vehicle has been during the last 120 days. What is even more terrifying is that all of the visited places are marked and pinpointed to the map. In addition to that, there’s a feature showing anyone who has login credentials the best locations and stops where the car has been. The so-called “recovery mode” pinpoints every 2 minutes and creates zone notifications. With a 99% successful recovery rate being a great result, user logins and passwords for hundreds of unsuspecting drivers are leaked online?
According to their website “The SVR Tracking service enables lot owners to locate and recover their vehicles with live, real-time tracking and provides stop verification, enabling them to determine potential locations for their vehicles. Alerts will flag owners, making them aware of events of interest. The application dashboard provides real-time graphs and detailed vehicle data suited to tighter control and accurate measurements of vehicle activity.”
One can access the software on any device connected to the internet device (desktop, laptop, mobile, or tablet). The satellite locates the tracking unit and sends the data to its servers using the GPRS Data Network. Think of the potential dangers if cybercriminals find out a car’s location by just logging in with the publicly available credentials and stealing that vehicle?
Shortly after sending the responsible disclosure note, the bucket has been secured, however, no words from the company.
In 2012 there were an estimated 721,053 automobiles stolen in the United States.
Verizon wireless employee exposed confidential data online
On September 20th, MacKeeper Security researchers discovered publicly accessible Amazon AWS S3 bucket containing around 100MB of data attributing to internal Verizon Wireless system called DVS (Distributed Vision Services).
DVS is the middleware and centralized environment for all of Verizon Wireless (the cellular arm of VZ) front-end applications, used to retrieve and update the billing data.
Although no customers data are involved in this data leak, we were able to see files and data named "VZ Confidential" and "Verizon Confidential", some of which contained usernames, passwords and these credentials could have easily allowed access to other parts of Verizon's internal network and infrastructure.
Another folder contained 129 Outlook messages with internal communications within Verizon Wireless domain, again, with production logs, server architecture description, passwords and login credentials.
Upon analyzing the content of the repository, we identified the alleged owner of the bucket and sent responsible notification email on September 21st. Shortly after that, online archive has been took down and it has been later confirmed that the bucket was self-owned by Verizon Wireless engineer and it did not belong or managed by Verizon.
What the repository contained:
- Admin user info that could potentially allow access to other parts of the network
- Command notes, logs including
- B2B payment server names and info
- Internal PowerPoints showing VZ infrastructure, with server IPs, marked as “Verizon Wireless Confidential and Proprietary information”
- Global router hosts
- 129 saved Outlook messages with access info and internal communications
Damage control or denial?
Verizon had $126.0 billion in consolidated revenues in 2016 and it seems like they would not leave the keys to the front door of their data servers or network out for anyone? In the corporate world any bad news can affect stock prices or other aspects of the business. However, if these files were not sensitive, why not make this information open-source or publically available? access to production logs, scripts, instructions, and administrative credentials to protected areas of Verizon's internal infrastructure.
In the aftermath of the Equifax data leak it is easy to be skeptical considering that they waited 5 months to inform regulators or the public. Then remember that Equifax executives sold off stock before the price drop. It is not out of line to consider when someone has been approached with a data leak that they might deny it. As security researchers we often hear that data was not sensitive or that it was production or test data, when it is clearly not.
Bob Diachenko, chief security communications officer, MacKeeper:
“Our primary goal is to notify and secure the data not dispute if they are being honest or not. As more and more data leaks occur it makes consumers, and average individuals more vulnerable online. We believe that companies have an obligation to not only take the proper security measures but also protect the data their employee collect and store”.
Alex Kernishniuk, VP of strategic alliances, MacKeeper:
"An improperly configured S3 can lead to viewing, uploading, modifying, or deleting S3 objects by third parties. To prevent S3 data loss or exposure and unexpected charges on your AWS bill, you need to grant access only to trusted entities by implementing the appropriate access policies recommended in this conformity rule. Bruteforce tools are already scanning all possible bucket names, analyzing configurations letter by letter and getting closer to your information every minute."
Report: virtual keyboard developer leaked 31 million client records
The MacKeeper team has discovered a massive amount of customer files leaked online and publically available. Researchers were able to access the data and details of 31,293,959 users. The misconfigured MongoDB database appears to belong to Ai.Type a Tel Aviv-based startup that designs and develops a personalized keyboard for mobile phones and tablets for both Android and iOS devices.
Ai.Type was founded in 2010 and According to their site, their flagship product for Android was downloaded about 40 million times from the Google Play store and the numbers of downloads and user bases are rapidly growing. They plan to integrate Matching Bots as a user types their conversation and that their Ai type keyboard will soon offer a “Bots Discovery Platform” Via Keyboard. There was also a notice of a name change from Ai.Type to Bots Matching Mobile Keyboard in the coming year.
Giving up data for personalized services and apps
Consumers give up more data than ever before in exchange for using services or applications. The scary part is that companies collect and use their personal data in ways they may not know. The concept is where people willing to provide their digital in exchange for free or lower-priced services or products. A study from the Annenberg School for Communication at the University of Pennsylvania concluded that a majority of Americans do not think the trade-off of their data for personalized services is a fair deal.
Once that data is gone users have little to no knowledge of what is done with their personal data. Why would a keyboard and emoji application need to gather the entire data of the user’s phone or tablet? Based on the leaked database they appear to collect everything from contacts to keystrokes. This is a shocking amount of information on their users who assume they are getting a simple keyboard application.
How the data leak occurred and what it contained
Ai.Type accidentally exposed their entire 577GB Mongo-hosted database to anyone with an internet connection. This also exposed just how much data they access and how they obtain a treasure trove of data that average users do not expect to be extracted from their phone or tablet.
MongoDB is a common platform used by many well-known companies and organizations to store data, but a simple misconfiguration could allow the database to be easily exposed online. One flaw is that the default settings of a MongoDB database would allow anyone with an internet connection to browse the databases, download them, or even worst-case scenario to even delete the data stored on them.
Summary of what the database contained:
Client registration
Client files that included the personal details of 31,293,959 users who installed ai.type virtual keyboard. This is highly sensitive and identifiable information.
For example:
phone number, the full name of the owner, device name and model, mobile network name, SMS number, screen resolution, user languages enabled, Android version, IMSI number (international mobile subscriber identity used for interconnection), IMEI number (a unique number given to every single mobile phone), emails associated with the phone, country of residence, links and the information associated with the social media profiles (birthdate, title, emails etc.) and photo (links to Google+, Facebook etc.), IP (if available), location details (long/lat).
Phonebook and contact records
6,435,813 records that contained data collected from users’ contact books, including names (as entered originally) and phone numbers, in total more than 373 million records scraped from registered users’ phones, which include all their contacts saved/synced on linked Google account.
Additionally, user data from a folder titled ‘old database’ that contained 753,456 records were also available.
There was a range of other statistics like the most popular users’ Google queries for different regions. Data like average messages per day, words per message, age of users, words_per_day': 0.0, 'word_per_session and a detailed look at their customers.
To avoid the negative consequences of such events, learn how to secure yourself against data breaches.
Ashley Madison's private picture went viral
Ashley Madison, the online cheating site that was hacked two years ago, is still exposing its users' data. This time, it is because of poor technical and logical implementations.
As a result, approximately 64% of Ashley Madison (AM) private, often explicit, pictures are accessible. This access can often lead to trivial deanonymization of users who had an assumption of privacy and opens new avenues for blackmail, especially when combined with last year's leak of names and addresses.
Let's look at how "Sarah" and "Jim," two hypothetical users on AM, can have their privacy broken.
AM has two types of pictures, public and private, neither of which are required. Public pictures are viewable by any AM user. Private pictures are secured by a "key." Sarah can send her key to Jim so he can see her pictures. Jim can request Sarah's key, requiring her explicit approval. Sarah can also revoke Jim's key, restricting his access.
This structure makes sense but, two issues open the door to problems:
- By default, AM will automatically share Sarah's key with Jim if he shares his key with her.
- Pictures can be accessed, without authentication, by directly accessing its URL
To protect her privacy, Sarah created a generic username, unlike any others she uses and made all of her pictures private. She has denied two key requests because the people did not seem trustworthy. Jim skipped the request to Sarah and simply sent her his key. By default, AM will automatically give Jim Sarah's key.
That's right, Jim can now see all of Sarah's private pictures, rated (aka explicit) and non-rated.
How does this happen? When adding a picture, the box to share your private pictures is already checked. If you keep this box checked, it will apply the same setting to additional pictures of the same type (public or private).
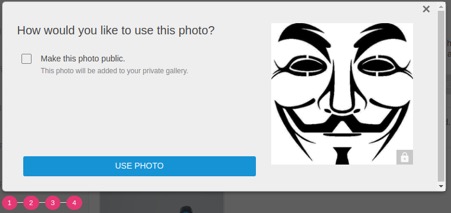
There are two issues with this implementation. First, few understand the implications nor think through the way it could be exploited. Second, as Steve Gibson would put it, is the "tyranny of the default." As he explains it, "whatever the default settings are, most of the time that's what they end up being forever." People will simply click through the options, leaving them as recommended. The only way to change this configuration is to go deep into the settings page.
Let's go back to our metaphorical users. Sarah will at least get an email saying that she received Jim's key and can go to AM to validate the interaction and revoke the key Jim was given.
During testing, less than 1% of users revoked their key after it had been given. It is our assumption that this means that most users do not understand the impact of this policy. We believe it is far less likely that users who go through the effort to distinguish between public and private photos are ok with any random AM user seeing their private pictures.
Those that revoked their key, access is now denied.
Actually, that's not 100% true. Once Jim is granted access to Sarah's pictures, he is able to see the link, e.g. https://photo-cdn.ashleymadison.com/[picture_name]. Not only can he access the picture, with this link, anyone can access the picture without authentication, AM user or not. While the picture URL is too long to brute-force (32 characters), AM's reliance on "security through obscurity" opened the door to persistent access to users' private pictures, even after AM was told to deny someone access.
Data leakage
In order to prove the validity of this issue, we wrote a program to iterate through all IDs, aka profile numbers, (0-99,999,999) and gave a private key to a random sample of users that had private pictures. Based on this random sampling:
- 26% of users had private pictures
- 64% of users accounts that had private pictures automatically returned their key
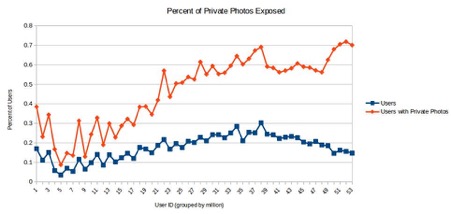
AM's parent company, Ruby, also controls two other sites, Established Men and Cougar Life. Both of these sites also have automatic key exchange and require no authentication to directly access picture URLs; however, they at least force a user to pick if they want to enable sharing by default instead of defaulting it on and requiring a user to uncheck the box.
Implications
The implications of these issues are many.
- At the core, pictures that AM users entrusted them to securely store are exposed.
- Users can be victims of blackmail. AM users were blackmailed last year, after a leak of users' email addresses and names and addresses of those who used credit cards. Some people used "anonymous" email addresses and never used their credit card, protecting them from that leak. Now, with a high likelihood of access to their private pictures, a new subset of users are exposed to the possibility of blackmail.
- These, now accessible, pictures can be trivially linked to people by combining them with last year's dump of email addresses and names with this access by matching profile numbers and usernames.
- Exposed private pictures can facilitate deanonymization. Tools like Google Image Search or TinEye can search the internet to try to find the same picture, including on social media sites like Facebook, Instagram, and Twitter. This sites often have your real name, connecting your AM account to your identity. Some users also include their first name in their username, e.g. Sarah1234. With your name, age, location, and now pictures, it can be easy to search Facebook or Google for a matching profile.
Recommendations
- Remove automatic pictures sharing or adjust its logic. In our opinion, Sarah should have to explicitly give Jim permission to her private pictures. AM's parent company does not agree and sees the automatic key exchange as an intended feature.
- Limit key exchanges. If you limit how many keys a user can send out, you decrease the speed with which they can exploit automatic key sharing across the user base. AM's parent company has completed this.
- Restrict right-click functionality in the web page. While this is not perfect, it at least raises the difficulty in saving or stealing private pictures.
- Add authentication to all AM photos. Having pictures accessible, unauthenticated, is negligent.
- Only allow 1 user account per email address. We were able to create 7 user accounts under the same email address, which lowered the difficulty of conducting the scan of user accounts.
For more recommendations on keeping your data secure on the web, check out these tips on how to protect your privacy online.
Report: cybercriminals steal voter database of the State of California
If there is one thing that the 2016 US election has taught us it is that the entire electoral process needs to be revamped and a more uniform secure process. There have been several high-profile leaks of voter data in recent months but in this case the entire voting population of California has had their information taken by cyber criminals.
In early December, MacKeeper security researchers discovered an unprotected instance of MongoDB database that appear to have contained voter data. The database named 'cool_db' contained two collections and was available for anybody with Internet connection to view and/or edit.
One was a manually crafted set of voter registration data for a local district and the other appeared to contain the entire state of California with 19,264,123 records, all open for public access.
According to the LA Times California had 18.2 million registered voters in 2016 so this would logically be a complete list of their records.
MacKeeper researchers were unable to identify the owner of the database or conduct a detailed analysis due to the fact that the database has been deleted by cyber criminals and there is a ransom note demanding 0.2 bitcoin ($2,325.01 at the time of discovery).
We were able to analyze the stats data we saw in our report (metadata on total number of records, uptime, names of the collection etc.), as well as 20-records sample extracted from the database shortly before it has been wiped out and ransom note appeared.
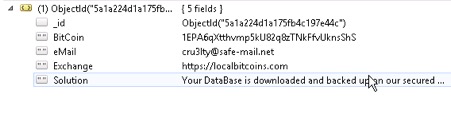
Ransomware and stolen data
In January 2017 a 27k or roughly a quarter of MongoDB databases left open to the internet were hit by ransomware and again in September 2017 three groups of hackers wiped out an estimated 26,000 MongoDB databases. The cyber criminals demanded that the owners of those databases pay around $650 USD in the cryptocurrency BitCoin to regain their data. It is still unknown just how that stolen data was used or how many people paid to have it returned, and if it was even returned after the cybercriminals received the money.
Back in January MacKeeper Security came up with the initiative to help those who suffered an attack. Read more about last year 'massacre' here.
It is unclear who exactly compiled the database in question or the ownership, but researchers believe that this could have been a political action committee or a specific campaign based on the unofficial title of the repository ("cool_db”), but this is only a suspicion. Political firms assist campaigns in building voter profiles. This information of California voters is governed by state law that dictates what kind of information can be released, and for what purposes.
The danger of a state voter database leak
In this case security researchers were able to bring awareness to millions of California citizens that their data was not only publicly leaked online, but also that cyber criminals have stolen it for ransom. State voter registration databases store detailed information on each registered voter in the state, as required by federal law.
The criminals used ransomware to wipe out the voter data and likely backed it up on a server making it even riskier. Once in the hands of cyber criminals, this voter data could end up for sale on the “Dark Web”. If this were an official database, deleting parts of that data could affect someones voting process.
What the database contained?
The 4GB collection contained data structured with the following rows:
- City:
- Zip:
- StreetType:
- LastName:
- HouseFractionNumber
- RegistrationMethodCode
- State: CA
- Phone4Exchng:
- MailingState: CA
- Email:
- Phone3Area:
- Phone3NumPart:
- Status: A
- Phone4Area:
- StreetName:
- FirstName:
- StreetDirSuffix:
- RegistrantId:
- Phone1NumPart:
- UnitType:
- Phone2NumPart:
- VoterStatusReasonCodeDesc: Voter Requested
- Precinct:
- PrecinctNumber:
- PlaceOfBirth:
- Phone1Exchng:
- AddressNumberSuffix:
- ExtractDate: 2017-05-31
- Language: ENG
- Dob:
- Gender:
- MailingCountry:
- AssistanceRequestFlag
- MailingCity:
- MiddleName:
- AddressNumber:
- StreetDirPrefix:
- RegistrationDate:
- PartyCode:
- Phone1Area:
- Suffix:
- NonStandardAddress:
- Phone4NumPart:
- CountyCode:
- MailingAdd3:
- MailingAdd2:
- MailingAdd1:
- UnitNumber:
- Phone2Exchng:
- NamePrefix:
- _id: ObjectId
- MailingZip5:
- Phone2Area:
The “Extract Date” is most likely is the indicator of when the database has been compiled. It appears to have been created on May 31st, 2017.
The purpose of the second much larger collection in the database, named ‘22GB appears to be the complete California voter registration records. It contains a massive 409,449,416 records in total.
The format and information in the document titled “22GB”
- ExtractDate: '2017-05-31',
- 'District':
- 'RegistrantId':
- 'CountyCode':,
- 'DistrictName':
- '_id': ObjectId
Bob Diachenko, head of communications, MacKeeper Security Center:
This is a massive amount of data and a wake up call for millions citizens of California who have done nothing more than fulfil the civic duty to vote. This discovery highlights how a simple human error of failing to enact the basic security measures can result in a serious risk to stored data. The MongoDB was left publically available and was later discovered by cyber criminals who seemed to steal the data, which origin is still unknown.
Here are the transactions for the wallet in the ransom note
https://www.blockchain.com/btc/address/1EPA6qXtthvmp5kU82q8zTNkFfvUknsShS
The database has been taken down since the initial discovery. Secretary of State of California was aware of the leak and "was looking into it", however, at the time of publication we did not receive any official statement.
Read more guides: